Network Programmability
Sponsored Guest Access WLAN
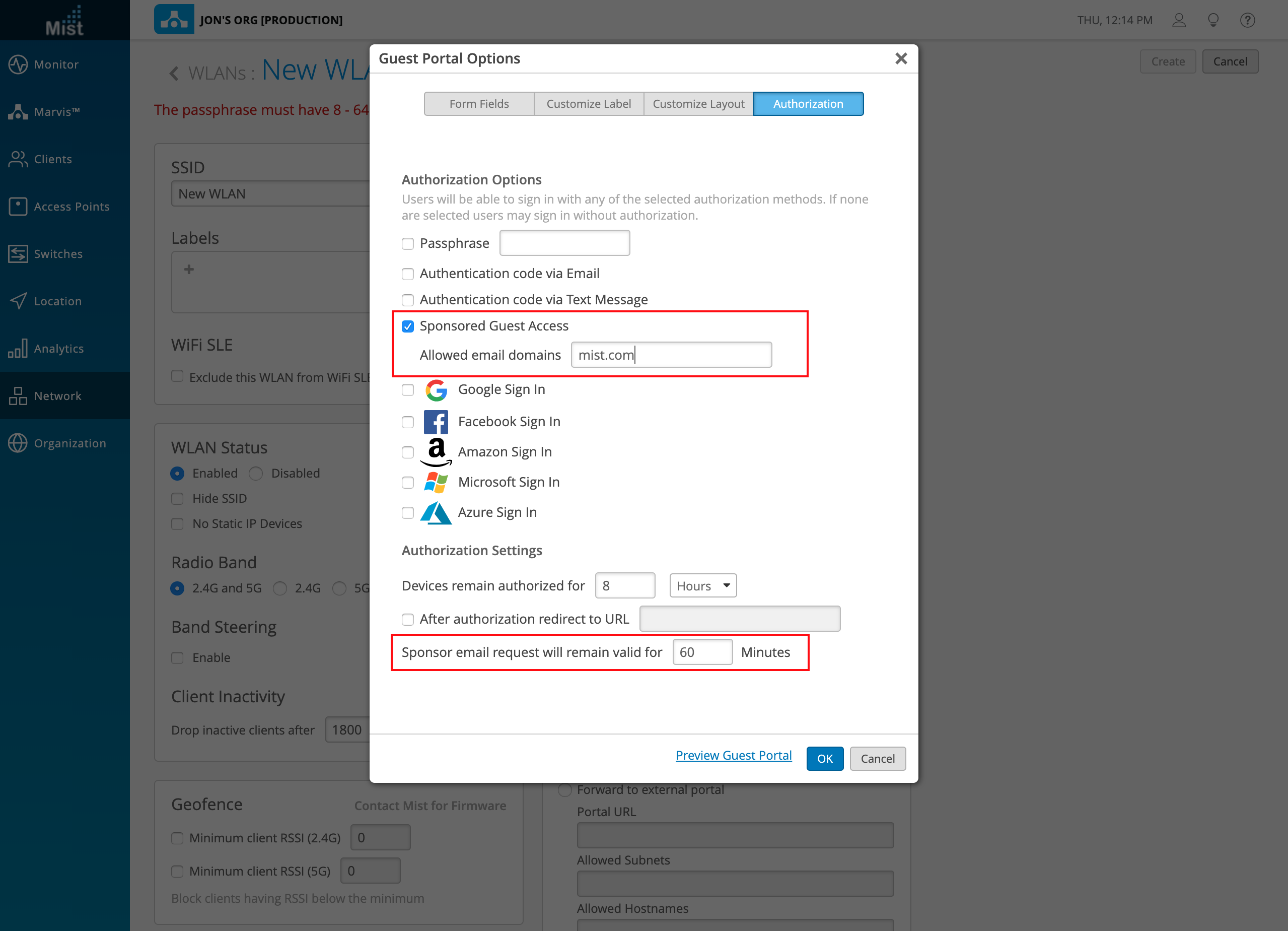
The Mist Captive Portal can be customized with a range of authorization options to cater to your specific needs as a network administrator. To improve its security capabilities we are introducing the option of adding a sponsored guest access authorization for users attempting to login using the portal. With sponsored guest access enabled, clients signing in to the portal need to be approved by a sponsor in order to successfully connect to the network. This will prevent unknown and unapproved users from connecting to your private guest WLAN.
To set up a sponsored guest access WLAN, navigate to Network > WLANs and select the Add WLAN button. Configure a Guest Portal and in the Authorization tab, select Sponsored Guest Access. Here, enter the email domain for the sponsors who will be approving the logins. You may customize the time window in which the sponsor needs to approve the login attempt – by default we have this set at 60 minutes.
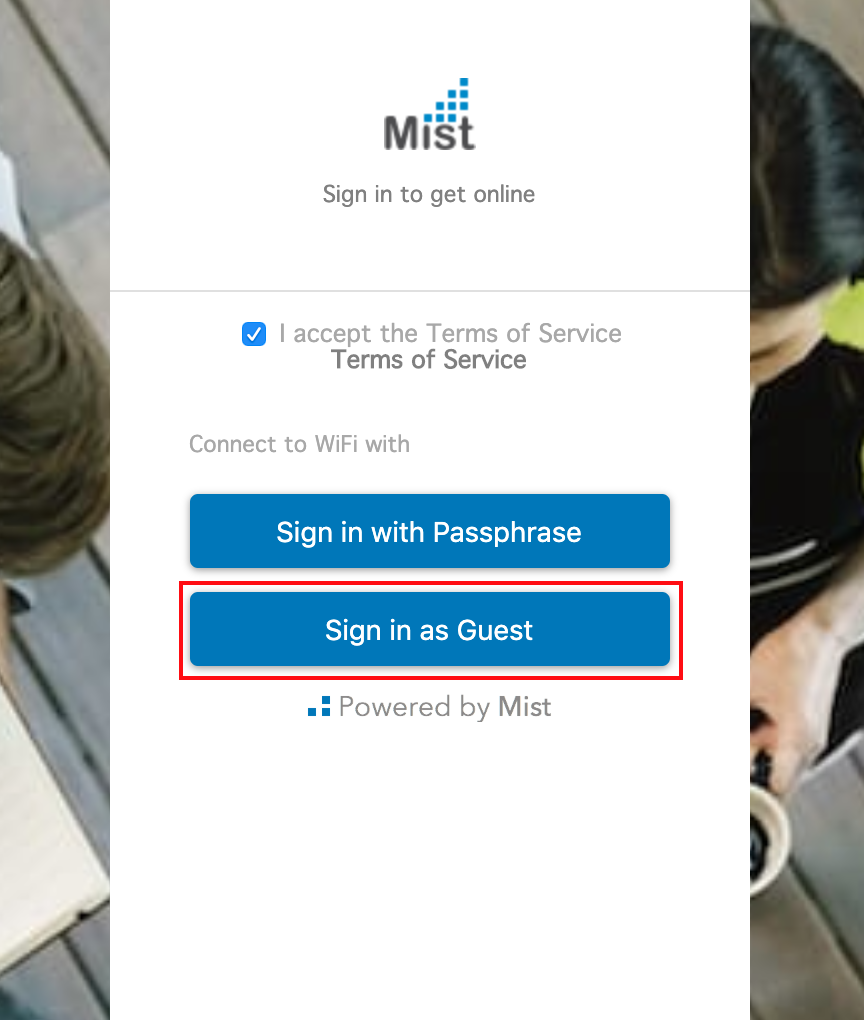
In a portal with multiple authorization methods set up, guests who need sponsor approval for login will select Sign in as Guest on the splash page. For portals without other authorization methods, the sponsored login page will be displayed by default. Fill in the required fields and select Notify Sponsor.
