The Mist IoT Assurance cloud service streamlines IT operations while securing network connections for headless IoT and BYOD devices. It uses Multi Pre-Shared Key (MPSK) or Private Pre-Shared Key (PPSK) as new types of identity and policy vectors to provide a simple yet comprehensive way to onboard client devices without relying on client MAC addresses.
Key Features
MAC-less client device onboarding
- No need to associate a particular PSK with a client MAC address ahead of time
- Automatically avoids challenges associated with MAC randomization
PSK Life Cycle Management
- Ability to create, rotate and auto-expire PSKs
- In case a single PSK is compromised, it is simple to identity the blast radius, revoke the PSK without affecting other clients
Dynamic traffic engineering
- Assign VLAN to a given PSK
- Ability to assign a Role to a PSK for dynamic per-user WxLAN policies
Personal WLAN
- Creates virtual broadcast domain per PSK
User level accountability with PSK simplicity
- PSK Name is used as a new identity vector
- PSK Name is reported in the Mist UI
- PSK Name is reported in client-sessions or client-join webhooks for 3rd party audit integration
Automated PSK provisioning and rotation
- PSK Portals allow simple end-user onboarding via authenticated SSO login.
- Based on SSO login, an end-user email id is automatically associated with a generated PSK and used as an identity.
WLAN Configuration
Mist supports three methods of the Multi Pre-Shared Key (MPSK) lookup – Local and Cloud and RADIUS, each with its own benefits and use-cases.
Best Practices brief:
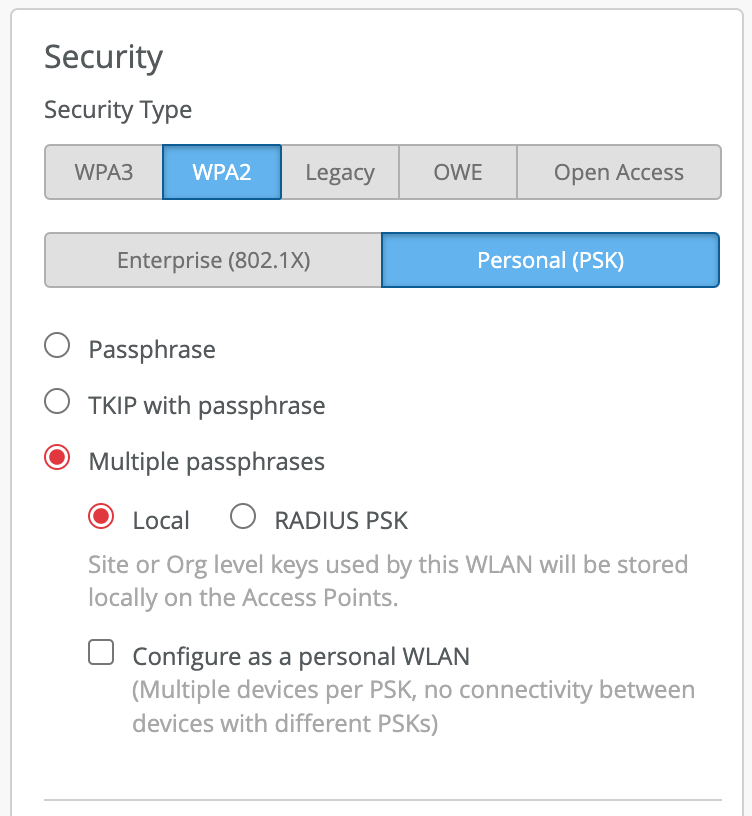
- Local mode is recommended for IoT use-cases (per device type PSK), low/mid-scale BYOD (no more than 5,000 total PSKs). With “Local” PSKs there is no dependency on the AP to Mist Cloud connectivity. Use for mission-critical networks. Local mode configuration:
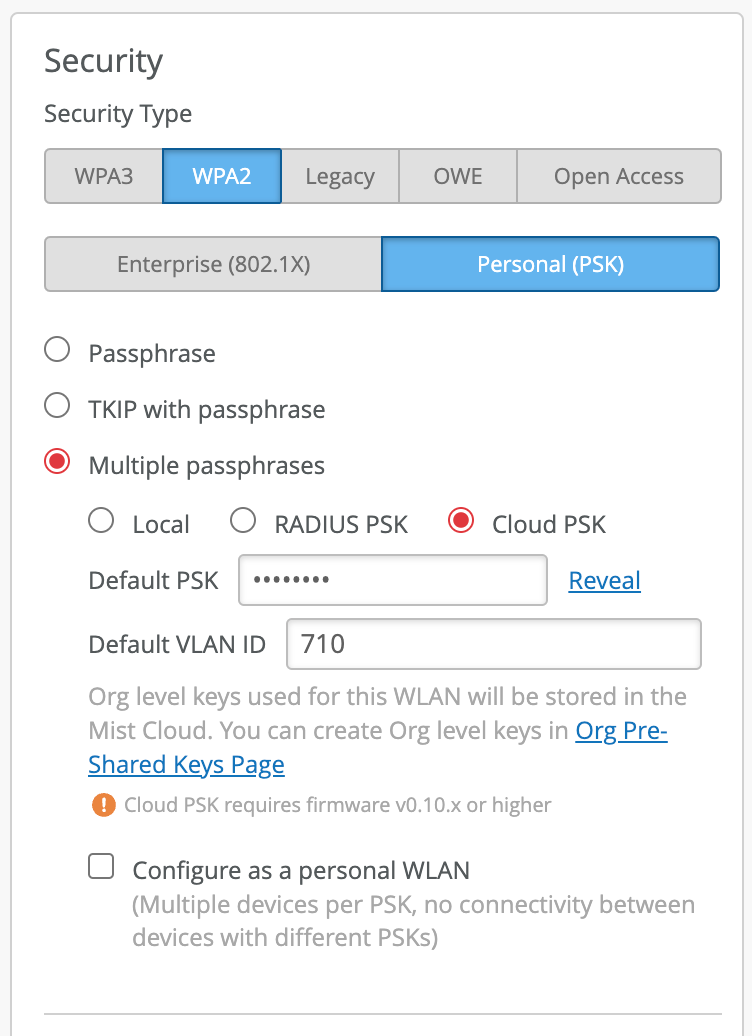
- Cloud mode is recommended for large scale BYOD type use-cases with per-user or per-device PSKs (>5000 PSKs).
- Cloud mode requires AP connectivity to the Mist Cloud
- In case AP is disconnected from the Mist Cloud, existing clients will stay connected and will be able to seamlessly roam to neighboring APs, however new clients will not be able to connect until AP to cloud connectivity is restored.
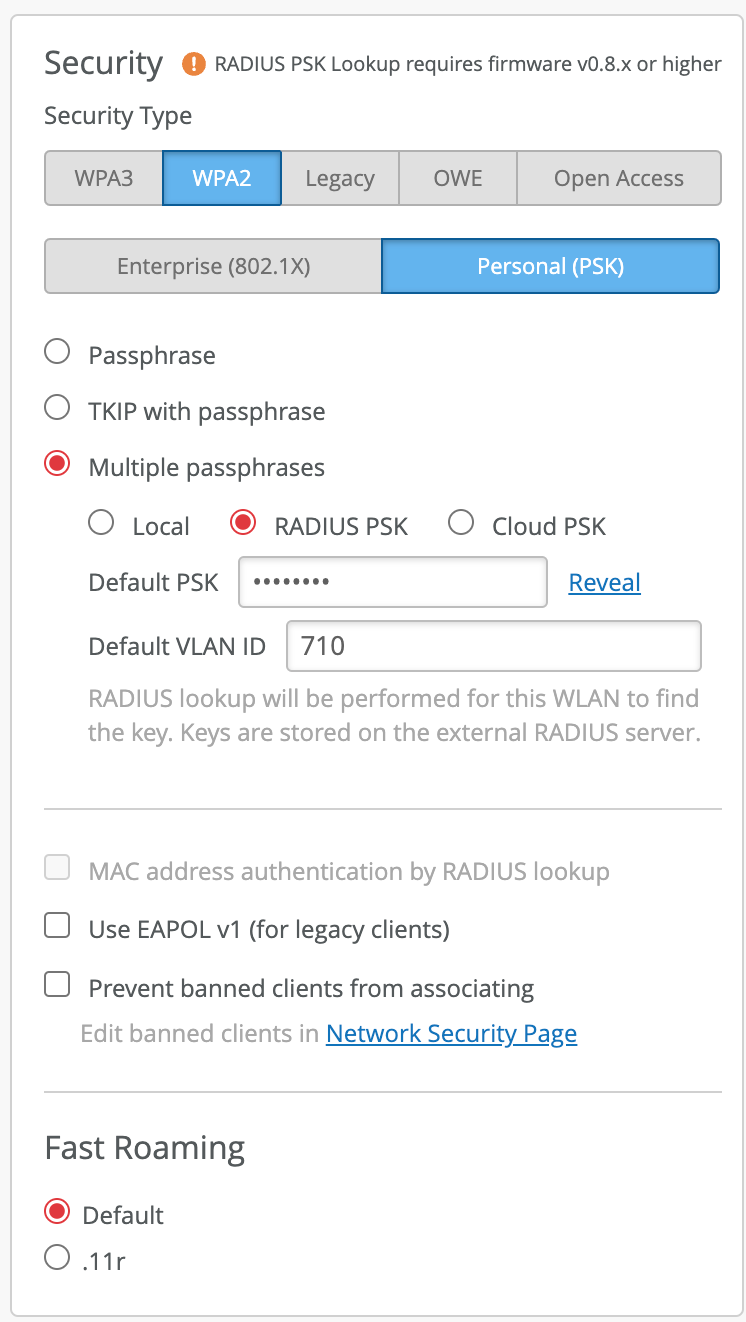
- RADIUS mode is recommended when integrating with a 3rd party PSK hosting service, such as Cisco ISE, Aruba Clearpass, RGnets, or ElevenWireless.
- In RADIUS mode AP does MAC Authentication request towards an external RADIUS server and expects RADIUS server to return the passphrase via Cisco AVPair. Refer to this document section 1.2.5 for more details. RADIUS mode configuration:
Site vs Org level Pre-Shared Keys
- When a PSK is created at a Site level (Site > Pre-Shared Keys), it will only be available within that site
- When a PSK is created at an Org level, it will be available across all Sites within the organization
- In “Local” mode, PSKs can be created either at the Site level and/or at the Org level.
