Table of Contents:
- Supported RADIUS Authentication Attributes
- RADIUS Accounting Attributes
- Dynamic Authorization Extensions
1. Supported RADIUS Authentication Attributes
The RADIUS protocol follows client-server architecture and uses the User Datagram Protocol (UDP) as described in RFC 2865. An Access Point sends user information to the RADIUS server in an Access-Request message and after receiving a reply from the server acts according to the returned information.
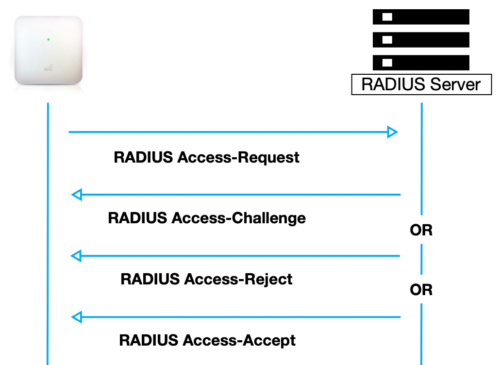
During authentication the RADIUS server then returns one of three responses to the Access Point:
- Access-Reject – The user is unconditionally denied access to the requested network resource. Failure reasons may include an invalid credentials or an inactive account.
- Access-Challenge – Requests additional information from the user such as a secondary password, PIN, token or card. Access-Challenge is also used in more complex authentication when a secure tunnel is established between the user and the Radius Server such as authentication using Extensible Authentication Protocol (EAP).
- Access-Accept – The user is permitted access. The Access-Request often includes additional configuration information for the user using return attributes.
RADIUS services can be enabled on the Mist Access Points for WLAN user authentication. RADIUS services are required for WLANs implementing 802.1X EAP or MAC based authentication.
1.1 IETF Standard Attributes
The following table outlines the standard authentication attributes that have been implemented in Mist Access Points in accordance with RFC 2865. Additional extensions have also been implemented following the recommendations in RFC 2868 and RFC 2869.
| Attribute Name | Type | RFC | Description |
| User-Name | 1 | RFC 2865 | The User-Name attribute is forwarded in the Access-Request and indicates the name of the user to be authenticated. |
| User-Password | 2 | RFC 2865 | The User-Password attribute is forwarded in the Access-Request and indicates the password of the user to be authenticated, or the user’s input following an Access-Challenge. |
| NAS-IP-Address | 4 | RFC 2865 | The NAS-IP-Address attribute is forwarded in the Access-Request and indicates the IP Address of the Access Point requesting user authentication. |
| Service-Type
|
6 | RFC 2865 | The Service-Type attribute is forwarded in the Access-Request and indicates the type of service the user has requested, or the type of service to be provided. The attribute value is always set to Framed-User by the Access Point for 802.1X/EAP WLANs or to Call-Check for the MAC-Auth enabled WLANs. |
| Framed-MTU | 12 | RFC 2865 | The Framed-MTU attribute is forwarded in the Access-Request and indicates the Maximum Transmission Unit (MTU) to be configured for the user. The attribute value is always set to 1200 by the Mist Access Point. |
| State | 24 | RFC 2865 | The State attribute is available to be forwarded in the Access-Challenge and must be sent unmodified from the client to the server in the Access-Request reply to that challenge, if any. |