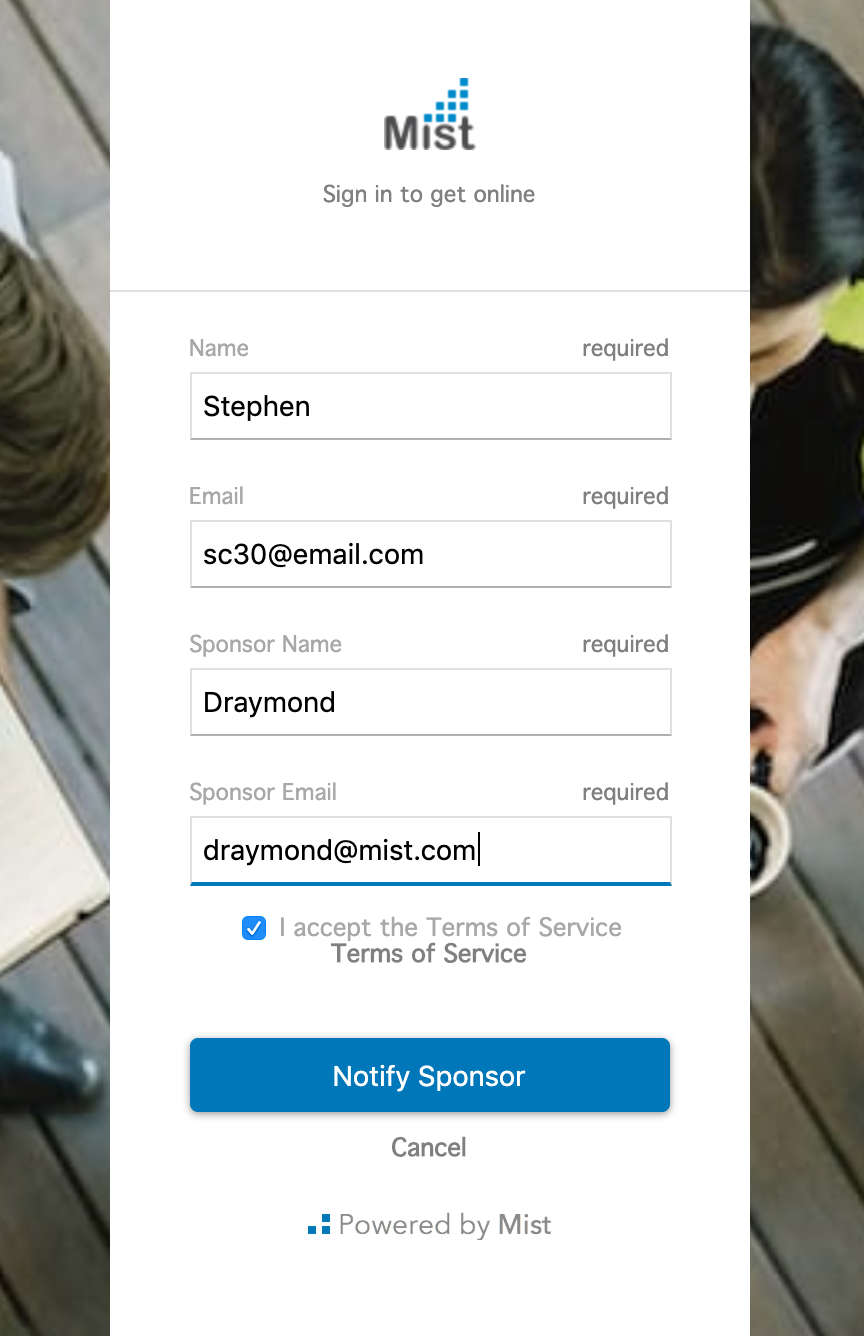
The sponsor will then receive an email requesting access for the user. Here, the sponsor can either accept or deny their request.
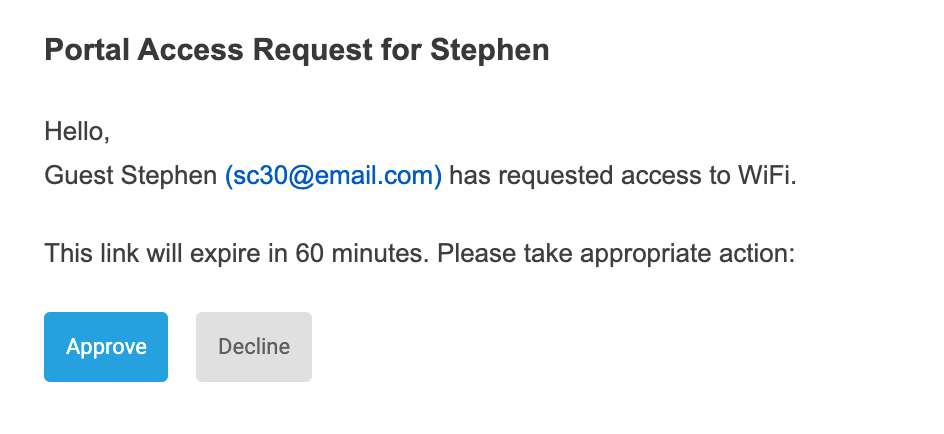
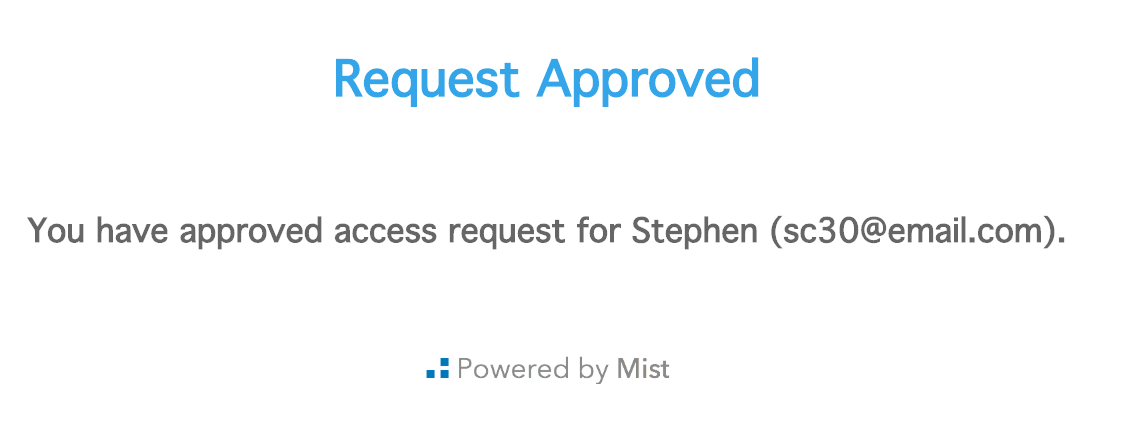
If accepted, the guest will now be approved and be automatically connected to the network.