- In “Cloud” mode, PSKs can only be created under Org level.
VLAN Assignment
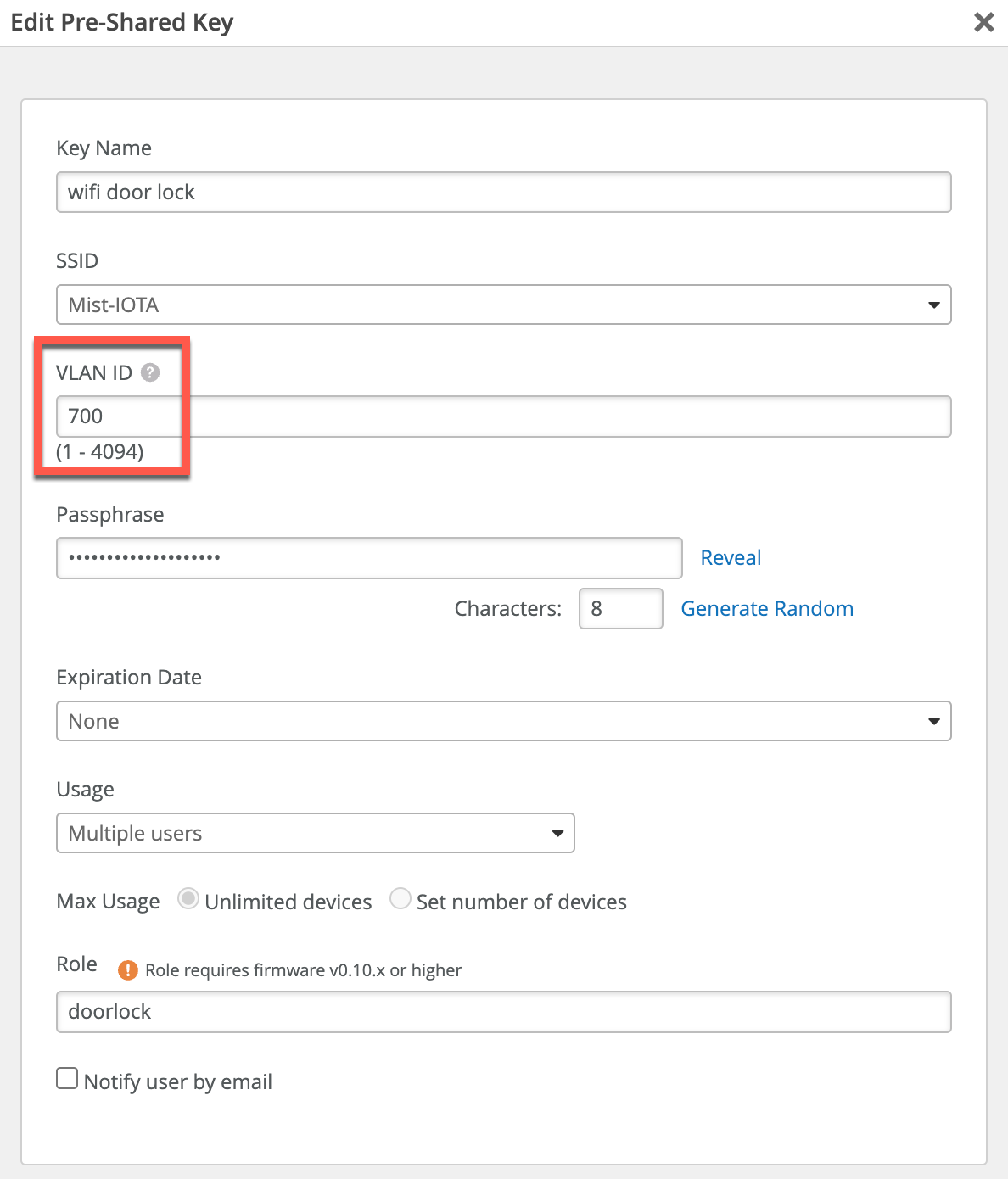
Each individual PSK can be assigned a VLAN for dynamic segmentation. This allows for simple dynamic segmentation within the same SSID based on the PSK identity.
For VLAN assignment to work, first make sure that a VLAN is part of the VLAN list under WLAN configuration:
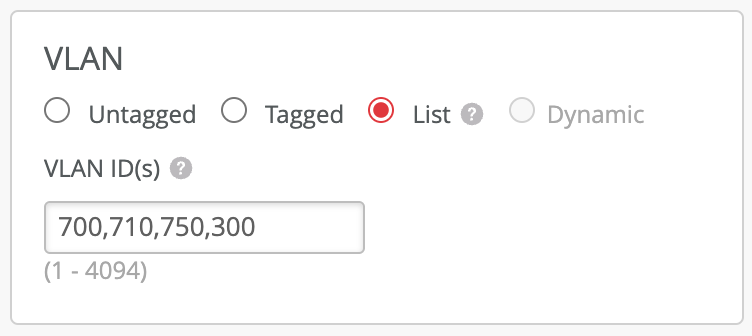
Then, configure required VLAN ID under Pre-Shared Key:
VLAN Assignment – dynamic tunneling with Mist Edge
In some cases, it is required to support both locally bridged as well as tunneled traffic to the Mist Edge within the same WLAN, for example to tunnel IoT client traffic to a Mist Edge in a regional POP closer to the IoT App server, while keeping BYOD client traffic local to the site. Mist handles this automatically based on the VLAN IDs.
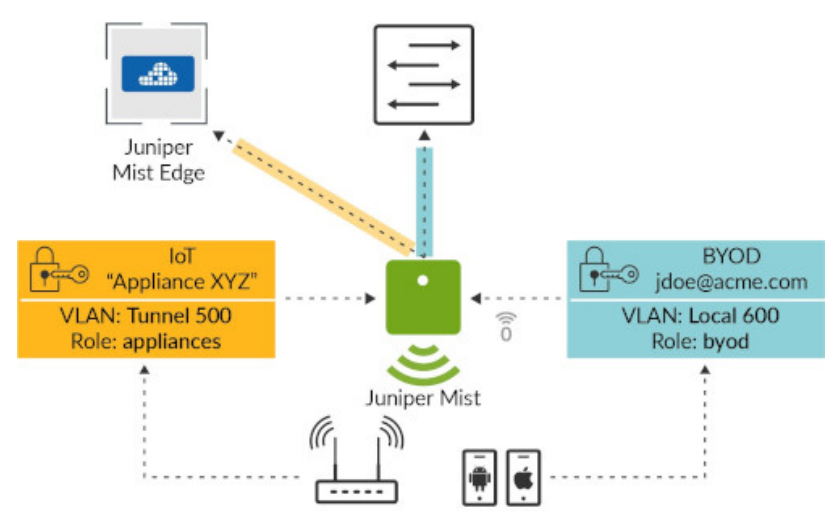
Let’s take above snippet as an example, where VLAN 500 is tunnelled to the Mist Edge, while VLAN 600 is locally bridged by the AP.
To achieve this, WLAN configuration must include both VLANs in the List:
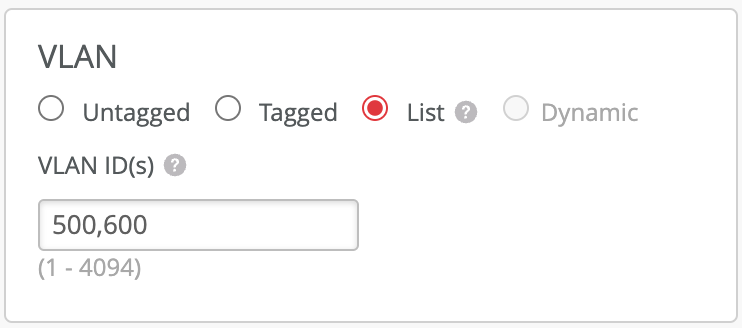
Mist Tunnel should include a tunnelled VLAN 500, but not the locally-bridged VLAN 600:
