Simplified Operations
RADIUS-assigned VLAN pools
WLANs with 802.1X, MAC address authentication by RADIUS lookup, or RADIUS PSK security now support VLAN assignment using VLAN pools. That is, when dynamic VLANs are configured on a RADIUS WLAN, the RADIUS server can return a VLAN name (Airespace-Interface-Name or Tunnel-Private-Group-ID) in the RADIUS access-accept message. That VLAN name could then map to a single VLAN or what is newly added – a pool of VLANs that clients are distributed amongst. A pool of VLANs is now also supported on the static VLAN, which is used when RADIUS does not return a VLAN attribute in the access-accept.
The following are a few points to consider:
- The static VLAN pool is supported with either Airespace or Standard VLAN Type configured in Mist.
- The RADIUS-assigned VLAN pools are supported only with Airespace VLAN Type configured in Mist, since we expect a named VLAN returned from RADIUS. However, even with Airespace configured in Mist, you can return a VLAN name in either Airespace-Interface-Name or Tunnel-Private-Group-ID AVPs in the RADIUS access-accept. We recognize that this is confusing, and we plan to rename the VLAN Types to be more obvious in a future update.
- A range of VLANs and/or comma separated VLANs are supported.
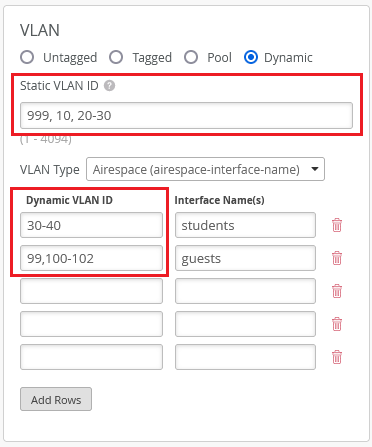
Note: These new VLAN pool capabilities are supported on 0.14.x firmware, or newer.
Email notification to guest users when sponsors act on their access request
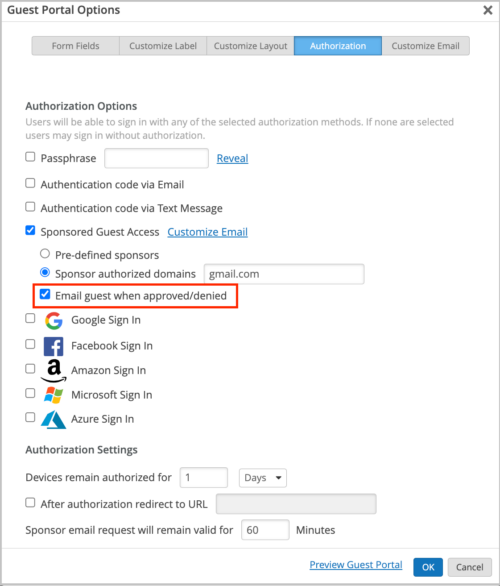
You can configure the Mist portal to send an email notification to the guest portal users with Sponsored Guest Access as their authorization method, when the sponsors act on their access requests. To configure this, navigate to the Authorization tab of the guest portal configuration page (accessed from Site > WLANs), and select the Email guest when approved/denied check box. This check box is disabled by default. The notification contains the request approval status, the time at which the request was approved, and the duration for which the authorization will be in effect.
Enhancements to Client movements on Live View
The Live View page (Location > Live View) for client locations has been updated with enhancements for seamless client movement rendering for all client types. The change applies to:
- SDK Clients
- Named Assets
- Discovered Assets
- Connected Wi-Fi Clients
- Unconnected Wi-Fi Clients
Marvis
Support for querying and troubleshooting Zoom calls
You can now use the Marvis Conversational Assistant to query your Zoom calls and troubleshoot any issues with them. To use this feature, your organization must have your Zoom account integrated. Or, the organization must have an SSR or SRX WAN Edge device. Marvis considers the SSR or SRX Zoom data when no Zoom account is integrated with the organization.
Zoom integration, already available as a beta feature, lets you (as an admin user) link your Zoom account to your Mist organization. With this linking, you get visibility into the Meeting Insights (available on the Monitor > Service Levels page) created based on the end-to-end application metrics from Zoom and network metrics from Mist. Note that the Meeting Insights section is updated a couple of hours after a meeting ends.
Using the Marvis Conversational Assistant, you can:
- List all Zoom calls.
- List bad Zoom calls.
- Troubleshoot the Zoom application based on the client MAC address, hostname, and site. You can troubleshoot the issues reported during the last 7 days.
