Feature Overview
With the help of this feature you can monitor the service status of following in any of the SRX:
- EWF
- IDP
- App_Secure
The following services on an SRX – showcase if configured:
- Whether the licenses are present
- Status of Service
Status of all the features will look like following :
"service_status": {
"idp_status": "disabled", // either "enabled" or "disabled"
"idp_policy": "", // if the above is disabled this will be empty
"appid_status": "disabled", // either "enabled" or "disabled"
"ewf_status": "disabled", // either "enabled" (websense up), "disabled" (no config) or "down" (websense down)
"appid_version": 0 // this will be 0 if appid_status is disabled, as we then don't check the version number
},
This feature requires special licenses on SRX to enable them . To purchase the SRX license for the mentioned features, please refer to:
After purchasing, please install the licenses using the below link:
On the SRX , use the “Show system license” command to display the license name with expiry date. Here is an example:
root@00c52c4c3204> show system license
License usage:
Licenses Licenses Licenses Expiry
Feature name used installed needed
anti_spam_key_sbl 0 1 0 2022-04-28 00:00:00 UTC
idp-sig 0 1 0 2022-04-28 00:00:00 UTC
dynamic-vpn 0 2 0 permanent
av_key_sophos_engine 0 1 0 2022-04-28 00:00:00 UTC
logical-system 1 3 0 permanent
wf_key_websense_ewf 0 1 0 2022-04-28 00:00:00 UTC
remote-access-ipsec-vpn-client 0 2 0 permanent
Licenses installed:
License identifier: DemoLabJUNOS386107562
License version: 4
Valid for device: CV4720AF0436
Customer ID: Juniper Internal
Features:
av_key_sophos_engine - Anti Virus with Sophos Engine
date-based, 2021-04-27 00:00:00 UTC - 2022-04-28 00:00:00 UTC
anti_spam_key_sbl - Anti-Spam
date-based, 2021-04-27 00:00:00 UTC - 2022-04-28 00:00:00 UTC
idp-sig - IDP Signature
date-based, 2021-04-27 00:00:00 UTC - 2022-04-28 00:00:00 UTC
wf_key_websense_ewf - Web Filtering EWF
date-based, 2021-04-27 00:00:00 UTC - 2022-04-28 00:00:00 UTC
Topology Requirements
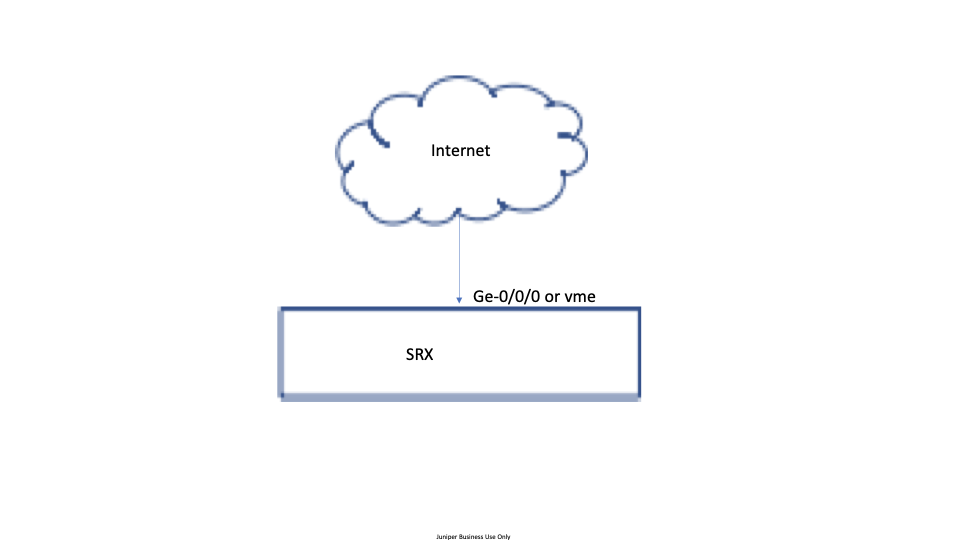
Configuration
Configuring EWF
Before configuring EWF Use command “show security utm web-filtering status” in the SRX to check if EWF server is showing UP. Since configurations are not pushed yet, it should not show as ‘UP.’