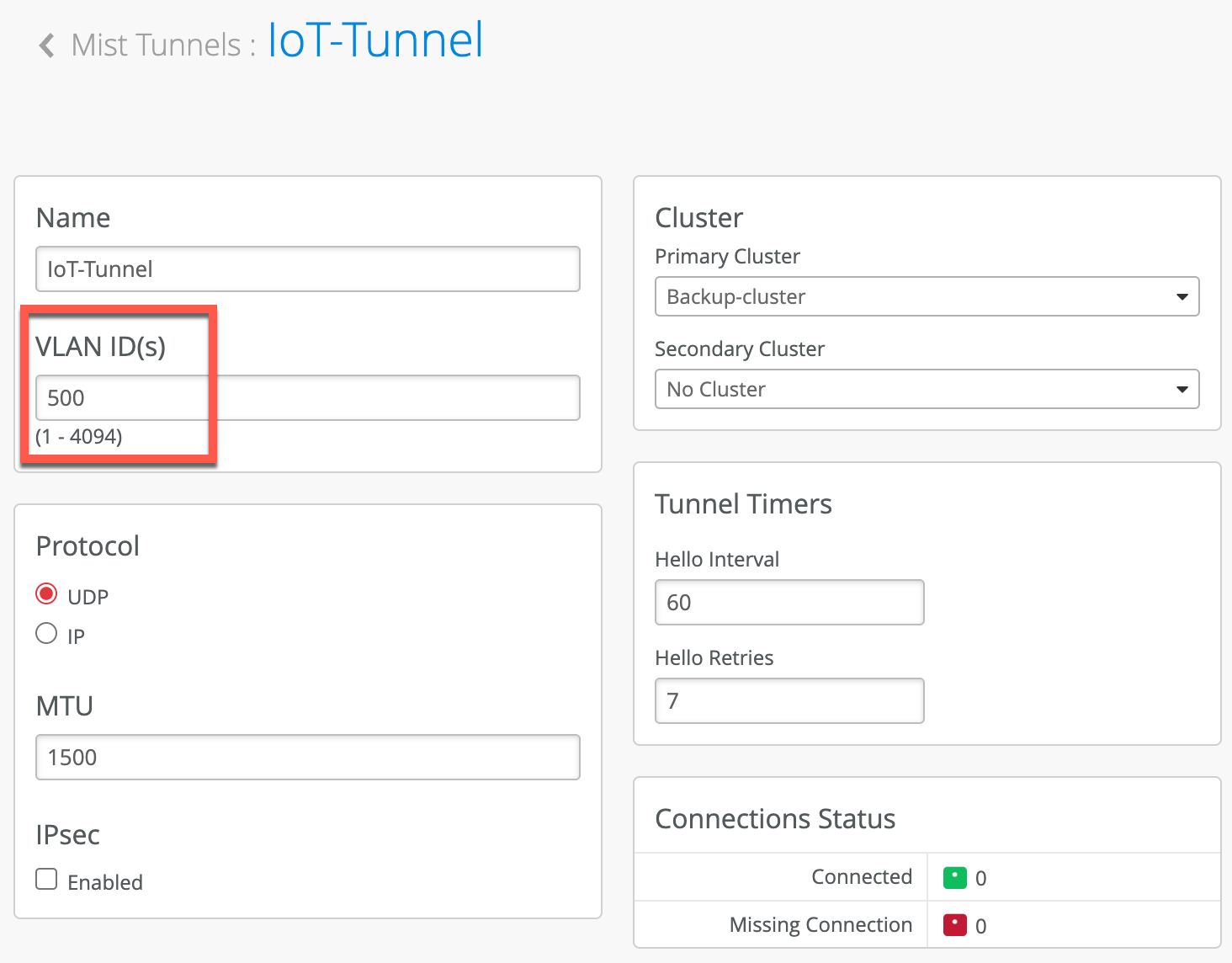
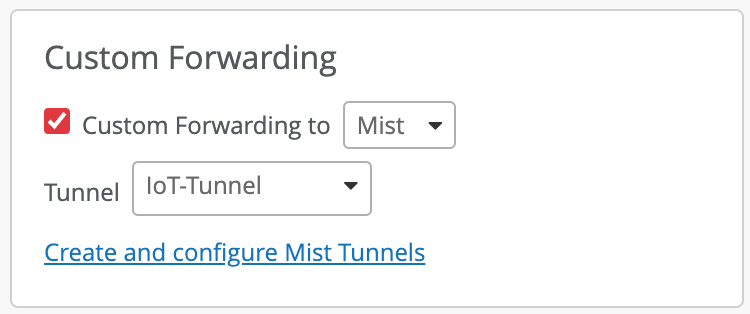
Subsequently the above Mist Tunnel must be mapped in the WLAN configuration under Custom Forwarding:
VLAN Assignment – per Site VLAN
In some cases clients using MPSK needs to be placed into different VLAN based on the Site they are in. For such scenarios, configure a single tagged VLAN as a variable:
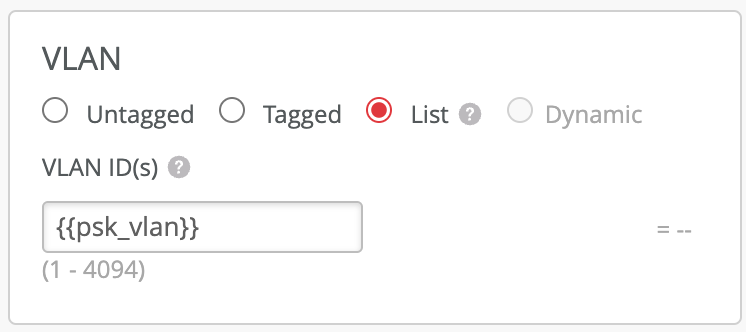
Leave VLAN field on the PSK config blank:
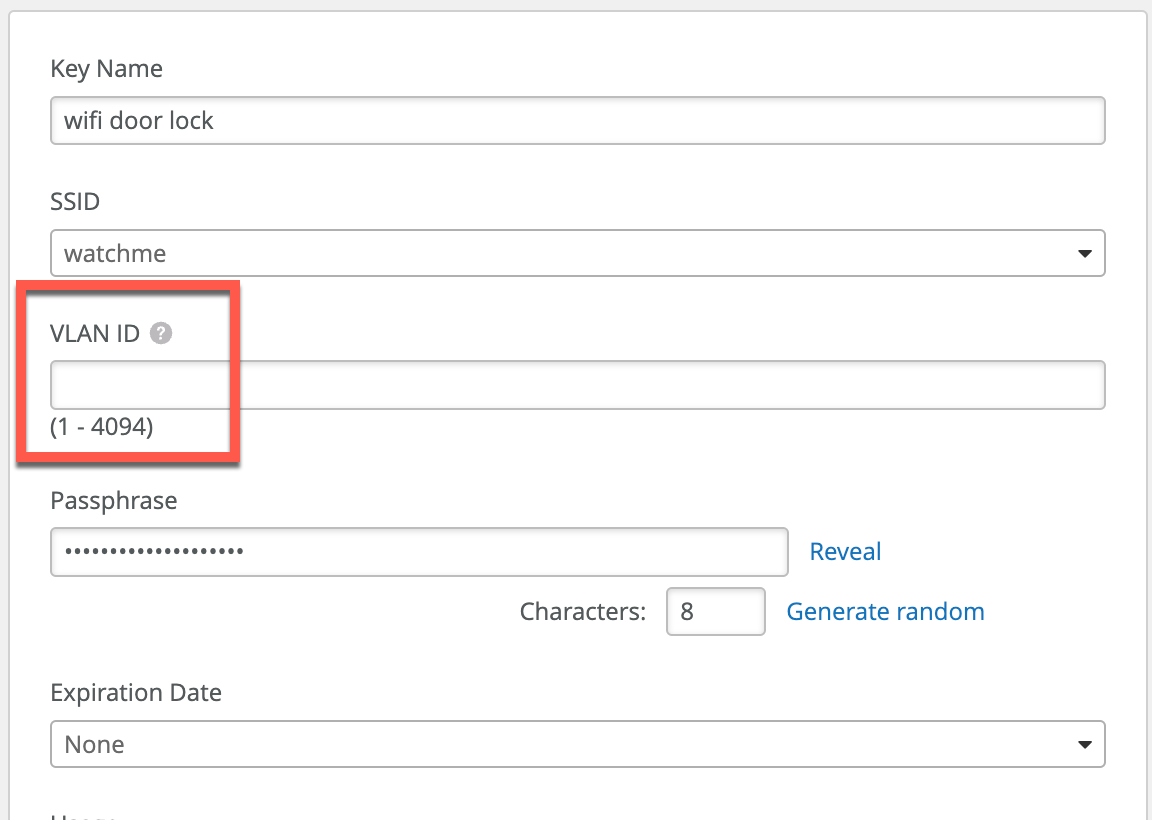
Then define a variable under Site Configuration:
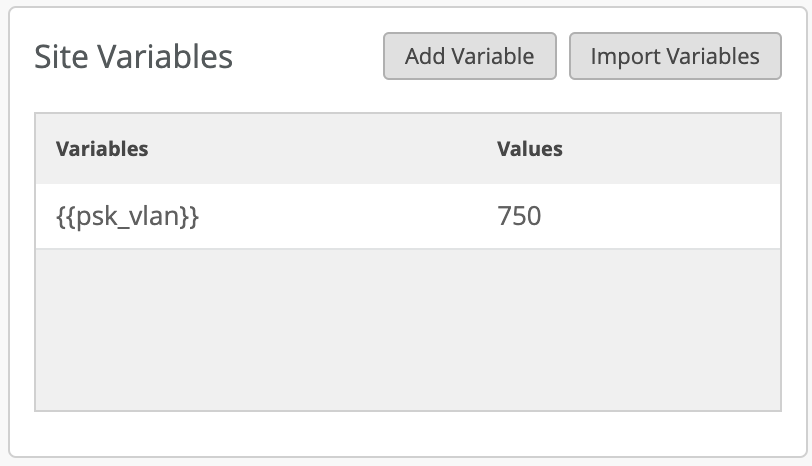
Leveraging Role in WxLAN policies
To expand segmentation options, in addition to a VLAN assignment, each PSK can be given a Role, which in turn can be assigned to a WxLAN network policy to further restrict a user or a device from accessing certain resources. A typical example would be to restrict an IoT device (e.g. a Wi-Fi camera) to only access network resources absolutely requires for that device type (e.g. Wi-Fi Camera feed server). Adding a Role to a PSK not only allows for granular control over network usage, but also protects the network in situations where a given PSK is compromised, since blast radius of such compromised credential would be very limited.