| Called-Station-Id | 30 | RFC 2865 | The Called-Station-Id attribute is forwarded in the Access-Request and indicates the BSSID and ESSID that the authenticating user is associated with. The Access Point will forward the attribute value using the following formatting: XX-XX-XX-XX-XX-XX:ESSID. |
| Calling-Station-Id | 31 | RFC 2865 | The Calling-Station-Id attribute is forwarded in the Access-Request and indicates the MAC address of the authenticating user. It is only used in Access-Request packets. The Access Point will forward the attribute value using the following formatting: XX-XX-XX-XX-XX-XX. |
| NAS-Identifier
|
32 | RFC 2865 | The NAS-Identifier attribute is forwarded in the Access-Request and indicates user defined identifier if configured on the WLAN. |
| Proxy-State | 33 | RFC 2865 | The proxy-state attribute is sent by proxy-server to another server when forwarding Access-Requests; this must be returned unmodified in the Access-Accept, Access-Reject or Access-Challenge and removed by the proxy server before sending the response to the network access server |
| NAS-Port-Type | 61 | RFC 2865 | The NAS-Port-Type attribute is forwarded in the Access-Request and indicates the type of physical connection for the authenticating the user. The attribute value is always set to Wireless-802.11 by the Access Point. |
| Connection-Info
|
77 | RFC 2869 | The Connection-Info attribute is forwarded in the Access-Request and indicates the data-rate and radio type of the authenticating user. The Access Point will forward the attribute value using the following formatting: CONNECT XXMbps 802.11X. |
| EAP-Message | 79 | RFC 2869 | The EAP-Message attribute is forwarded in the Access-Request, Access-Challenge, Access-Accept and Access-Reject and encapsulates Extended Access Protocol (EAP) packets. |
| Message-Authenticator | 80 | RFC 2869 | The Message-Authenticator attribute is forwarded in the Access-Request and may be used to prevent spoofing of CHAP, ARAP or EAP Access-Request packets. |
| Tunnel-Private-Group-ID | 81 | RFC 2868 | The Tunnel-Private-Group-ID attribute is forwarded in the Access-Accept and indicates the numerical VLAN ID to be assigned to the authenticating user. The attribute value must be set to a numerical value between 1 and 4094 or a string representing a named VLAN. |
| Filter-Id | 11 | RFC 2865 | The Filter-Id attribute may be forwarded in the Access-Accept and indicates user role client will be associated with. User Groups are used by the Mist WxLAN policy framework to assign network firewall rules. |
Supported IETF Standard Authentication Attributes
1.1.1 Tunnel-Private-Group-ID
The Tunnel-Private-Group-ID attribute may be forwarded in the Access-Accept to indicate the dynamic VLAN membership of an 802.1X or RADIUS MAC authenticated user.
| Attribute Name | Attribute Number | Attribute Value |
| Tunnel-Private-Group-ID | 81 | 1 – 4094 (Assigned VLAN-ID) or String (Assigned VLAN Name) |
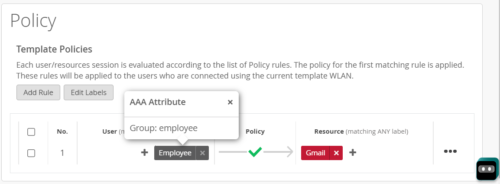
1.1.2 Filter-Id
The Filter-Id attribute may be forwarded in the Access-Accept and indicates user role client will be associated with. User Groups are used by Mist WxLAN policy framework to assign granular network resource restrictions.