root@00c52c4c3204> show security utm web-filtering status UTM web-filtering status: Server status: no-config root@00c52c4c3204>
In the configuration mode, use the following configurations in the SRX to enable EWF:
set system syslog file utm-log any any set system syslog file utm-log match RT_UTM set security utm custom-objects url-pattern blacklist value https://*.poki.com set security utm custom-objects custom-url-category restricted value blacklist set security utm default-configuration anti-virus type sophos-engine set security utm default-configuration anti-virus scan-options uri-check set security utm default-configuration anti-virus scan-options timeout 30 set security utm default-configuration anti-virus sophos-engine sxl-timeout 5 set security utm default-configuration web-filtering url-blacklist restricted set security utm default-configuration web-filtering type juniper-enhanced set security utm default-configuration web-filtering juniper-enhanced server host rp.cloud.threatseeker.com set security utm default-configuration web-filtering juniper-enhanced server port 80 set security utm default-configuration web-filtering juniper-enhanced default permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Games action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Gambling action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Abused_Drugs action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Adult_Content action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Adult_Material action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Advanced_Malware_Command_and_Control action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Advanced_Malware_Payloads action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Bot_Networks action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Compromised_Websites action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Drugs action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Emerging_Exploits action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Files_Containing_Passwords action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Hacking action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Illegal_or_Questionable action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Keyloggers action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Malicious_Embedded_Link action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Malicious_Embedded_iFrame action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Malicious_Web_Sites action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Militancy_and_Extremist action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Mobile_Malware action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Network_Errors action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Newly_Registered_Websites action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Pay_to_Surf action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Phishing_and_Other_Frauds action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Potentially_Damaging_Content action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Potentially_Exploited_Documents action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Potentially_Unwanted_Software action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Racism_and_Hate action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Spyware action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Suspicious_Content action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Suspicious_Embedded_Link action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Unauthorized_Mobile_Marketplaces action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Alcohol_and_Tobacco action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Application_and_Software_Download action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Bandwidth action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Computer_Security action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Custom_Encrypted_Payloads