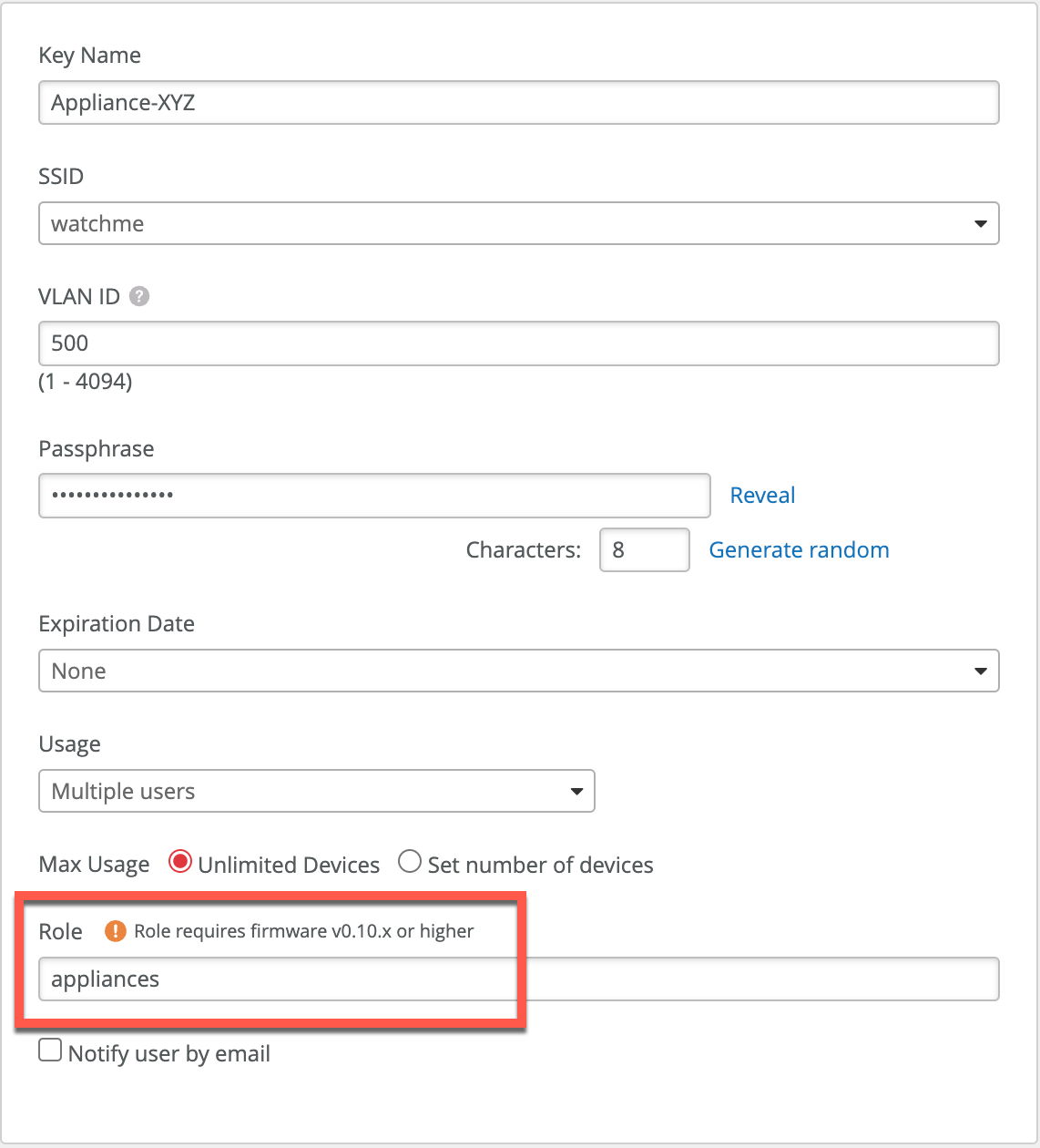
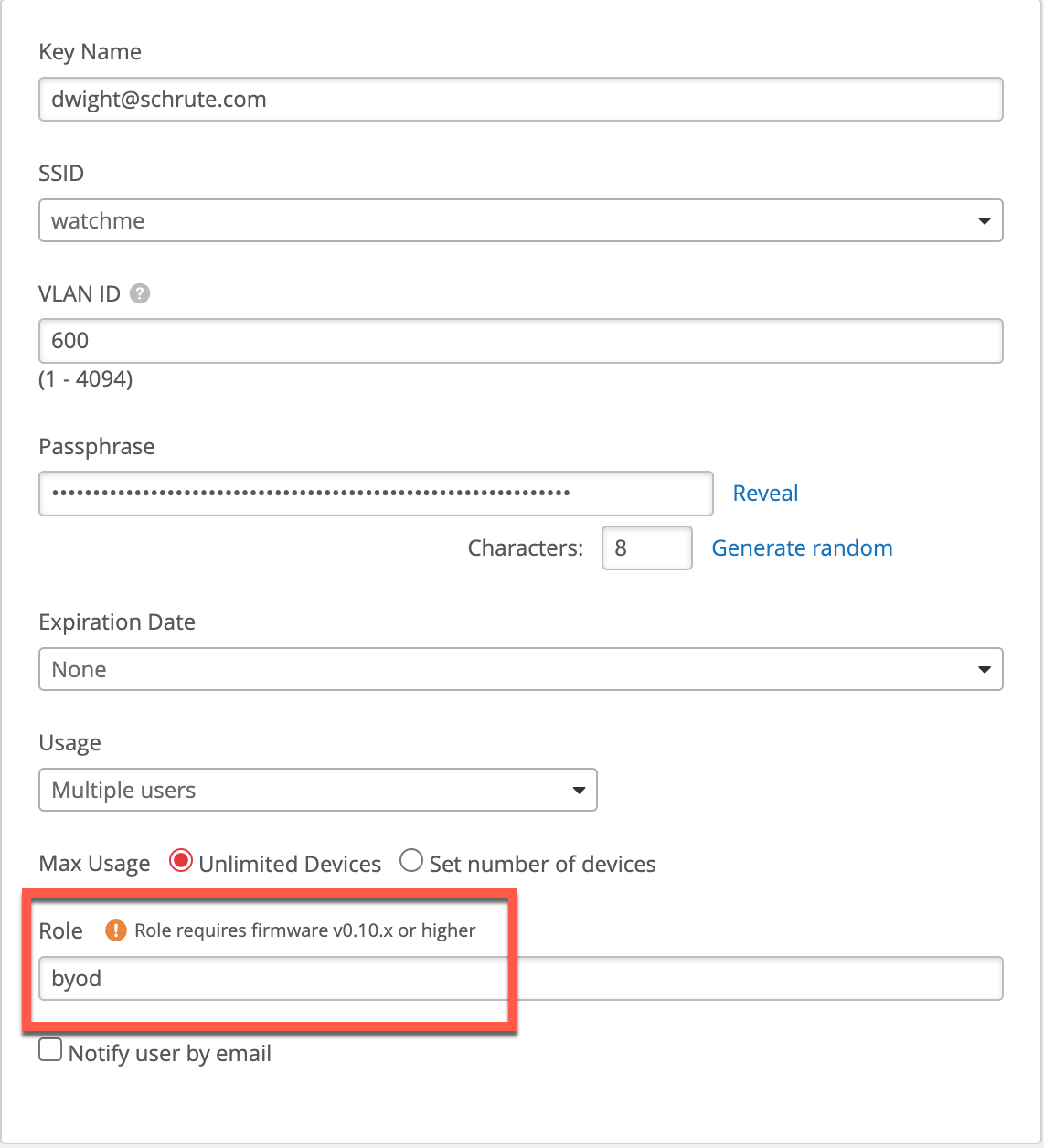
Let’s return to our previous example and see how we can leverage PSK Role and attach it to the WxLAN policy.

In the above example we assign Role ‘appliances’ to our IoT PSK, and we assign role ‘byod’ to an end-user PSK used to connect personal device to the network.
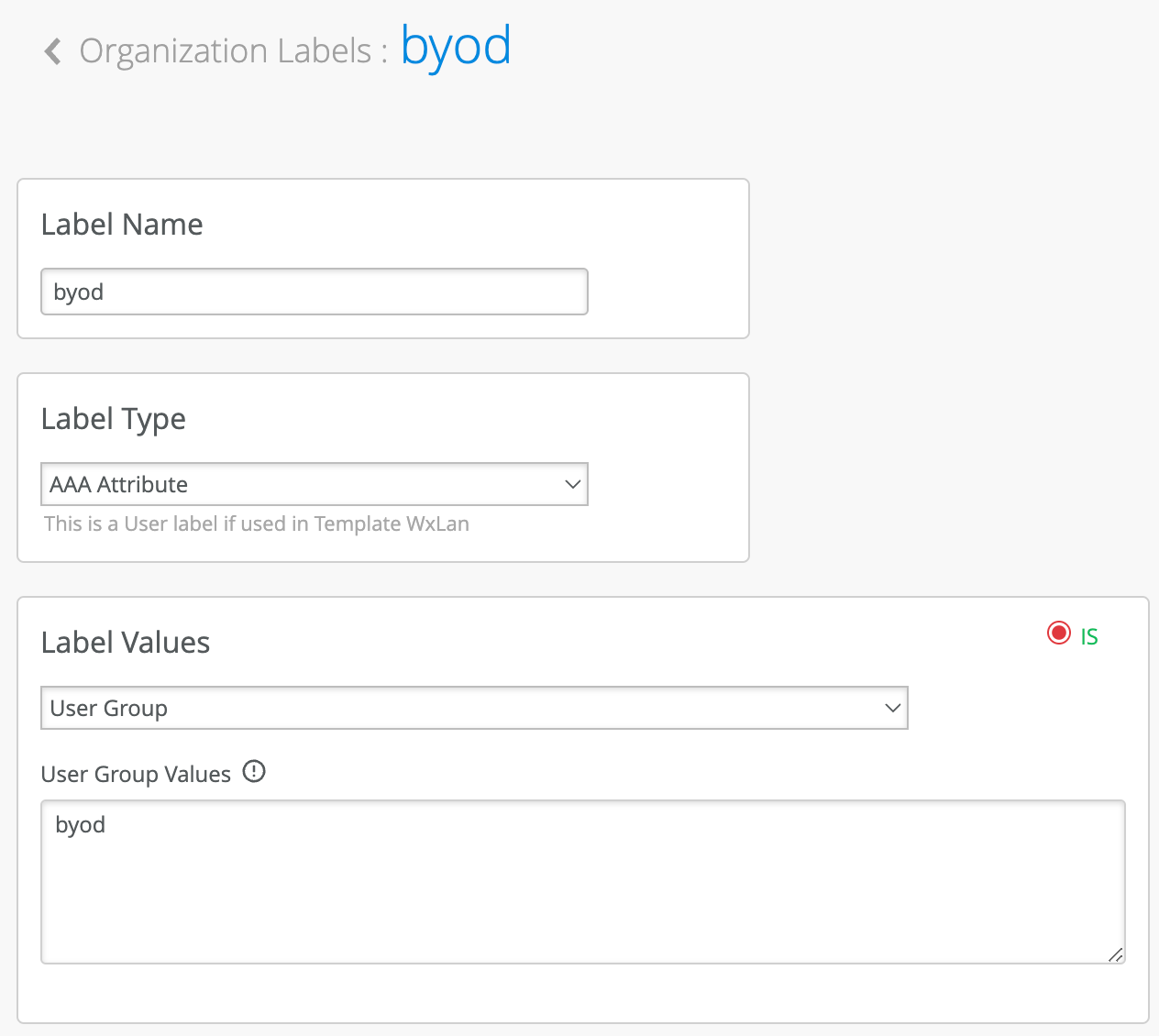
As a next step, we will create Org level labels to match on the roles above.