Simplified Operations
Throughput SLE Improvements
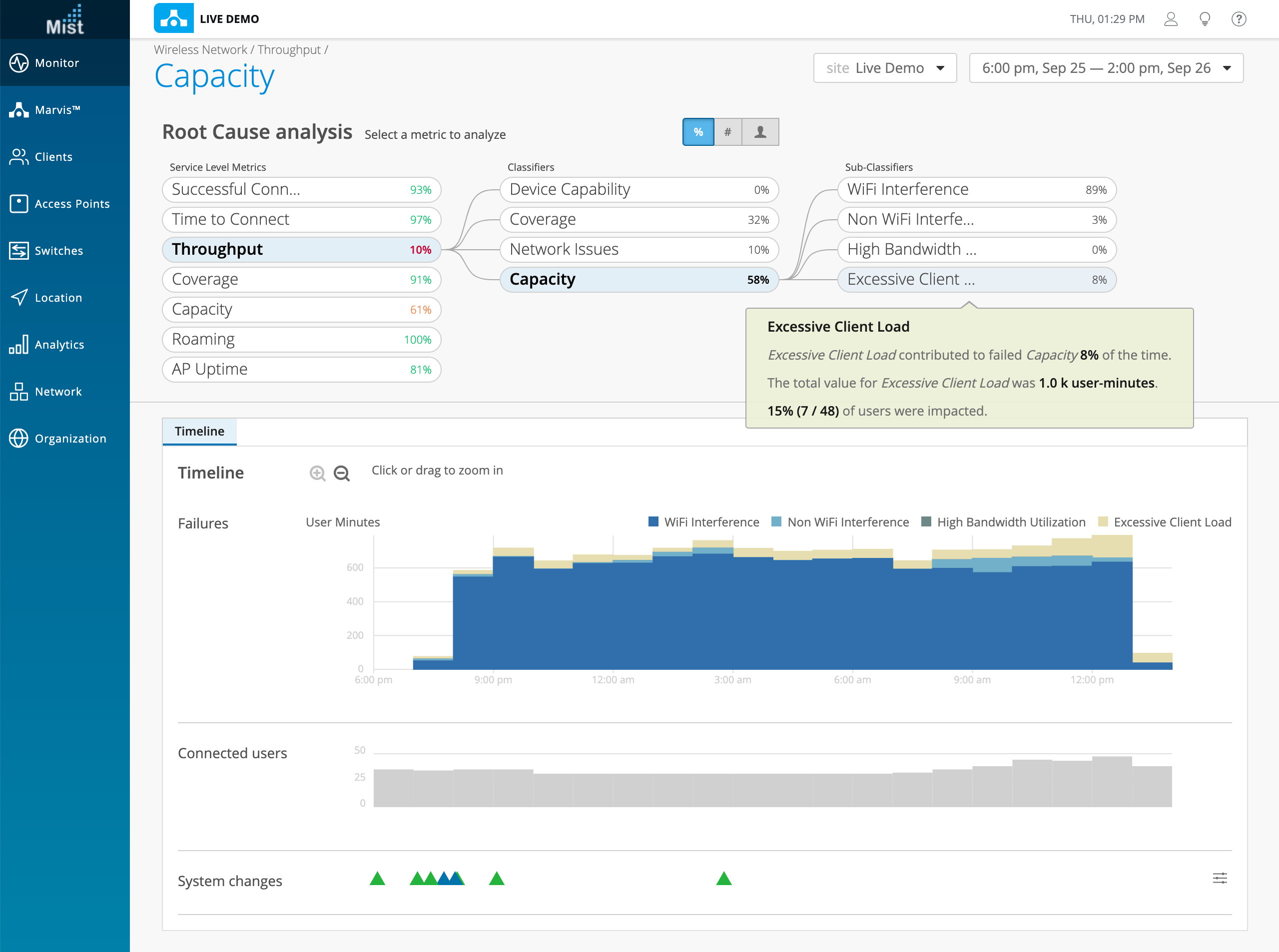
We have improved the data accuracy and visible information for our Throughput SLE Metric. The Capacity classifier can now be expanded to reveal four sub-classifiers to provide a more granular view into specific reasons for Capacity issues in your Throughput metric. The sub-classifiers for Throughput > Capacity are:
- WiFi Interference
- Non WiFi Interference
- High Bandwidth Utilization
- Excessive Client Load
In these sub-classifiers, you may examine Users and Access Points below the service level goal, the Timeline of failures and system changes, as well as the distribution of failures and affected items relating to the sub-classifier.