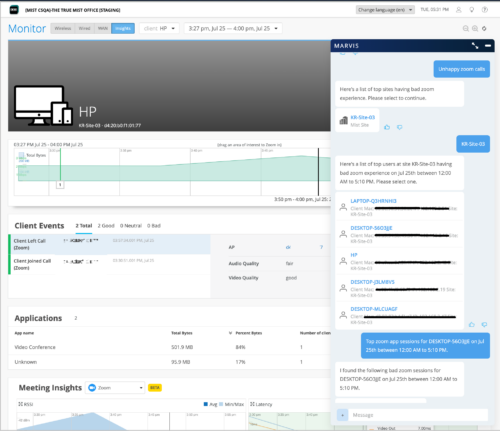
Marvis Conversational Assistant listing bad Zoom calls (1)
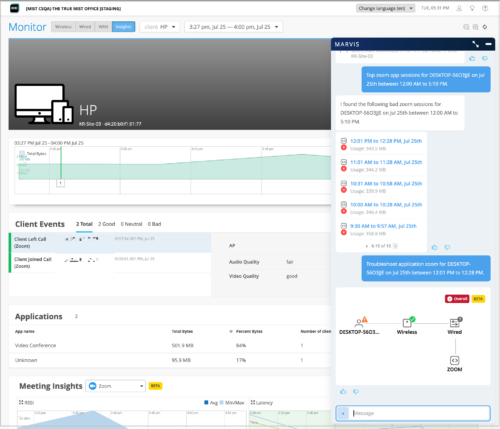
Marvis Conversational Assistant listing bad Zoom calls (2)
WAN Assurance
Default WAN Edge Templates
For greenfield deployments, you can now create new WAN Edge templates using pre-populated configurations based on specific device models. For example, if you select an SSR120 to base a WAN Edge template on, the template gets pre-populated with information such as the DHCP/DHCP server details for the WAN (ge-0/0/0, ge-0/0/1, ge-0/0/2) and LAN (ge-0/0/3) interfaces, and the default policies (LAN -> WAN).
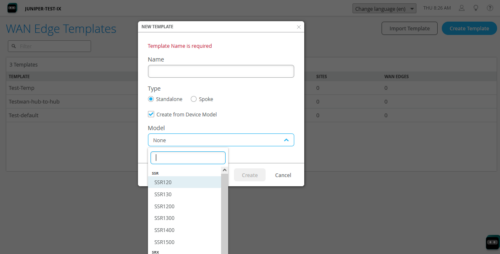
Used in combination with Zero Touch Provisioning, this feature simplifies the process of onboarding and setting up a WAN Edge device in the following three simple steps:
- Create a site.
- Create a template from a device model and assign it to the site.
- Claim WAN Edge and assign the device to the site.
Port Aggregation support for SSR devices
Port Aggregation, which was available on SRXs, is now also supported on the SSR family, as part of WAN Assurance. You can configure this using the Port Aggregation field in the WAN and LAN configuration sections on the WAN Edge Template and device configuration pages.
Wired Assurance
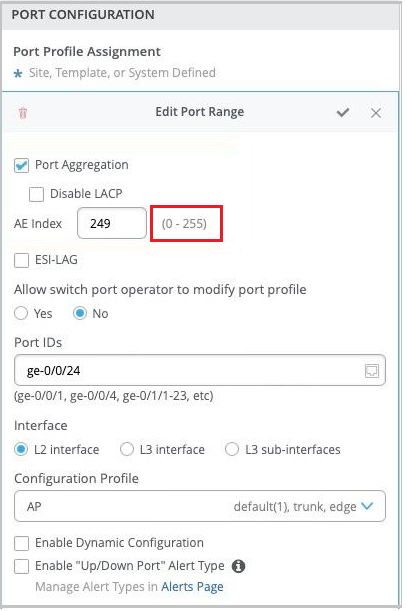
Support for AE interface index range from 0 to 255
We have increased the supported range of aggregated Ethernet (AE) interface index (aex) from 0-127 to 0-255. You can configure the AE index on the Ports tab of your campus fabric page (Organization > Campus Fabric > Ports) and through the switch configuration templates (Organization > Switch Templates). In the switch configuration template, the AE index configuration is available on the Port Config tab in the Select Switches Configuration section, as shown below.
Behavior Changes
Change to channel 144 configuration
We have removed the option to explicitly allow channel 144 from the site configuration page (Organization > Site Configuration). Channel 144 is now enabled by default for use by RRM or is available for manual assignment in countries where it is allowed. You can disable or enable it in RRM like any other channel. Channel 144 can be disabled via the Set allowable channels option in the RF template (Organization > RF Templates) or device profile (Organization > Device Profiles).
New source IP addresses in webhook requests (Global 02)
Mist now uses new source IP addresses in its webhook request to customers’ networks. The new IP addresses range from 34.94.226.48 to 34.94.226.63 (34.94.226.48/28). This change is applicable only to the Global 02 cloud.
Please add these IP addresses to your firewall to receive webhook requests from Mist. These are static IP addresses.
The previously used source IP addresses (34.94.120.8, 35.236.34.24, and 35.236.92.224) are no longer valid.
See also: Ports to enable on your firewall.
Security Alerts
End of support for cipher suites using the CBC mode
Juniper Mist has ended support for cipher suites using the Cipher Block Chaining (CBC) mode of operation on our cloud endpoints. These cipher suites are known to be susceptible to attacks such as padding oracle attack, which can lead to data leaks and other security issues. For more information see, End of support for cipher suites using the CBC mode.