Navigate to Organization > Wireless > Labels and click Add Label
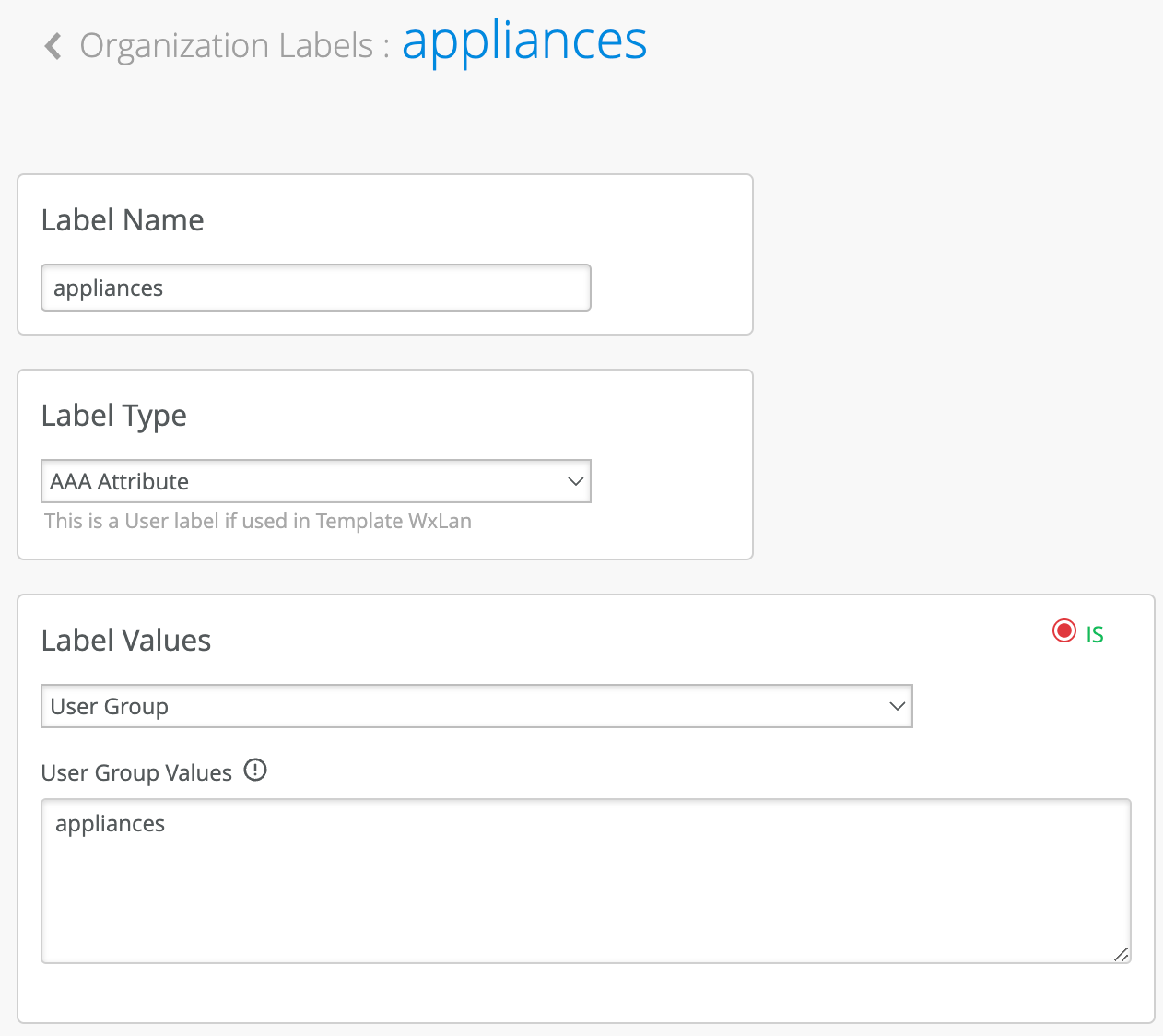
In our test scenario, we want to only allow BYOD devices to gain internet access, but restrict them from accessing internal company networks, while for IoT devices we want to restrict them to access only IoT application server and nothing else.
Under Org Labels page, create three more labels.
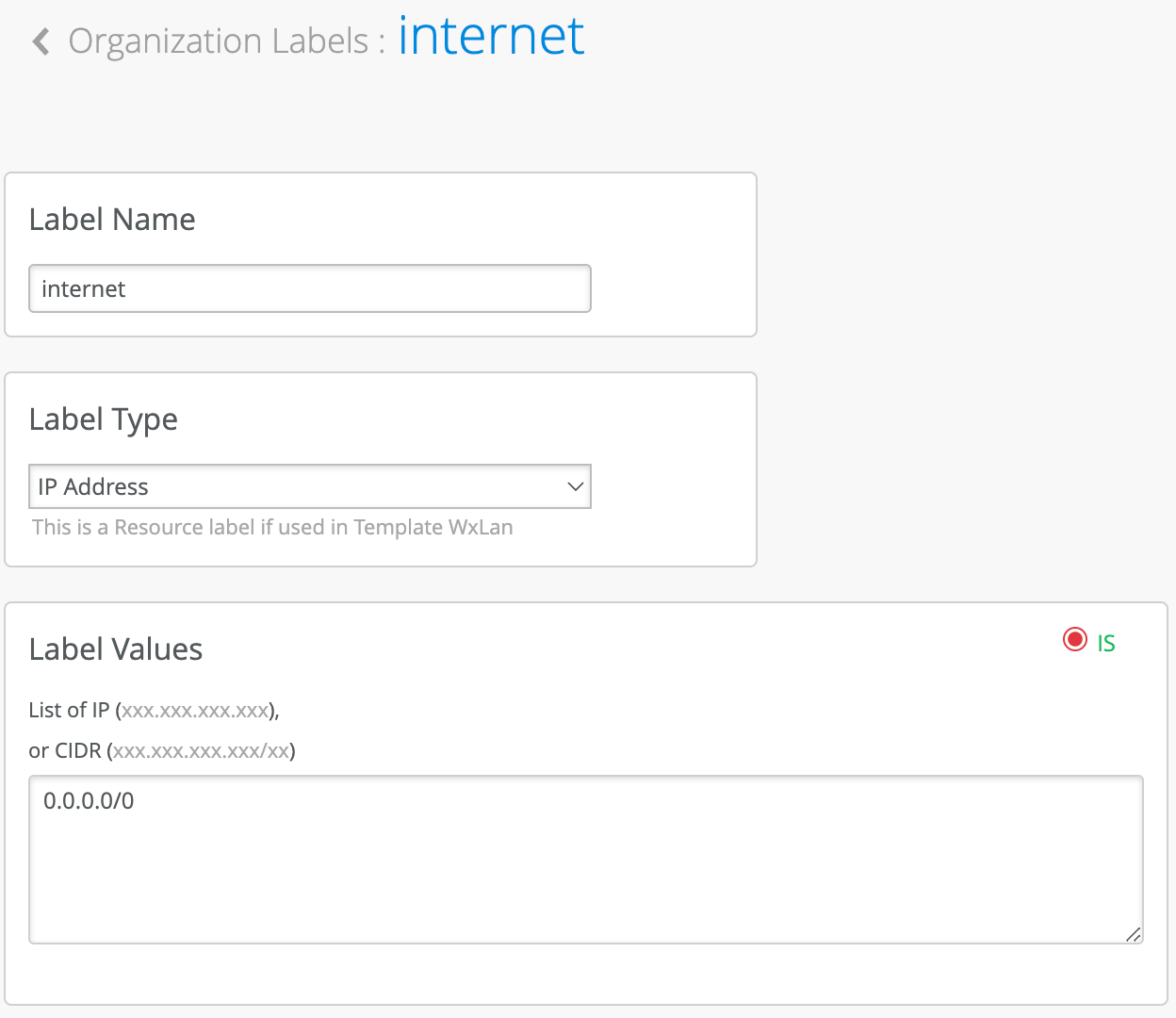
First label will be a wildcard matching on any IP address, i.e. 0.0.0.0/0, we will call it “internet.
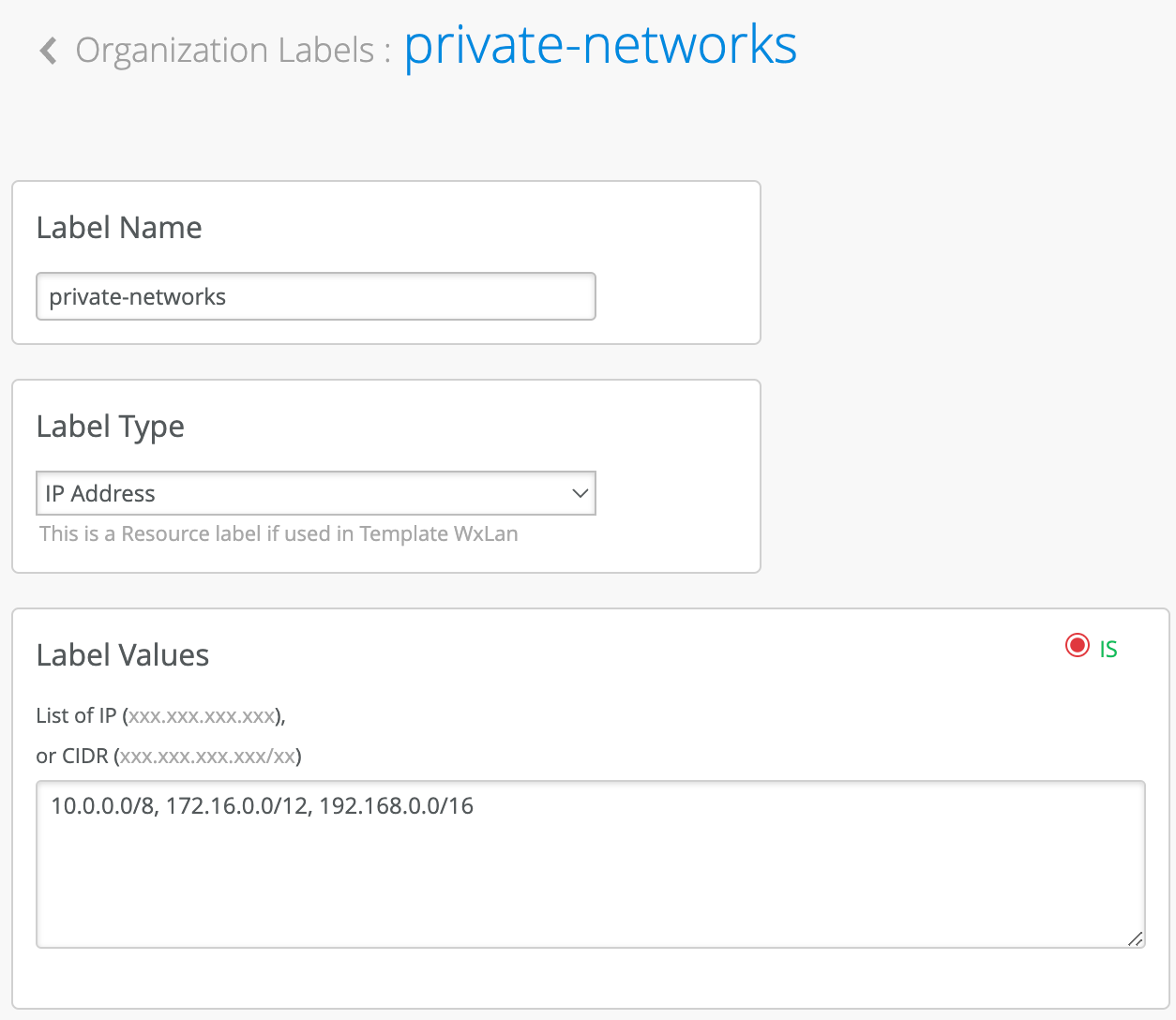
Second label will match on RFC1918 IP address space to indicate access to any private or internal company networks, we will call it “private-networks”.