| Attribute Name | Attribute Number | Attribute Value |
| Filter-Id | 11 | String |
| Format: Group-Name | ||
| Example: employee | ||
WxLAN Policy example configuration:
1.1.3 NAS-Identifier
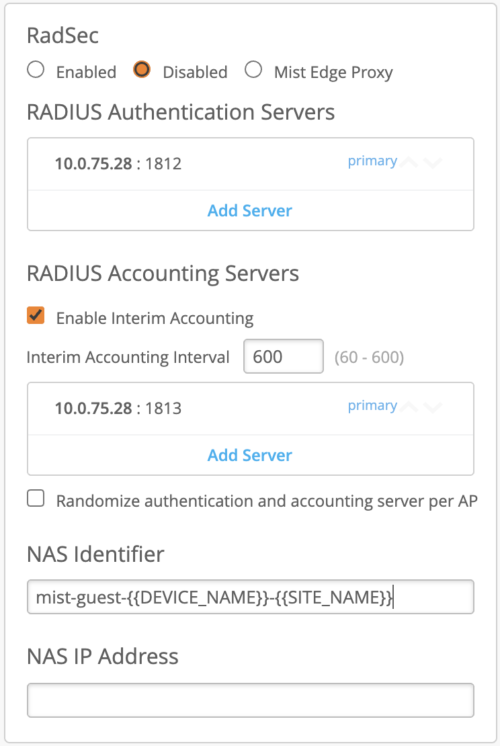
The NAS-Identifier attribute is a user-configurable AVP that could be unique per WLAN configuration. All Mist Access Points would send the configured NAS-ID value. Please note that Mist Cloud allows for dynamic payload configuration, such as to send current AP hostname, Site Name or AP MAC address, AP model, using pre-defined variables for example:
{{DEVICE_NAME}}
{{DEVICE_MODEL}}
{{DEVICE_MAC}}
{{SITE_NAME}}
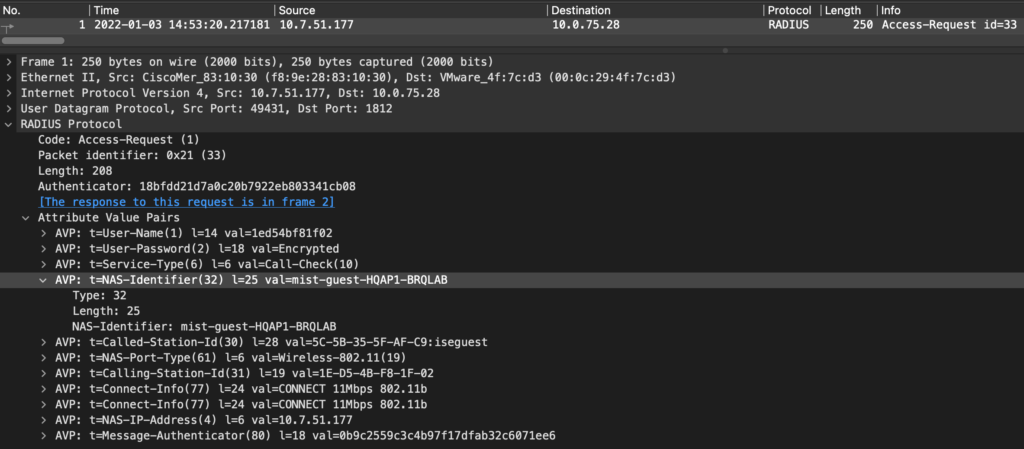
The above configuration would result in AP sending NAS ID that would include AP Hostname as well as Mist Site name in the request:
1.2 Supported Vendor-Specific Attributes
The following table outlines vendor-specific attributes (VSAs) that are supported by Mist Access Points in accordance with RFC 2865.
| Attribute Name | Type | Vendor ID | Attribute Number | Formatting |
| Airespace-Interface-Name | 26 | 14179 | 5 | String |
| Airespace-ACL-name | 26 | 14179 | 6 | String |
| Aruba-User-Role | 26 | 14823 | 1 | String |
| Cisco-AVPair | 26 | 9 | 1 | String |
| Eleven-Authentication-Find-Key | 26 | 52970 | 3 | TLV |
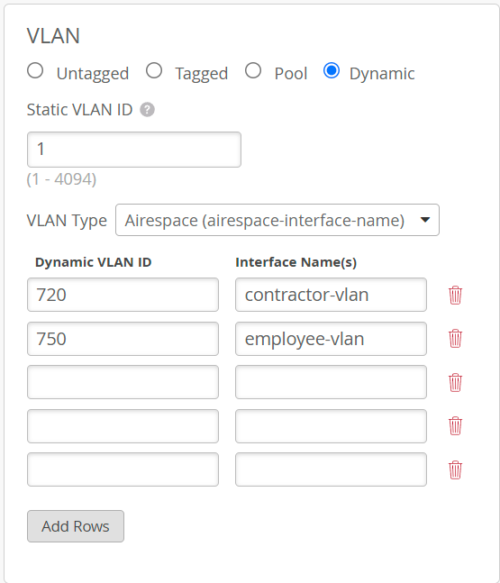
1.2.1 Airespace-Interface-Name
The Airespace-Interface-Name attribute may be forwarded in the Access-Accept to indicate the dynamic VLAN membership of an 802.1X or RADIUS MAC authenticated user. Returned attribute value is always a string formatted name of the VLAN. VLAN Name to VLAN ID translation must be configured under WLAN using VLAN IDs or Variables.
| Attribute Name | Vendor ID | Attribute Number | Attribute Format |
| Airespace-Interface-Name | 14179 | 5 | String |
| Format: VLAN-Name | |||
| Example: employee-vlan | |||
1.2.2 Airespace-ACL-Name
The Airespace-ACL-Name attribute maybe forwarded in the Access-Accept and indicates user role client will be associated with. User Groups are used by Mist WxLAN policy framework to assign granular network resource restrictions.
| Attribute Name | Vendor ID | Attribute Number | Attribute Format |
| Airespace-ACL-Name | 14179 | 6 | String |
| Format: Group-Name | |||
| Example: employee | |||
WxLAN Policy example configuration:

1.2.3 Aruba-User-Role
The Aruba-User-Role attribute maybe forwarded in the Access-Accept and indicates user role client will be associated with. User Groups are used by Mist WxLAN policy framework to assign granular network resource restrictions.
| Attribute Name | Vendor ID | Attribute Number | Attribute Format |
| Aruba-User-Role | 14823 | 1 | String |
| Format: Group-Name | |||
| Example: employee | |||
WxLAN Policy example configuration:
1.2.4 Cisco-AVPair url-redirect
The Cisco-AVPair attribute maybe forwarded in the Access-Accept to indicate to the Mist Access Point that a client needs to be redirected for portal authentication and specify the redirect-URL location. This attribute is typically used for Guest Access integrations with Cisco ISE or Aruba Clearpass RADIUS servers or to enable Posture Redirect functionality for 802.1X/EAP users.
| Attribute Name | Vendor ID | Attribute Number | Attribute Format |
| Cisco-AVPair | 9 | 1 | String |
| Format: url-redirect=<URL value> | |||
| Example: url-redirect=https://ise28.89mistilbs.org:8443/portal/gateway?sessionId=0a004b1c/Jtf4peiJ5A8nPreloHRRITWvmhDCbnH3qXQ8MngtoA&portal=71984f36-f55e-4439-ba6e-903d9f77c216&action=cwa&token=1f7dca2cc907b1ad56ee4880e1cfa1ae | |||
1.2.5 Cisco-AVPair PSK
The Cisco-AVPair attribute may also contain PSK attribute, indicating to the Mist Access Point which passphrase is assigned to a certain client. Note that to provide a PSK value to the AP, two Cisco AVPair attributes must be sent simultaneously, one indicating that PSK will be sent in ASCII format and another AVPair providing the actual Pre-Shared Key value.
| Attribute Name | Vendor ID | Attribute Number | Attribute Format |
| Cisco-AVPair | 9 | 1 | String |
| Format:
psk-mode=ascii & psk=<passphrase> |
|||
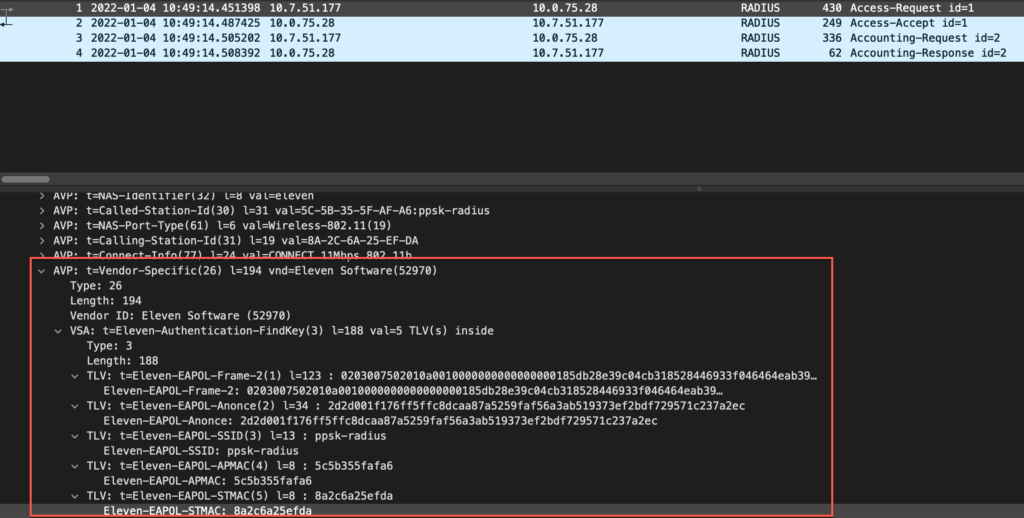
1.2.6 Eleven-Authentication-Find-Key
The Eleven-Authentication-Find-Key attribute is used to supply additional information to the supported RADIUS servers to simplify wireless client PSK lookup via RADIUS, removing the need to pre-associate a wireless client MAC with a particular PSK ahead of time. This attribute is a TLV according to the RFC6929 that contains multiple sub-attributes inside.
| Attribute Name | Vendor ID | Type | Attribute Format |
| Eleven-Authentication-Find-Key | 52970 | 3 | TLV |
| TLV Sub-Attribute Name | Sub Attribute Number | Sub Attribute Format | Description |
| Eleven-EAPOL-Frame-2 | 1 | Octets | Eleven-EAPOL-Frame-2 sub attribute contains the second EAPOL frame sent by the wireless client to the Access Point during a 4way handshake |
| Eleven-EAPOL-Anonce | 2 | Octets | Eleven-EAPOL-Anonce sub attribute contains the first EAPOL frame sent by the Access Point to the wireless client during a 4way handshake |
| Eleven-EAPOL-SSID | 3 | String | Eleven-EAPOL-SSID sub attribute contains current SSID name that the wireless client is trying to associate to |
| Eleven-EAPOL-APMAC | 4 | Octets | Eleven-EAPOL-APMAC sub attribute contains BSSID in xxxxxxxxxxxx format |
| Eleven-EAPOL-STMAC | 5 | Octets | Eleven-EAPOL-STMAC sub attribute contains wireless client MAC address in xxxxxxxxxxxx format |
Example packet capture:
2 RADIUS Accounting Attributes
RADIUS accounting information can be used to track individual user’s network usage for billing purposes as well as be used as a tool for gathering statistic for general network monitoring.
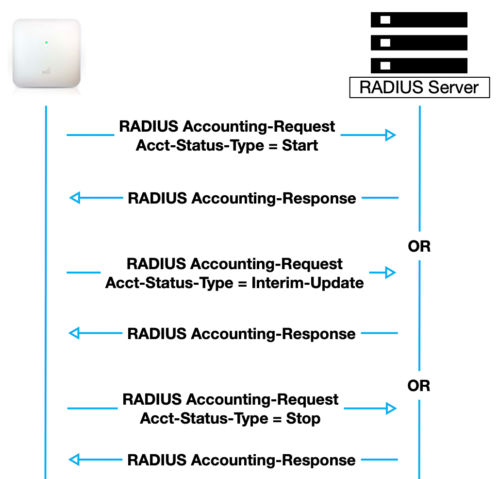
When network access is granted to the user by the Access Point, an Accounting-Request message with the Acct-Status-Type field set to Start is forwarded by the Access Point to the RADIUS server to signal the start of the user’s network access. Start records typically contain the user’s identification, point of attachment and a unique session identifier.
Optionally periodic Accounting-Request messages with the Acct-Status-Type field set to Interim-Update may be sent by the Access Point to the RADIUS server to update it on the status of an active session. Interim records typically convey the current session duration and information on current data usage.
When the user’s session is closed (wireless client disconnects from the AP or roams to the next Access Point), the Access Point forwards an Accounting-Request message with the Acct-Status-Type field set to Stop. This provides information on the final usage in terms of time, packets transferred, data transferred and reason for disconnect and other information related to the user’s network access.
RADIUS Accounting can be enabled / disabled per WLAN. For each WLAN the following accounting configuration is supported:
- Start-Stop – Mist Access Points will forward Accounting-Requests at the start and end of the user sessions. This behavior is enabled by default, as soon as at least one Accounting server is configured under WLAN.
- Start-Interim-Stop – Mist Access Points will forward Accounting-Requests at the start and end of the user sessions as well as periodically during the lifetime of the sessions. In addition to that, Framed-IP-Address attribute will be included in the Accounting messages. Note that Interim-Update interval can also be dynamically overridden by sending Acct-Interim-Interval (85) AVP from the RADIUS server.
The following table outlines the standard RADIUS accounting attributes that have been implemented in the Mist Access Points in accordance with RFC 2866:
| Attribute Name | Type | RFC | Description |
| User-Name | 1 | RFC 2865 | The User-Name attribute is forwarded in the Accounting-Request and indicates the name of the user. |
| NAS-IP-Address | 4 | RFC 2865 | The NAS-IP-Address attribute is forwarded in the Accounting-Request and indicates the IP Address of the Access Point. |
| Framed-IP-Address | 8 | RFC 2865 | The Framed-IP-Address attribute is forwarded in the Accounting-Request packets and indicates current or last-known IP address of the wireless client. It is only sent when Interim Accounting is enabled on the WLAN.
Note: during the first client connection, when client has not yet obtained an IP address, Framed-IP-Address AVP will be missing in the first Accounting-Start packet. However, as soon as the AP learns client IP address, it will send asynchronous (outside of normal Interim-Accounting update interval) Accounting Interim-Update message with Framed-IP-Address information. |
| Class | 25 | RFC 2865 | The Class attribute is optionally forwarded in the Access-Accept and should be sent unmodified by the client to the accounting server as part of the Accounting-Request packet if accounting is enabled. Mist Access Points support sending multiple Class attributes for each client. |
| Called-Station-Id | 30 | RFC 2865 | The Called-Station-Id attribute is forwarded in the Accounting-Request and indicates the BSSID and ESSID that the user is associated with. The Access Point will forward the attribute value using the following formatting: XX-XX-XX-XX-XX-XX:ESSID. |
| Calling-Station-Id | 31 | RFC 2865 | The Calling-Station-Id attribute is forwarded in the Accounting-Request and indicates the MAC address of the user. The Access Point will forward the attribute value using the following formatting: XX-XX-XX-XX-XX-XX. |
| NAS-Identifier | 32 | RFC 2865 | The NAS-Identifier attribute is forwarded in the Accounting-Request and indicates the user defined identifier configured under WLAN settings. |
| Acct-Status-Type
|
40 | RFC 2866 | The Acct-Status-Type attribute is forwarded in the Accounting-Request and indicates whether the Accounting-Request marks the status of the accounting update. Supported values include Start, Stop and Interim-Update. |
| Acct-Delay-Time
|
41 | RFC 2866 | The Acct-Delay-Time attribute is forwarded in the Accounting-Request and indicates how many seconds the Access Point has been trying to send the accounting record for. This value is subtracted from the time of arrival on the server to find the approximate time of the event generating this Accounting-Request. |
| Acct-Input-Octets | 42 | RFC 2866 | The Acct-Input-Octets attribute is forwarded in the Accounting-Request and indicates how many octets have been received from the user over the course of the connection. This attribute may only be present in Accounting-Request records where the Acct-Status-Type is set to Stop. |
| Acct-Output-Octets | 43 | RFC 2866 | The Acct-Output-Octets attribute is forwarded in the Accounting-Request and indicates how many octets have been forwarded to the user over the course of the connection. This attribute may only be present in Accounting-Request records where the Acct-Status-Type is set to Stop. |
| Acct-Session-Id | 44 | RFC 2866 | The Acct-Session-Id attribute is forwarded in the Accounting-Request and provides a unique identifier to make it easy to match start, stop and interim records in an accounting log file. |
| Account-Authentic | 45 | RFC 2866 | The Account-Authentic attribute is forwarded in the Accounting-Request and indicates how the user was authenticated. When RADIUS accounting is enabled the Access Point will set this value to RADIUS. |
| Acct-Session-Time | 46 | RFC 2866 | The Acct-Session-Time attribute is forwarded in the Accounting-Request and indicates how many seconds the user has received service for. This attribute may only be present in Accounting-Request records where the Acct-Status-Type is set to Stop. |
| Acct-Input-Packets | 47 | RFC 2866 | The Acct-Input-Packets attribute is forwarded in the Accounting-Request and indicates how many packets have been received from the user over the course of the connection. This attribute may only be present in Accounting-Request records where the Acct-Status-Type is set to Stop. |
| Acct-Output-Packets | 48 | RFC 2866 | The Acct-Output-Packets attribute is forwarded in the Accounting-Request and indicates how many packets have been forwarded to the user over the course of the connection. This attribute may only be present in Accounting-Request records where the Acct-Status-Type is set to Stop. |
| Acct-Terminate-Cause | 49 | RFC 2866 | The Acct-Terminate-Cause attribute is forwarded in the Accounting-Request and indicates how the session was terminated. This attribute may only be present in Accounting-Request records where the Acct-Status-Type is set to Stop. |
| Event-Timestamp | 55 | RFC 2869 | The Event-Timestamp attribute is forwarded in the Accounting-Request and indicates the time that the accounting event occurred on the Access Point. |
| NAS-Port-Type | 61 | RFC 2865 | The NAS-Port-Type attribute is forwarded in the Accounting-Request and indicates the type of physical connection for the user. This attribute value is always set to Wireless-802.11 by the Mist Access Point.
|
IETF Standard Accounting Attributes
3 Dynamic Authorization Extensions
The RADIUS authentication protocol originally did not support unsolicited messages sent from the RADIUS server to the Access Point. However, there are many instances in which it is desirable for changes to be made to session characteristics without requiring the Access Point to initiate the exchange.
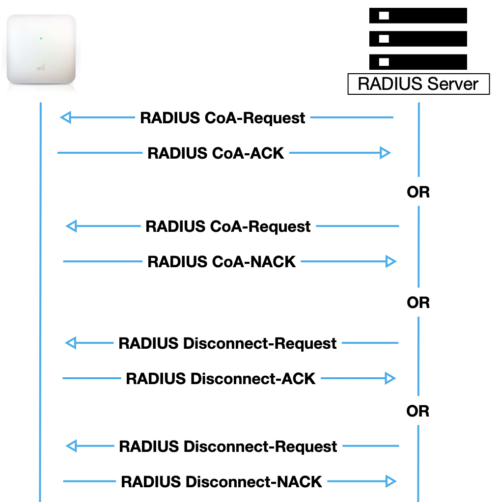
To overcome these limitations several vendors have implemented additional RADIUS extensions support unsolicited messages sent from the RADIUS server to an Access Point. These extensions support Disconnect and Change-of-Authorization (CoA) messages that can be used to terminate an active user session or change the characteristics of an active session.
Disconnect-Request – Causes a user session to be terminated. The Disconnect-Request packet identifies the NAS as well as the user session to be terminated by inclusion of the identification attributes shown in table 3.0.
CoA-Request – Causes session information to by dynamically updated on the Access Point.
The following table outlines the required dynamic authorization attributes for Disconnect and CoA Requests respectively.
3.1 Disconnect-Request
| Attribute Name | Vendor | Attribute Number | Description |
| Event-Timestamp | IETF | 55 | Time at which Disconnect-Request has been issued. Time will be checked by the Mist AP. If clock drift is too big, Disconnect Request will be discarded.
Event-Timestamp attribute validation can be optionally disabled under WLAN configuration. |
| Calling-Station-Id | IETF | 31 | MAC address of the user in XX-XX-XX-XX-XX-XX format. |
Example packet capture:

Note that if addititional Attributes are sent by the RADIUS server, some will also be evaluated (for example NAS-IP-Address value must match current IP address of the Mist AP, or Acct-Session-Id must match wireless client session ID), while other attributes that are not supported will be ignored (for example Acct-Terminate-Cause). The minimum set of attributes outlined in the table above is sufficient for the Disconnect to work.
3.2 CoA-Request
| Attribute Name | Vendor | Attribute Number | Description |
| Event-Timestamp | IETF | 55 | Time at which Disconnect-Request has been issued. Time will be checked by the Mist AP. If clock drift is too big, Disconnect Request will be discarded.
Event-Timestamp attribute validation can be optionally disabled under WLAN configuration |
| Calling-Station-Id | IETF | 31 | MAC address of the user in XX-XX-XX-XX-XX-XX format. |
| Cisco-AVPair | Cisco (9) | 1 | subscriber-command:reauthenticate |
Example packet capture:
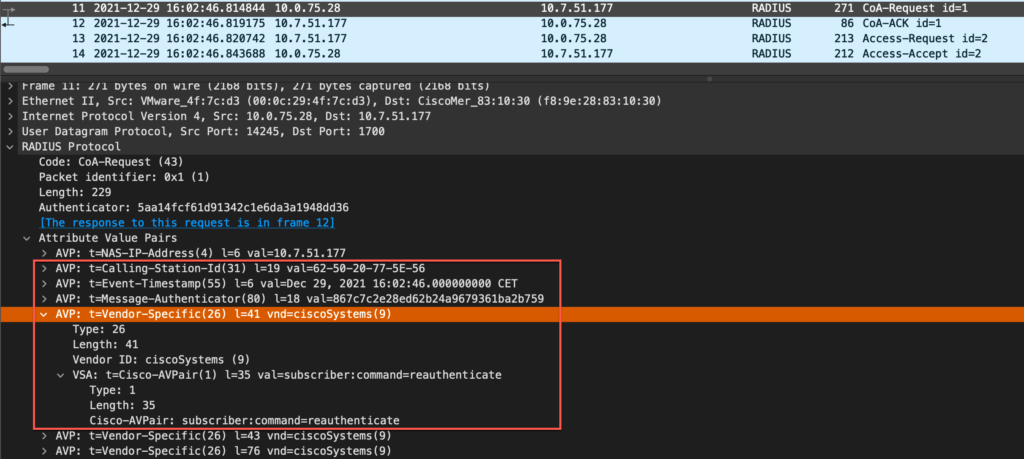
Note that other Attributes if sent by the RADIUS server will also be evaluated (for example NAS-IP-Address value must match current IP address of the Mist AP, or Acct-Session-Id must match wireless client session ID), while attributes that are not supported will be ignored (for example any additional Cisco-AVPair attributes). The minimum set of attributes outlined in the table above is sufficient for the CoA to work.
Note: in case of MAC-Authentication and CoA, subsequent Access-Accept must contain User-Name attribute that would be equal to the wireless client MAC address