action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Elevated_Exposure action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Entertainment action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Entertainment_Video action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_File_Download_Servers action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Freeware_and_Software_Download action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Instant_Messaging action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Internet_Auctions action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Internet_Radio_and_TV action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Intolerance action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Lingerie_and_Swimsuit action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Marijuana action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Media_File_Download action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Message_Boards_and_Forums action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Non_Traditional_Religions action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Non_Traditional_Religions_and_Occult_and_Folklore action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Nudity action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Parked_Domain action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Peer_to_Peer_File_Sharing action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Personals_and_Dating action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Prescribed_Medications action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Private_IP_Addresses action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Pro_Choice action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Pro_Life action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Proxy_Avoidance action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Sex action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Sex_Education action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Social_Networking_and_Personal_Sites action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Surveillance action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Tasteless action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Violence action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Web_and_Email_Spam action log-and-permit set security utm utm-policy custom-utm-policy anti-virus http-profile junos-av-defaults set security utm utm-policy custom-utm-policy web-filtering http-profile wf-home commit
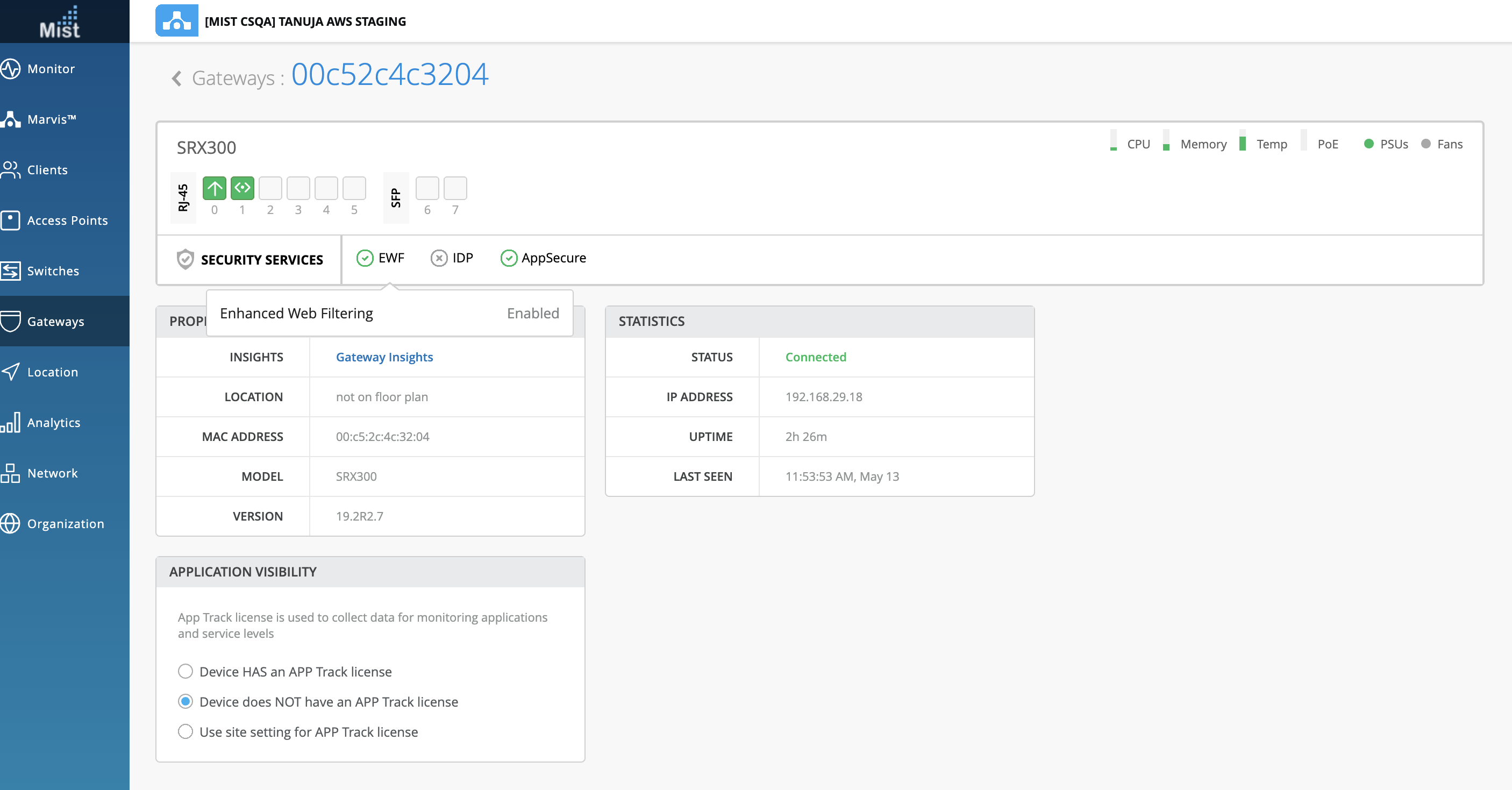
Once committed, if you run “show security utm web-filtering” in operational mode this will be represented by “ewf_status”
root@00c52c4c3204> show security utm web-filtering status UTM web-filtering status: Server status: Juniper Enhanced using Websense server UP root
If you see “Juniper Enhanced using Web-sense server UP” this means you can connect to the web-sense server, and you are using enhanced web filtering (EWF), meaning the service is enabled. This will then appear as enabled for “ewf_status” in the API as well as the UI.
Configuring IDP
Before configuring IDP you need to download and install the IDP security package using these steps:
- Download: ‘request security idp security-package download’
- Install: ‘request security idp security-package install’
For our purpose we’ll use a template for idp
- Download: ‘request security idp security-package download policy-templates’
- Install: ‘request security idp security-package install policy-templates’
1. Set up recommended IDP policy template and enable:
user@host-1# set system scripts commit file templates.xsl user@host-1# commit
user@host-1# set security idp default-policy Recommended user@host-1# set security idp active-policy Recommended user@host-1# commit
2. Use this command:
“set security idp idp-policy Recommended rulebase-ips rule 1 match from-zone any to-zone any source-address any destination-address any application junos-echo attacks predefined-attack-groups Critical”