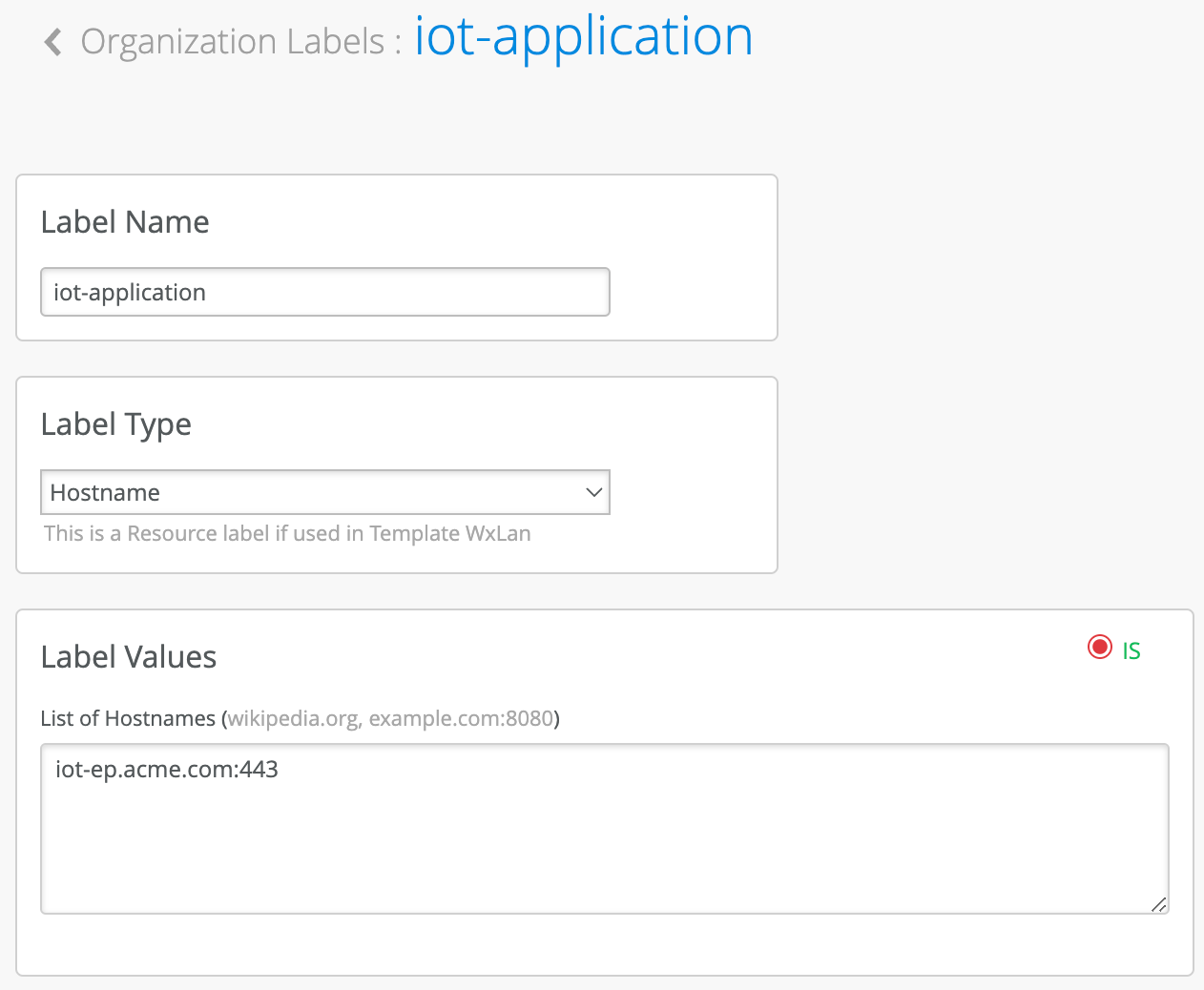
Finally, last label will match on a specific application FQDN and port, to indicate application that IoT devices need to access. We will call it “iot-application”.
Bringing this all together.
Navigate to Organization > Wireless > WLAN Templates > Select your Template.
Under Policy section we will create two rules. First rule will match on clients having “byod” role from a Pre-Shared Key, and it will allow access to internet, while blocking access to any internal networks. Second rule will match on clients with role “appliances” and it will only allow access to the iot application traffic and nothing else.
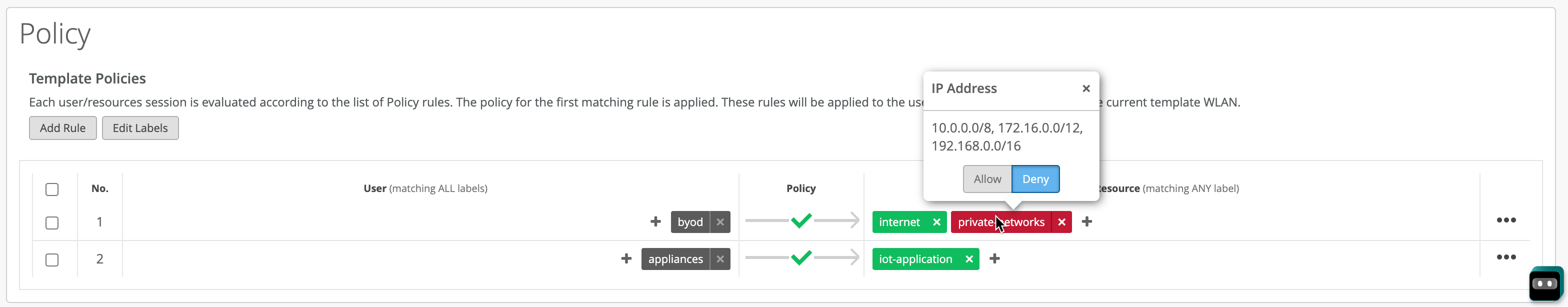
Few notes on the WxLAN policies that are of importance:
- DHCP and DNS traffic is automatically allowed, no need to mention it explicitly.
- Order of the resource labels on the right hand side is not important, the most specific label (e.g. specific IP > application > smaller subnet > larger subnet > wildcard) will be applied first automatically.
- WxLAN rules are enforced right at the Access Point for the egress traffic only. Ingress rules are automatically adjusted based on outgoing traffic.
Per PSK visibility and accountability
Since PSK Name is used as a new type of identity, Mist dashboard provides a tremendous amount of visibility on a per-user or per PSK basis at an Org level, which brings the level of visibility and accountability close to the traditional 802.1X Accounting.
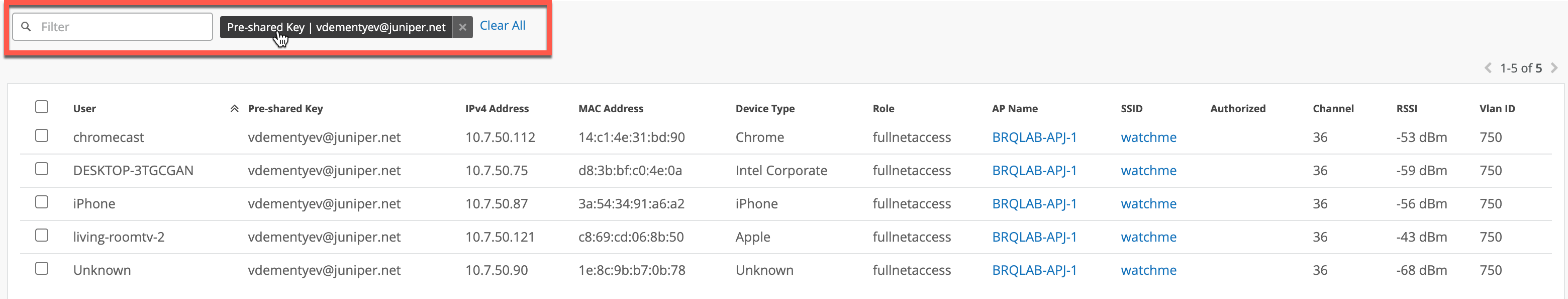
- Under Wi-Fi Clients page, if a client is connected to an MPSK WLAN, we will display the PSK name associated with the client and we can also allow searching for clients using PSK name in real-time:

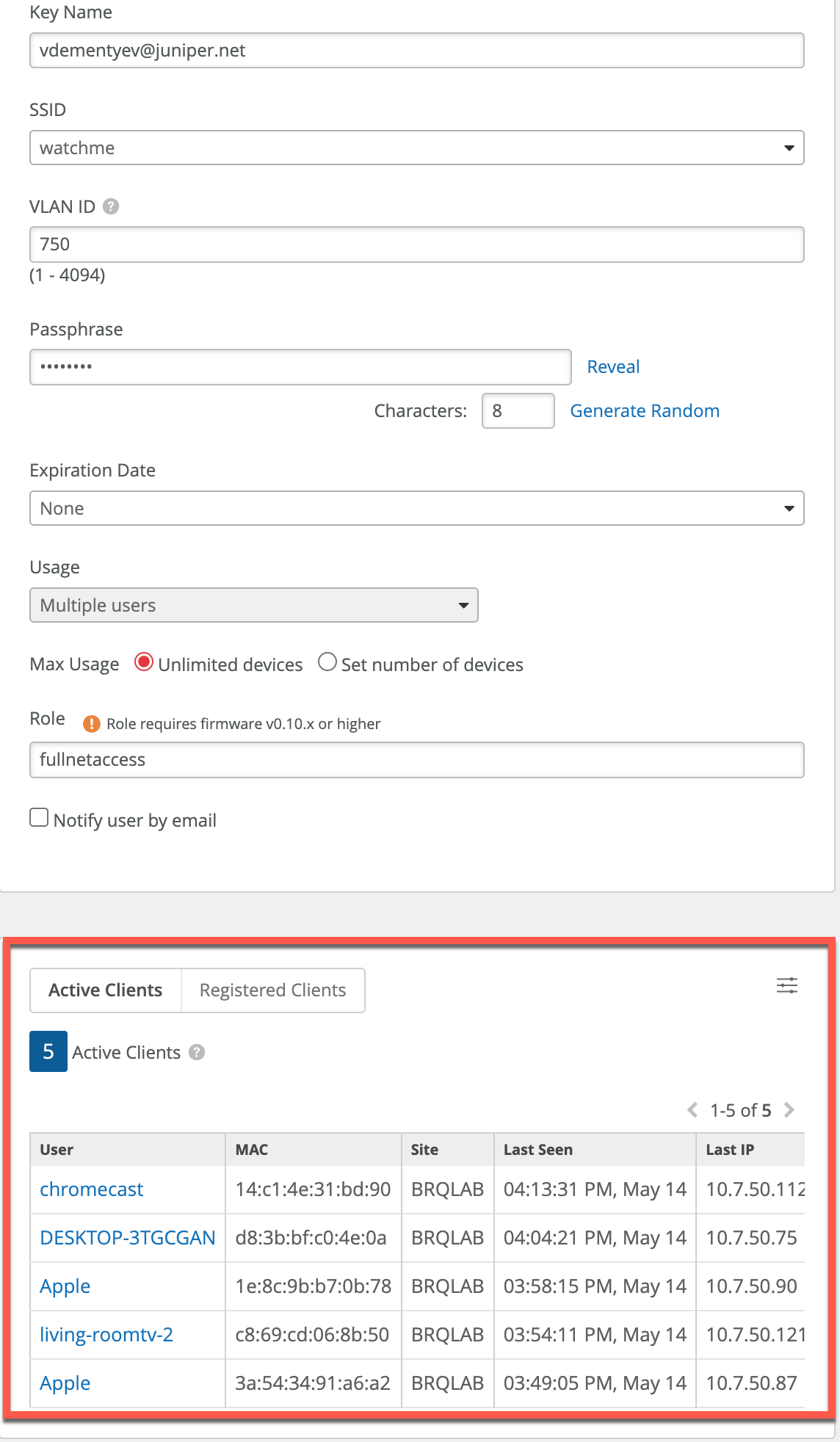
- Under Org Pre-Shared Keys page, searching for and selecting a specific key lists all the active clients as well as clients seen in the past 2 weeks at the Org level:
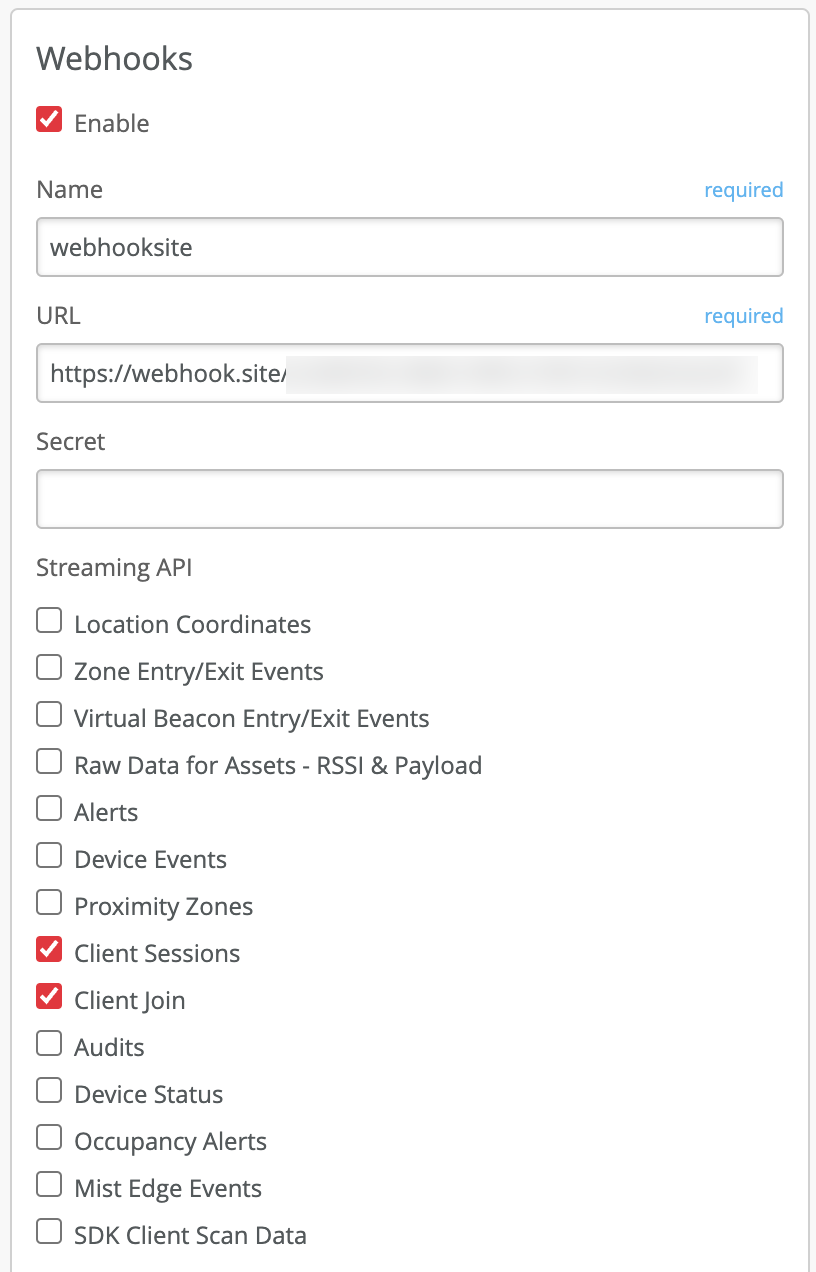
- If required, PSK Name (currently only supported with Cloud PSK Lookup) and PSK ID can be sent via webhooks to a 3rd party collector for auditing purposes:
Example webhook event containing PSK Name and ID information:
{
"topic": "client-join",
"events": [
{
"ap": "d420b080f145",
"ap_name": "APLX-BRQLAB-1",
"band": "5",
"bssid": "d420b08c7c42",
"client_ip": "10.7.0.74",
"client_username": "",
"connect": 1663172583,
"connect_float": 1663172583.292,
"mac": "1a60a07424ca",
"org_id": "2e69ddfd-8af0-4277-b143-762175f7e679",
"psk_id": "946025ff-eae1-4819-b6ad-d396018c2d9b",
"psk_name": "vdementyev@juniper.net",
"random_mac": true,
"rssi": -53,
"site_id": "4ee6e679-caee-49d3-ae4c-de4f97c76850",
"site_name": "BRQLAB",
"ssid": "watchme",
"timestamp": 1663172583,
"version": 2,
"wlan_id": "72559916-5132-4a24-8fa1-a8fc0cb32c8c"
}
]
}
PSK Life Cycle Management – PSK Expiration
Each PSK can be assigned an expiration date, either during create or edit time. Expiration can be set either at a specified time/date or in certain amount of time (days/weeks/months):
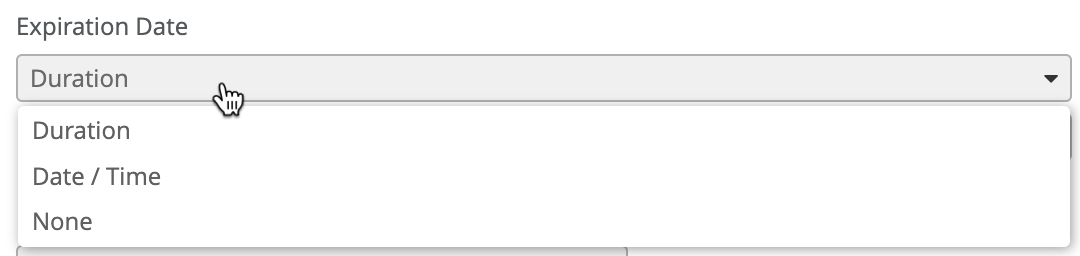

Note: for Local mode PSKs expiration is done hourly, and not exactly at 00:00 of the day of the expiry.
PSK Life Cycle Management – Seamless Rotation
For majority of the IoT client use-cases when per device-type PSK is utilized, there are often situations where a PSK credential needs to be rotated, either because of the PSK compromise or because of the company security policy that mandates periodic credential rotation. Mist provides a simple way to rotate PSK without disrupting existing client connectivity.
Let’s take an example of one PSK that needs to be rotated, but we already have several clients connected, so it will take time for on-site personnel to reconfigure client devices.
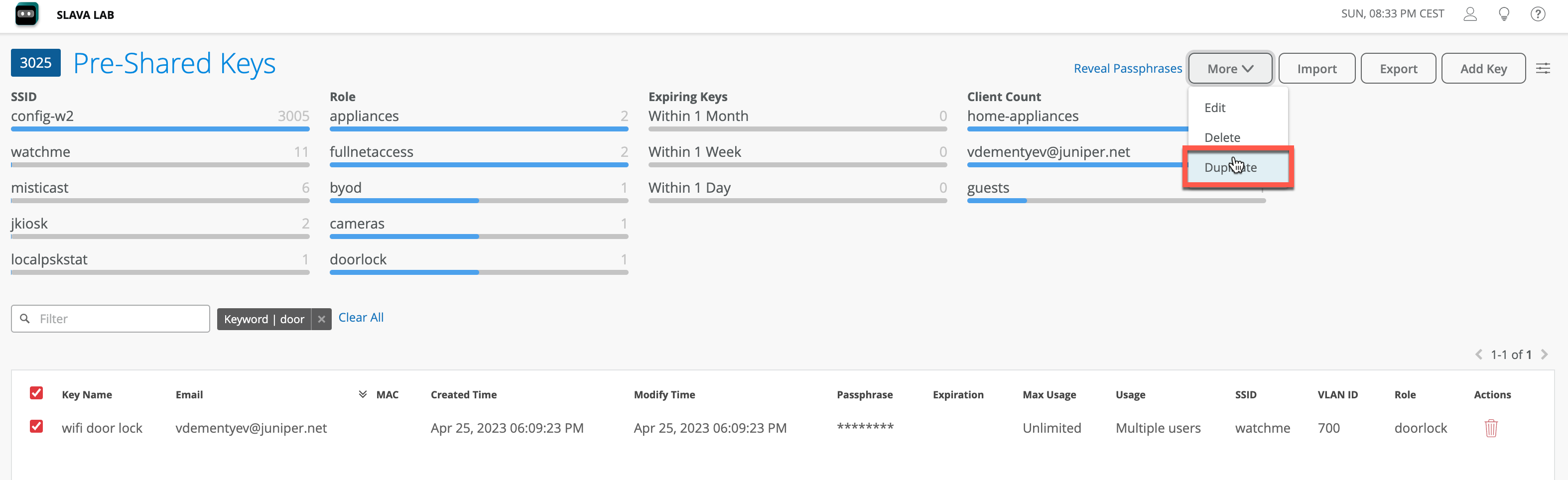
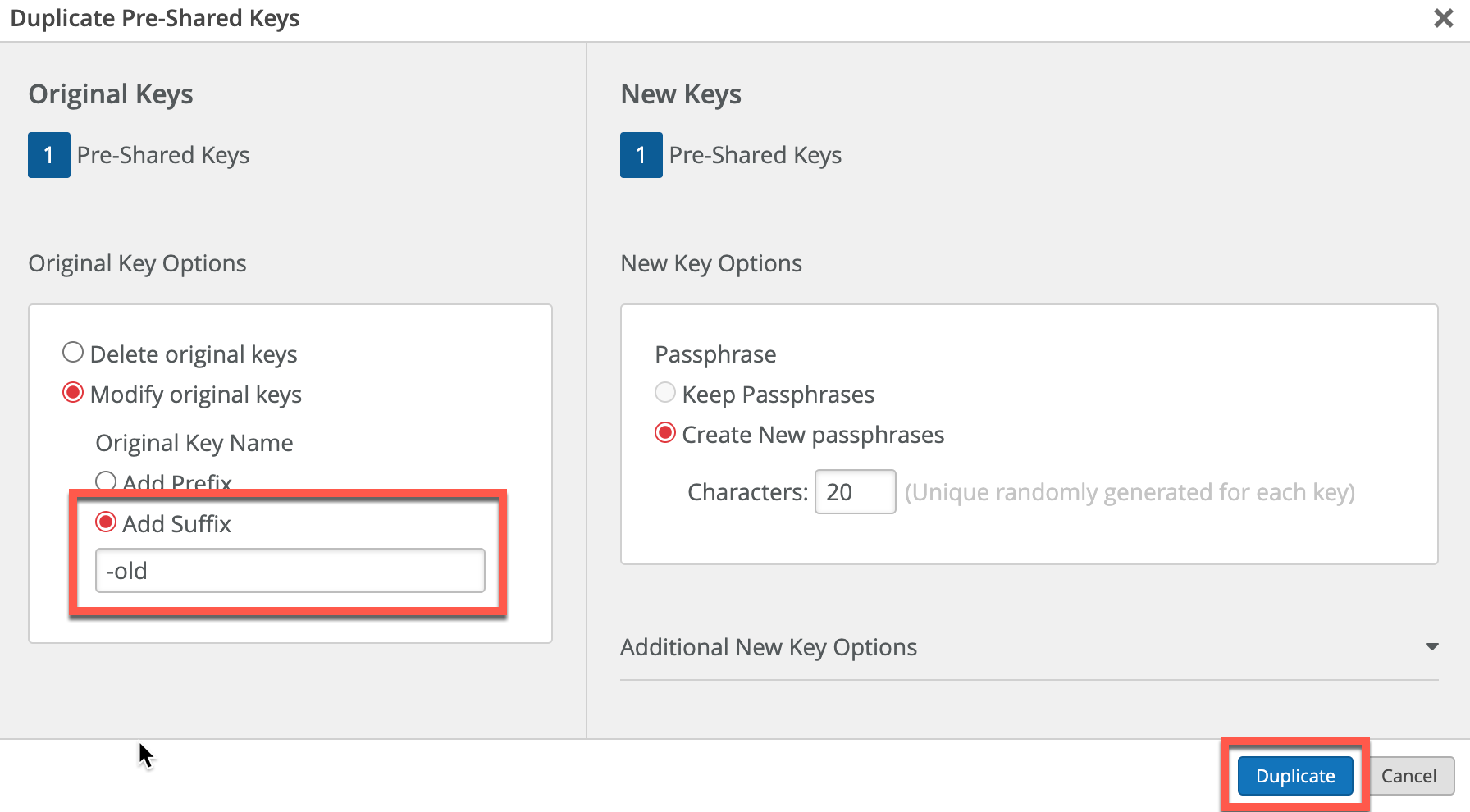
Navigate to the Organization > Wireless > Pre-Shared Keys and select a PSK you want to rotate:
Select “Modify Original keys” and add a Suffix ‘-old’. Define the new key passphrase complexity settings and click Duplicate:
Once done, you will see 2 PSKs active, the exiting one with ‘-old’ suffix and the new one with a new passphrase.
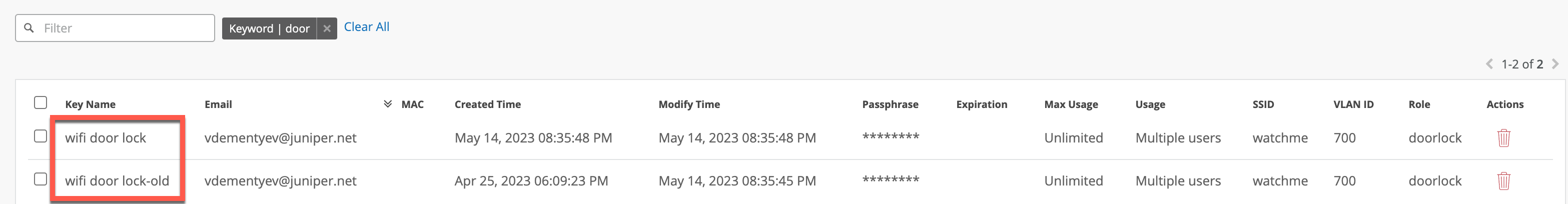
The new key has the exact same security settings inherited from the original (VLAN, Role, Expiration etc), just has a new passphrase.
Now with both PSKs active, you can reconfigure your clients with a new passphrase and at the same time monitor progress and wait until there is no more Active clients on the old PSK, and all have been successfully moved to the new PSK.
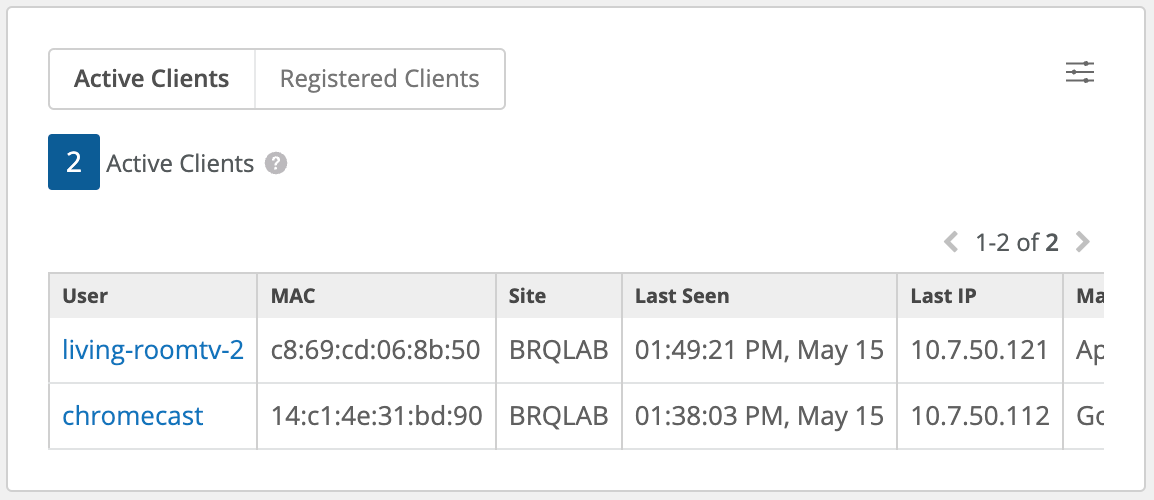
Once you no longer see Active clients on the old PSK, it is safe to remove it manually or let it automatically expire.
PSK Email Notifications
Optionally creating or editing a PSK can generate an automatic email notification to update the user and provide PSK info.
An email notification would contain SSID, passphrase, expiration date and a QR code that can be used by any mobile device for automatic connection:

Features that require IOT Assurance Subscription (S-CLIENT-S)
The following functionality requires IoT Assurance subscription:
- Cloud PSK lookup
- Org-level PSK scale >5,000 PSKs
- Client Onboarding / PSK Portals
- PSK Life Cycle Management (PSK expiration, PSK rotation, per-PSK usage visibility)
IoT Assurance subscription (SUB-CLNT) is calculated based on concurrent active client devices using Multi-PSK functionality over 7 day period. Such mechanism is conservative, allowing for occasional usage peaks.