3. Use the “show security idp policies” command in operational mode to see the Recommended idp policy.
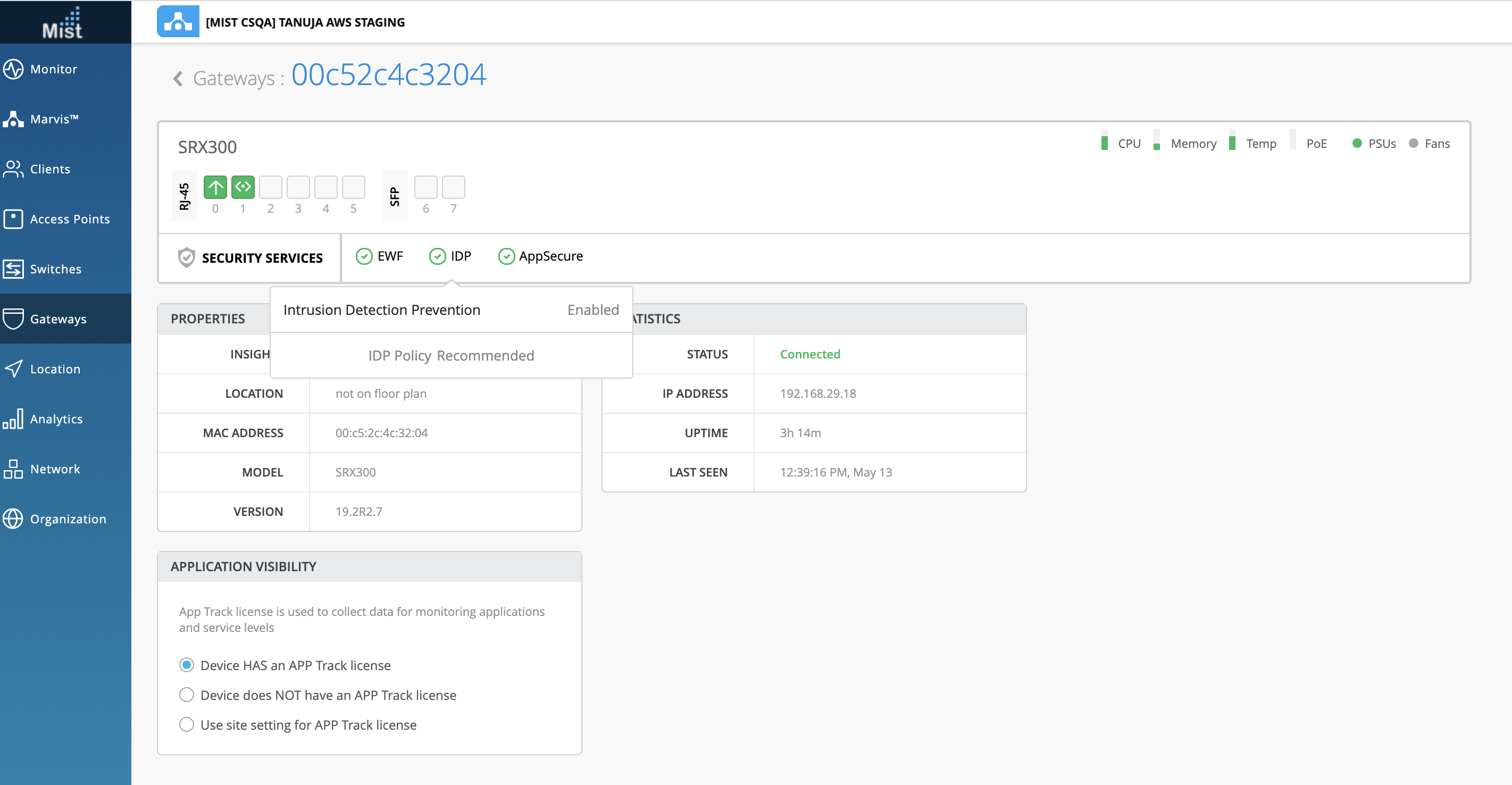
4. On the UI this corresponds to “idp_status” which will now be enabled, and “idp_policy” which will show as “Recommended”.
5. In the CLI, issue the command “show security idp policies“ to check the policy name
show security idp policies PIC : FPC 0 PIC 0: ID Name Sessions Memory Detector 0 Recommended 0 3197169 12.6.160200828
6. Issue the command “show security idp status“ to check the IDP Status
root@00c52c4c3204> show security idp status Intelligent Inspection State Details: State: Inactive State of IDP: Default, Up since: 2021-05-13 03:59:50 UTC (03:17:15 ago) Packets/second: 0 Peak: 0 @ 2021-05-13 07:06:22 UTC KBits/second : 0 Peak: 0 @ 2021-05-13 07:06:22 UTC Latency (microseconds): [min: 0] [max: 0] [avg: 0] Packet Statistics: [ICMP: 0] [TCP: 0] [UDP: 0] [Other: 0] Flow Statistics: ICMP: [Current: 0] [Max: 0 @ 2021-05-13 07:06:22 UTC] TCP: [Current: 0] [Max: 0 @ 2021-05-13 07:06:22 UTC] UDP: [Current: 0] [Max: 0 @ 2021-05-13 07:06:22 UTC] Other: [Current: 0] [Max: 0 @ 2021-05-13 07:06:22 UTC] Session Statistics: [ICMP: 0] [TCP: 0] [UDP: 0] [Other: 0] Policy Name : Recommended Running Detector Version : 12.6.160200828
Here is what the UI will look like:
Configuring App_Secure (Application_ID)
You don’t have to configure App_id/version, since app_secure will be enabled by default and oc-term makes sure our devices have the most up to date application_version. If you want to change the version/install a custom version, please refer to this document: