Pre-requisites:
- Microsoft Server 2012
- Active Directory Domain Services (ADDS)
- Active Directory Federation Services (ADFS)
- Active Directory Web Server (IIS) (for local testing)
- Mist Organization with Single Sign-on enabled
Steps:
- Launch the ADFS Management console
- Add Relying Party Trust, located under “AD FS > Trust Relationships > Relying Party Trusts”
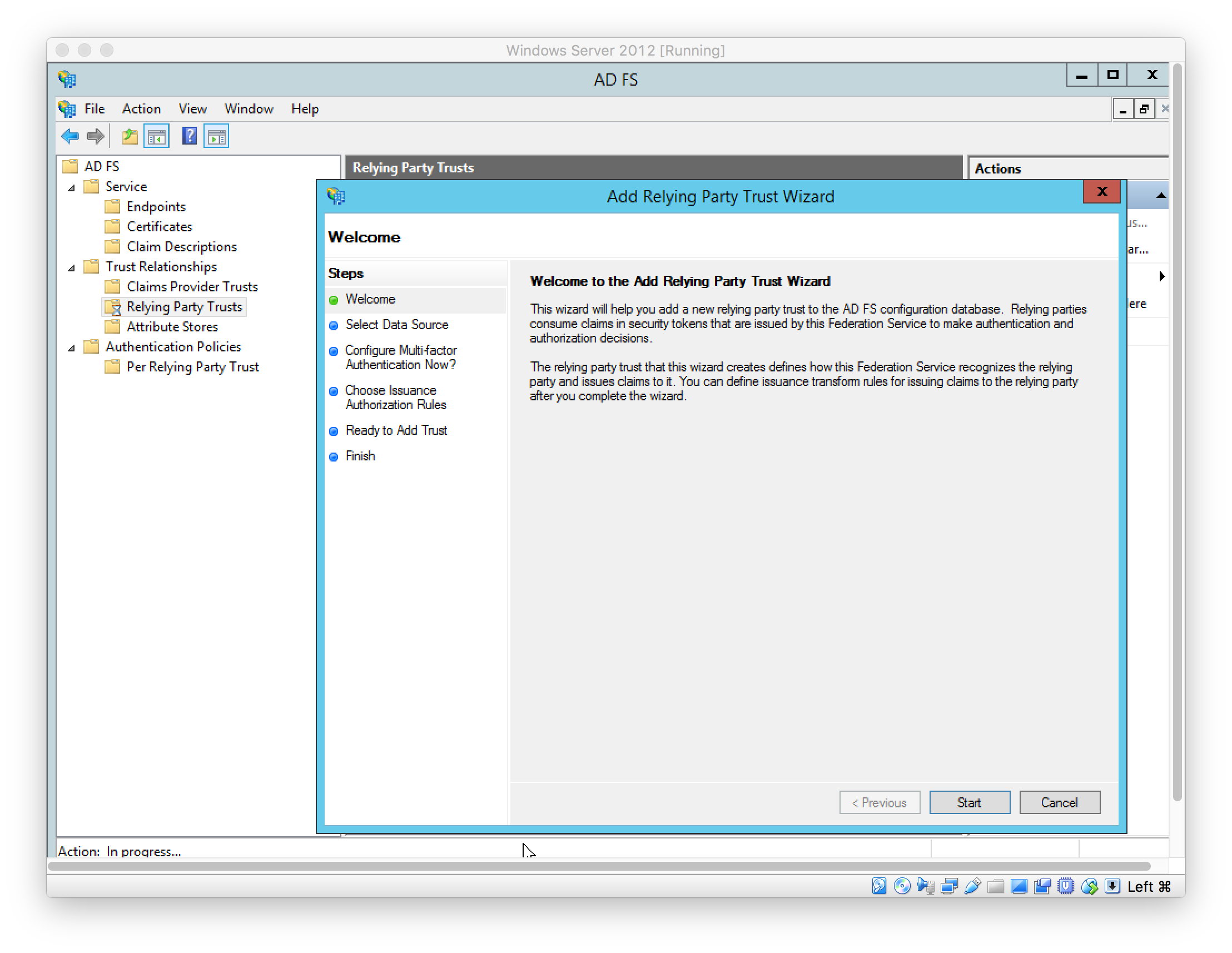
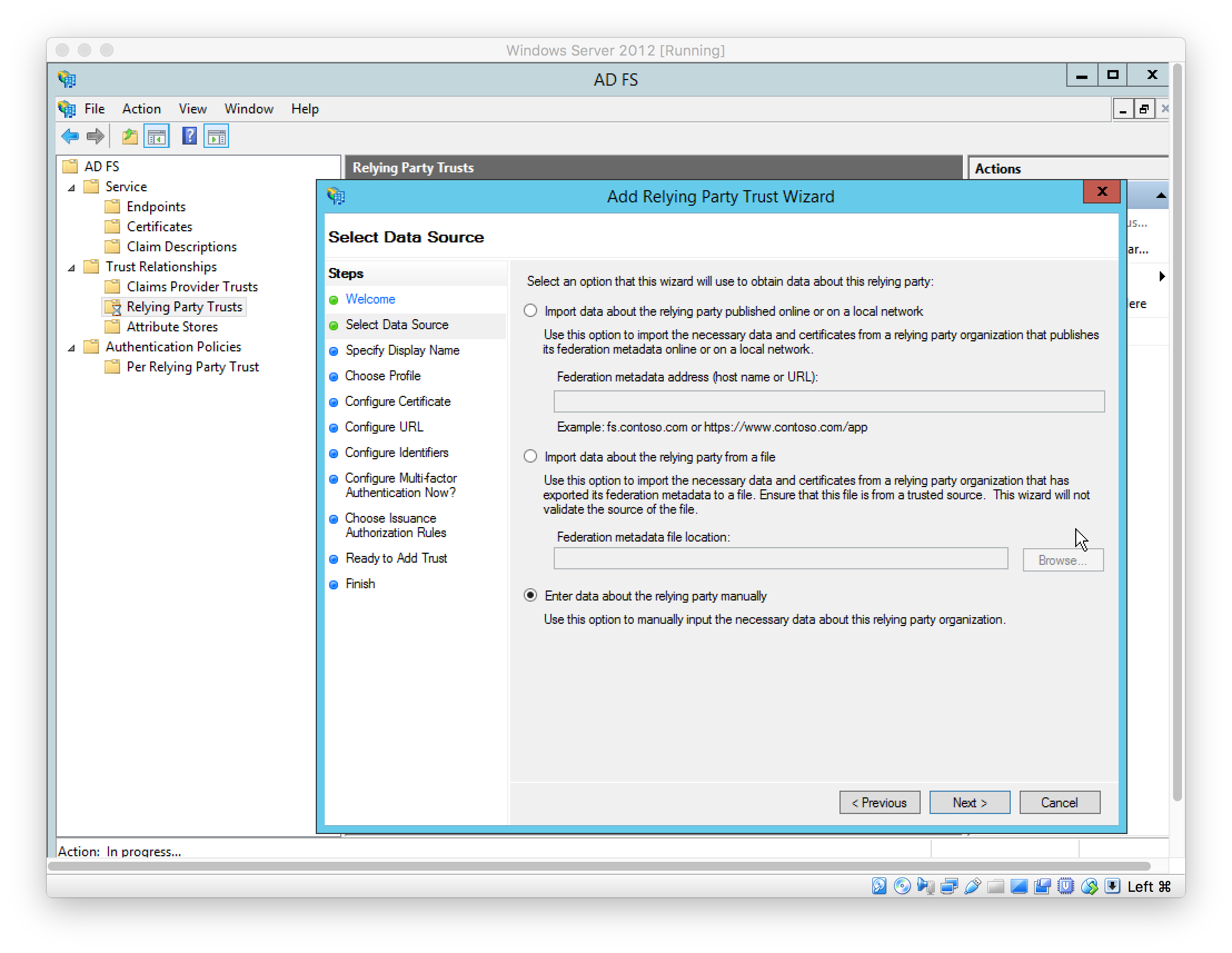
Select data source used to obtain data about the relying party
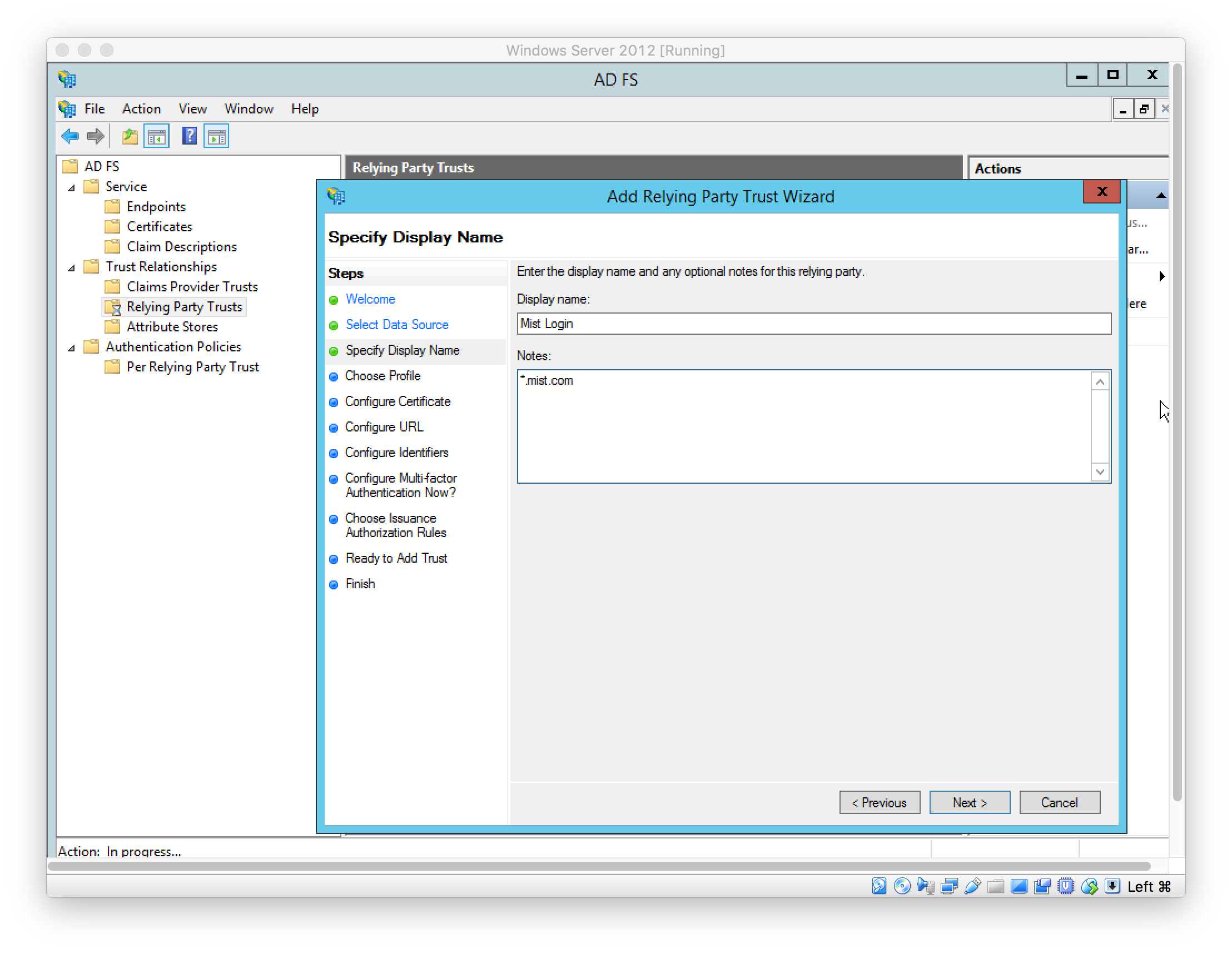
Set display name
Choose ADFS profile (left as default)
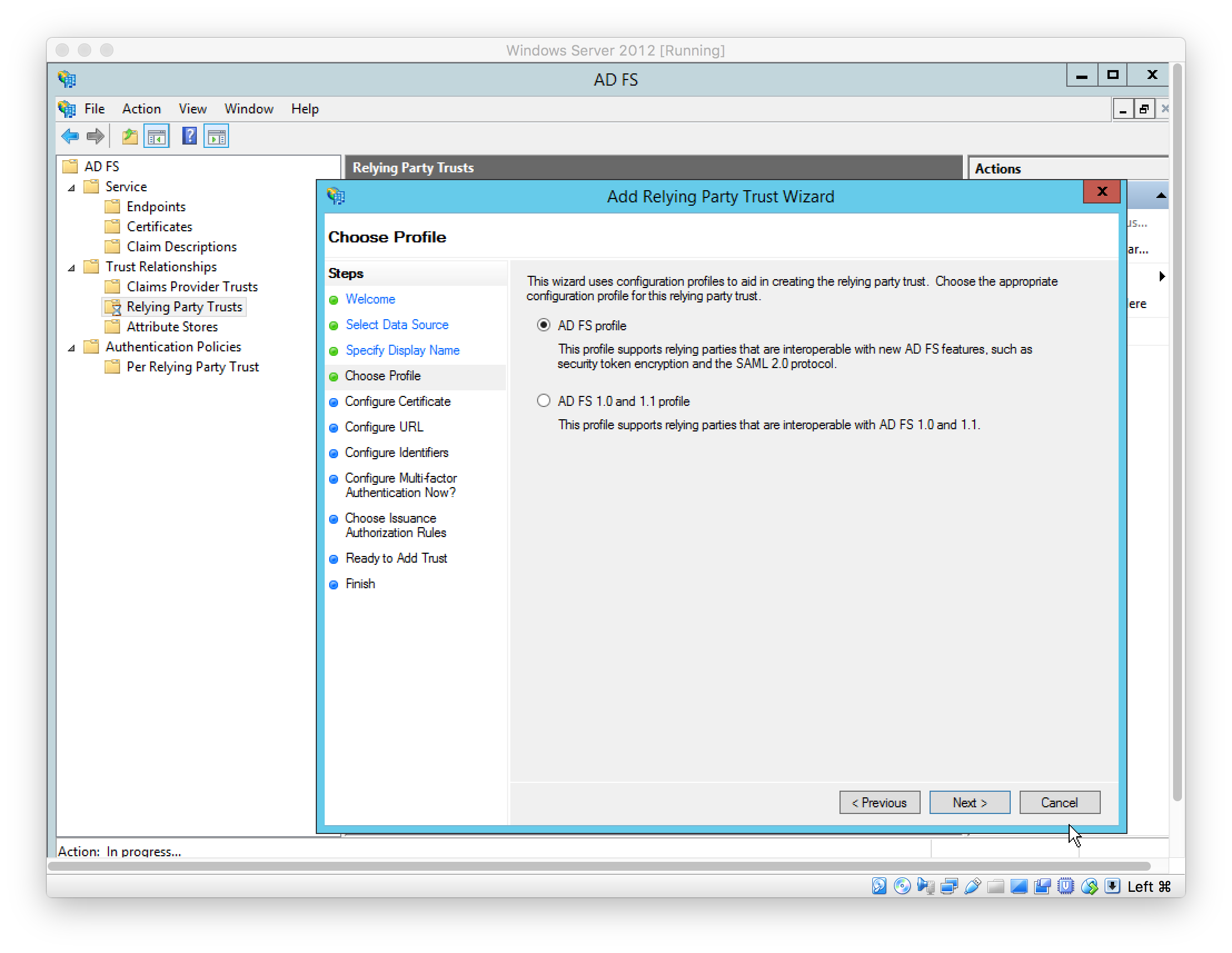
Configure optional token encryption certificate (left as default)
In Mist, add IDP under “Organization > Settings”
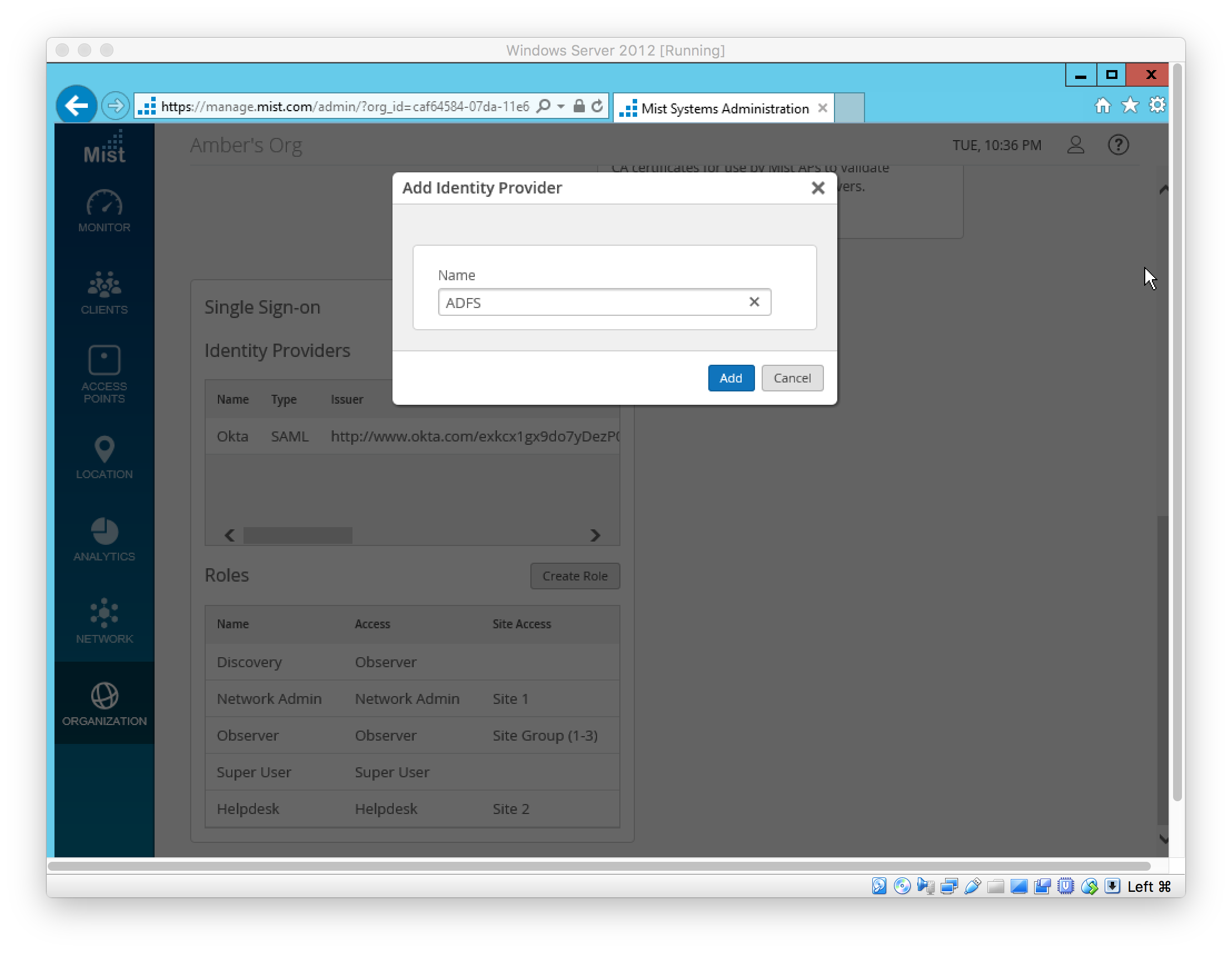
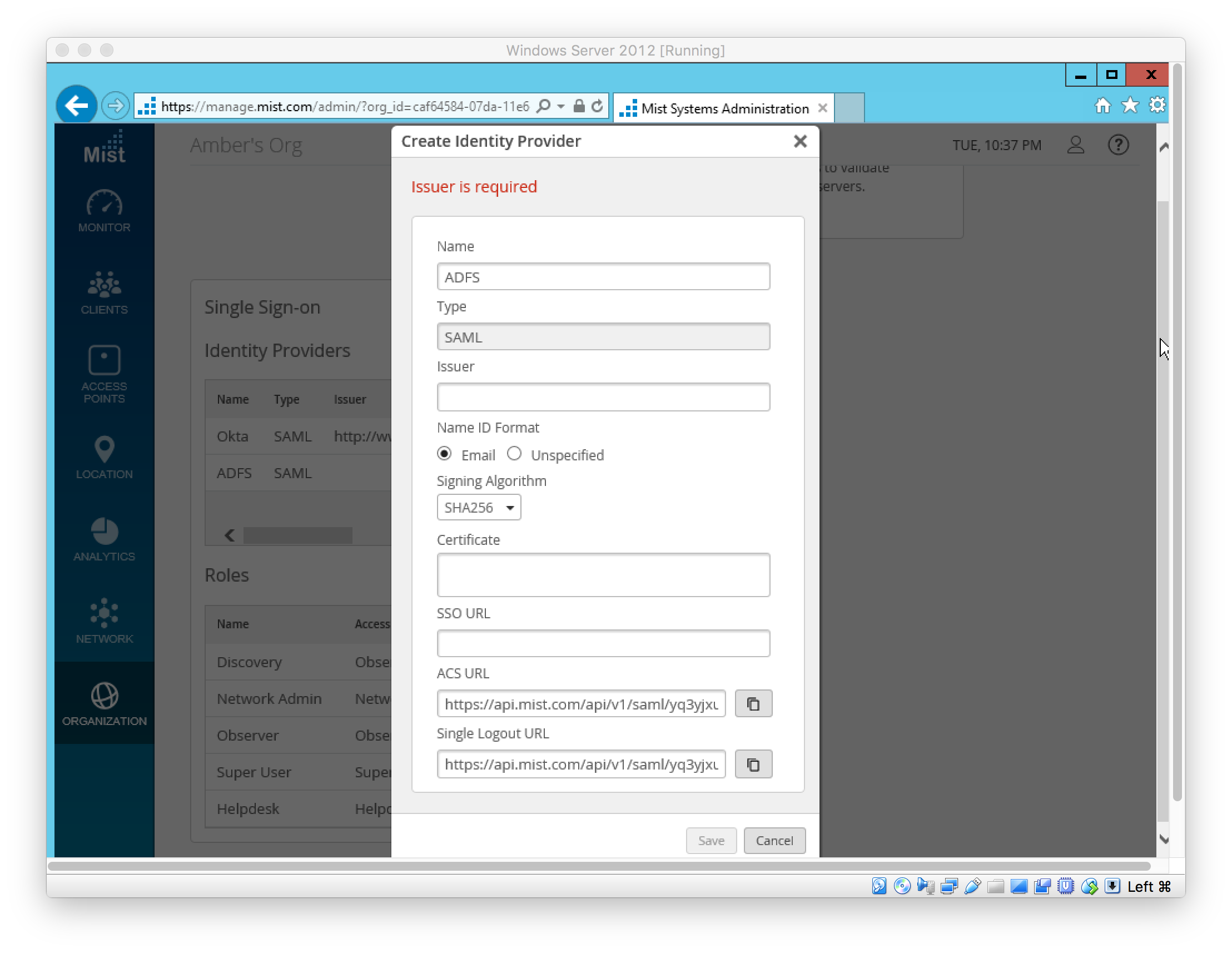
In ADFS, set SAML 2.0 SSO Service URL; this is the Mist IDP’s “ACS URL” (see above)
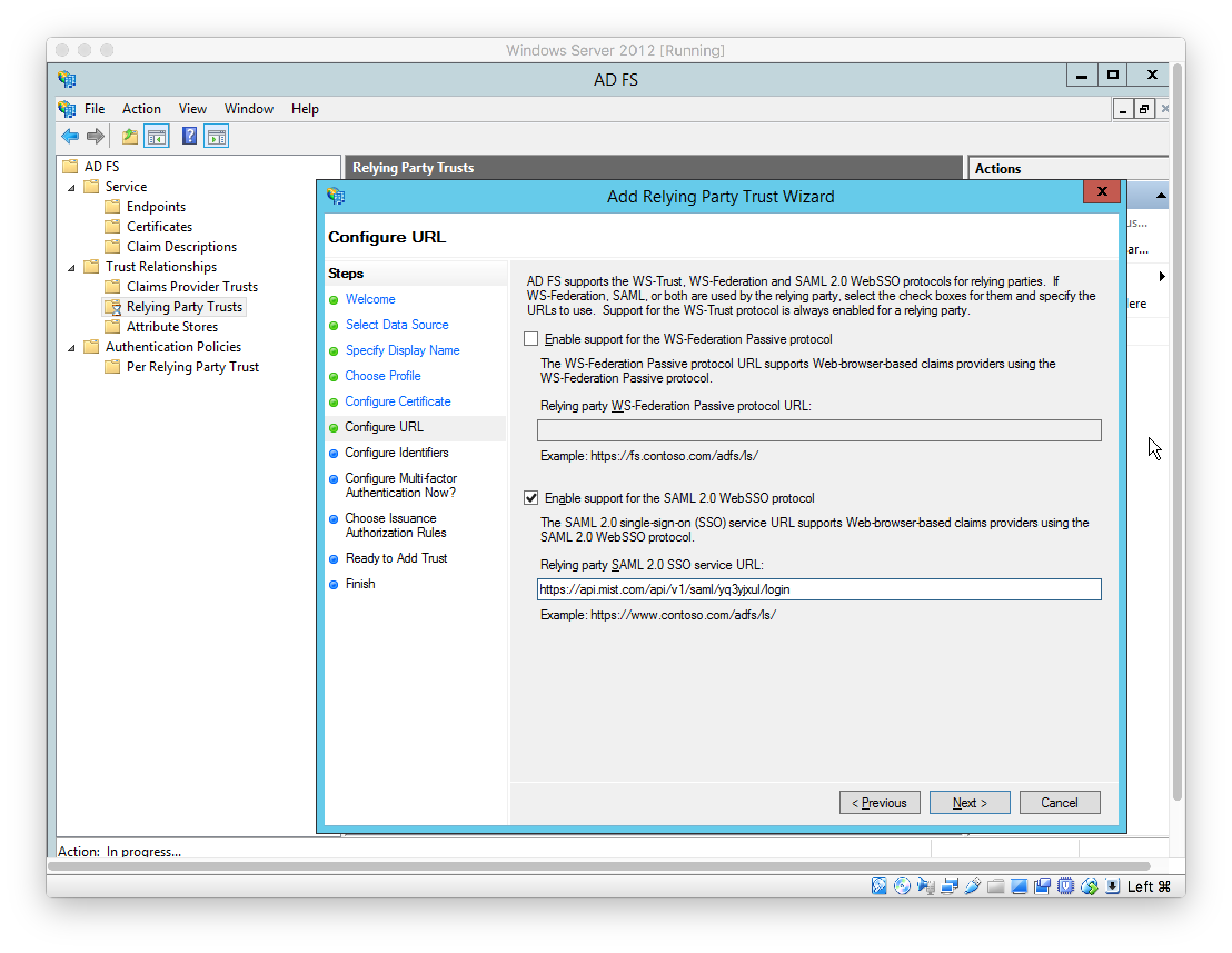
Set Relying Party Trust identifier
Set multi-factor authentication configurations (left as default)
Configure authorization rules (left as default)
Finish adding Relying Party Trust
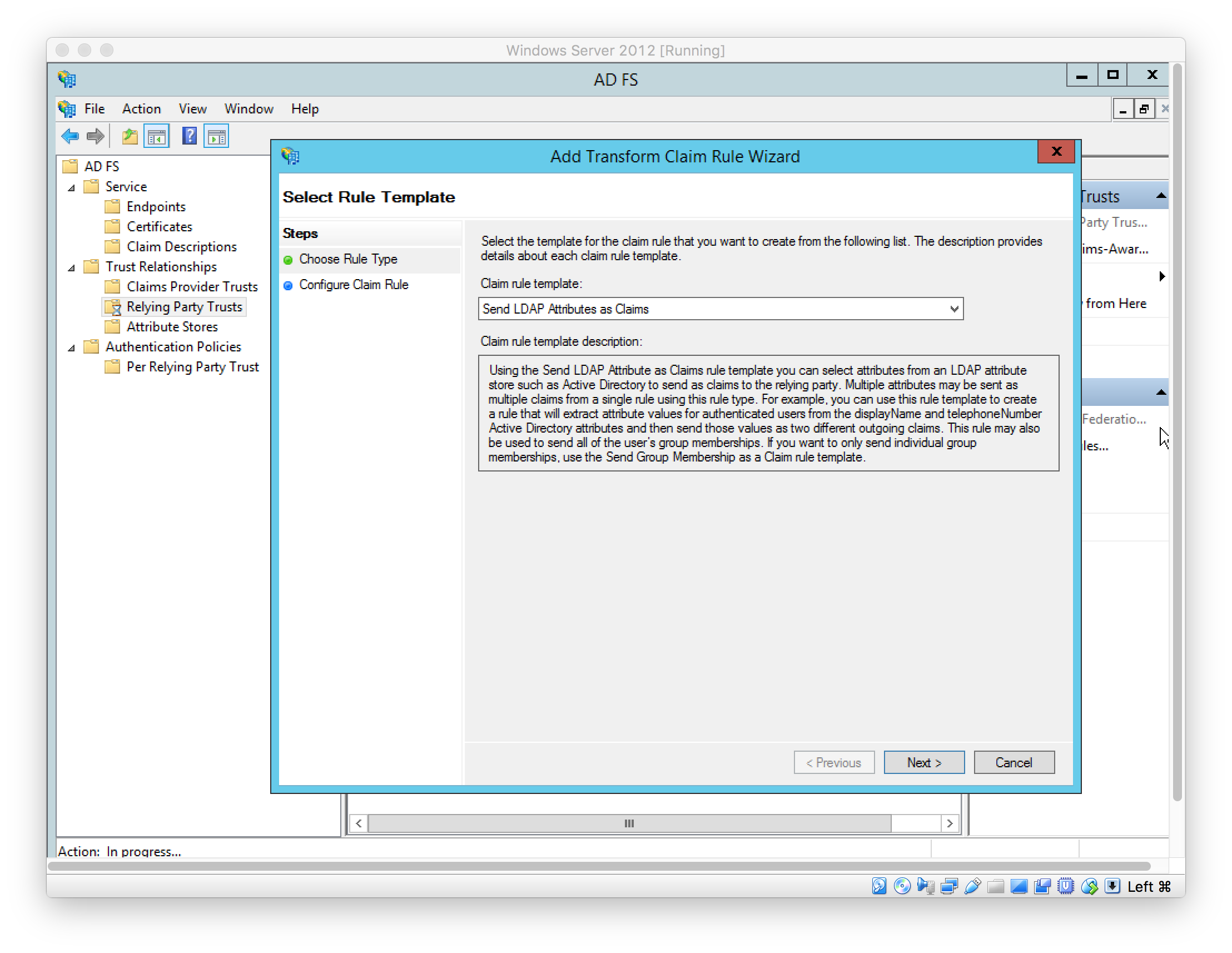
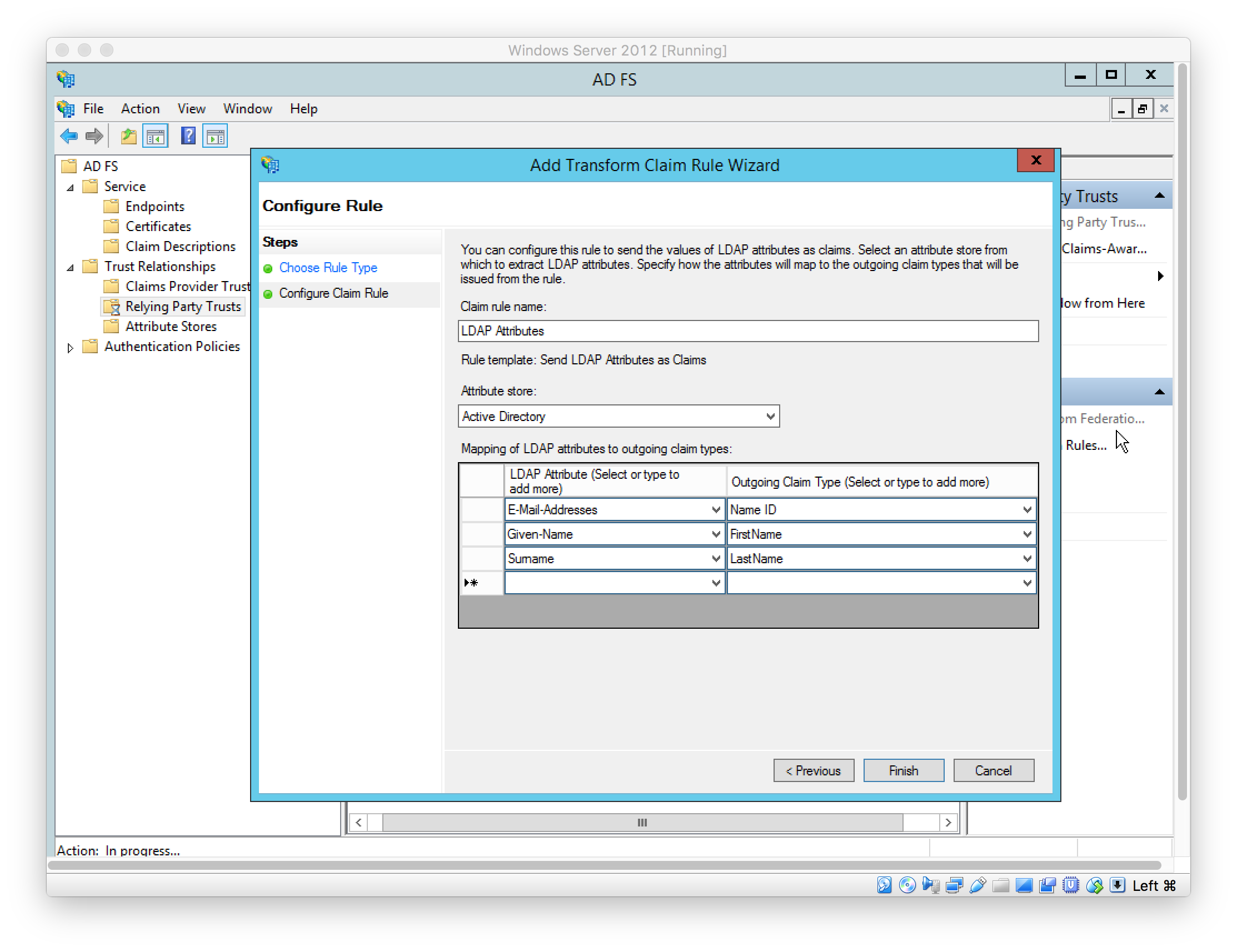
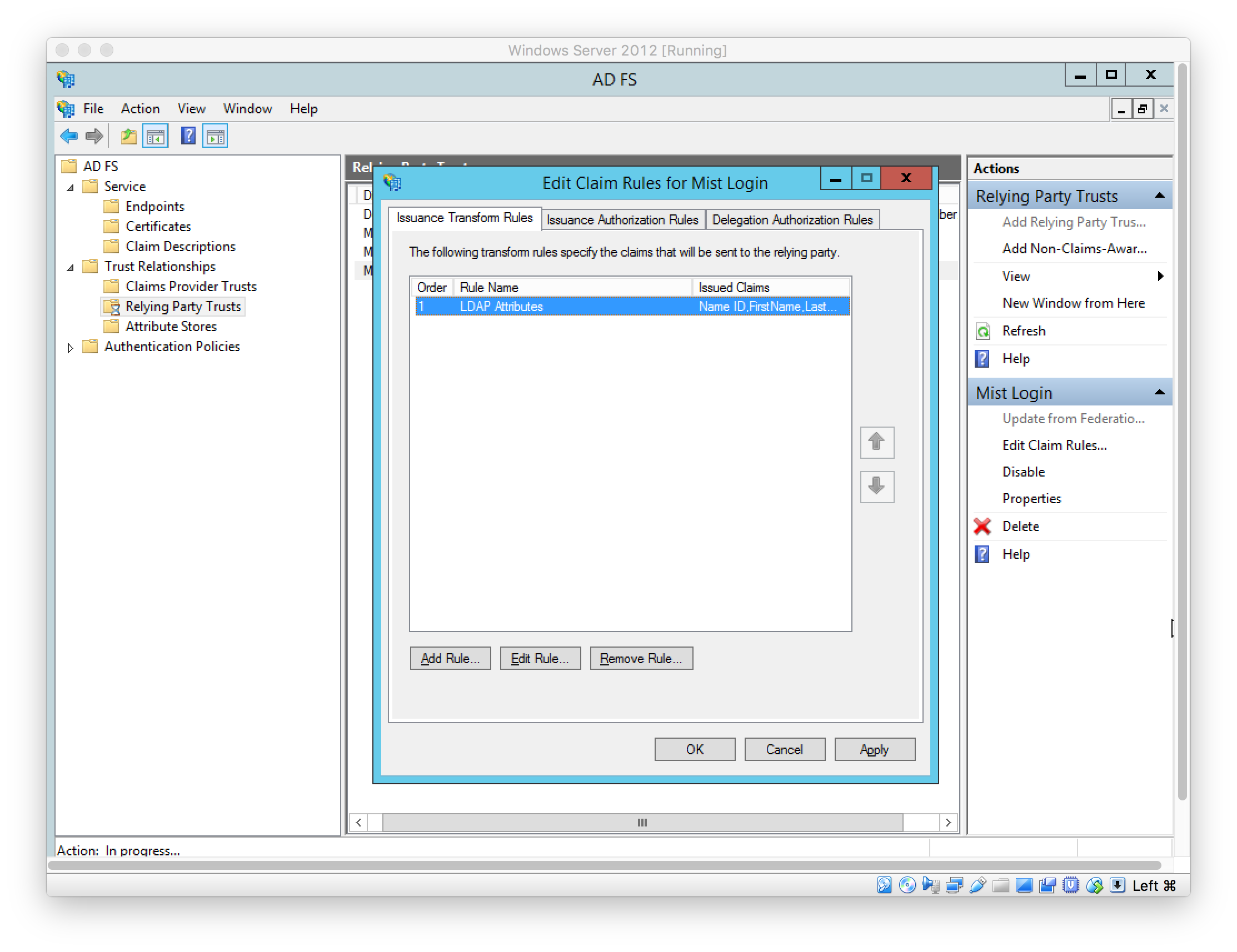
Add Claim Rules to send case-sensitive LDAP Attributes: Name ID, FirstName, LastName, and Role
In this example, the AD User fields “First name” (givenName), “Last name” (surname), and “Department” (department) are used to source these values respectively. See later step for the user setup.
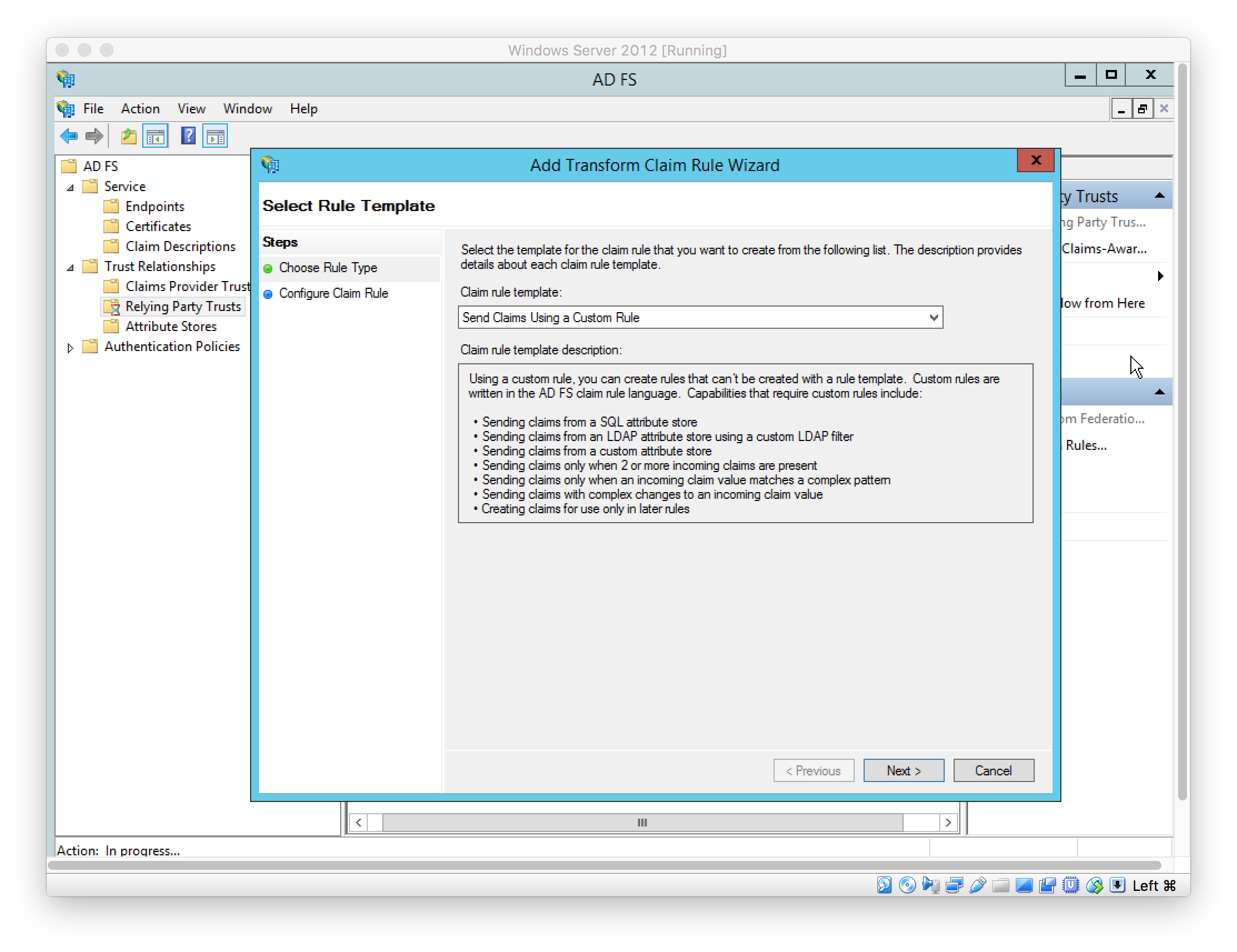
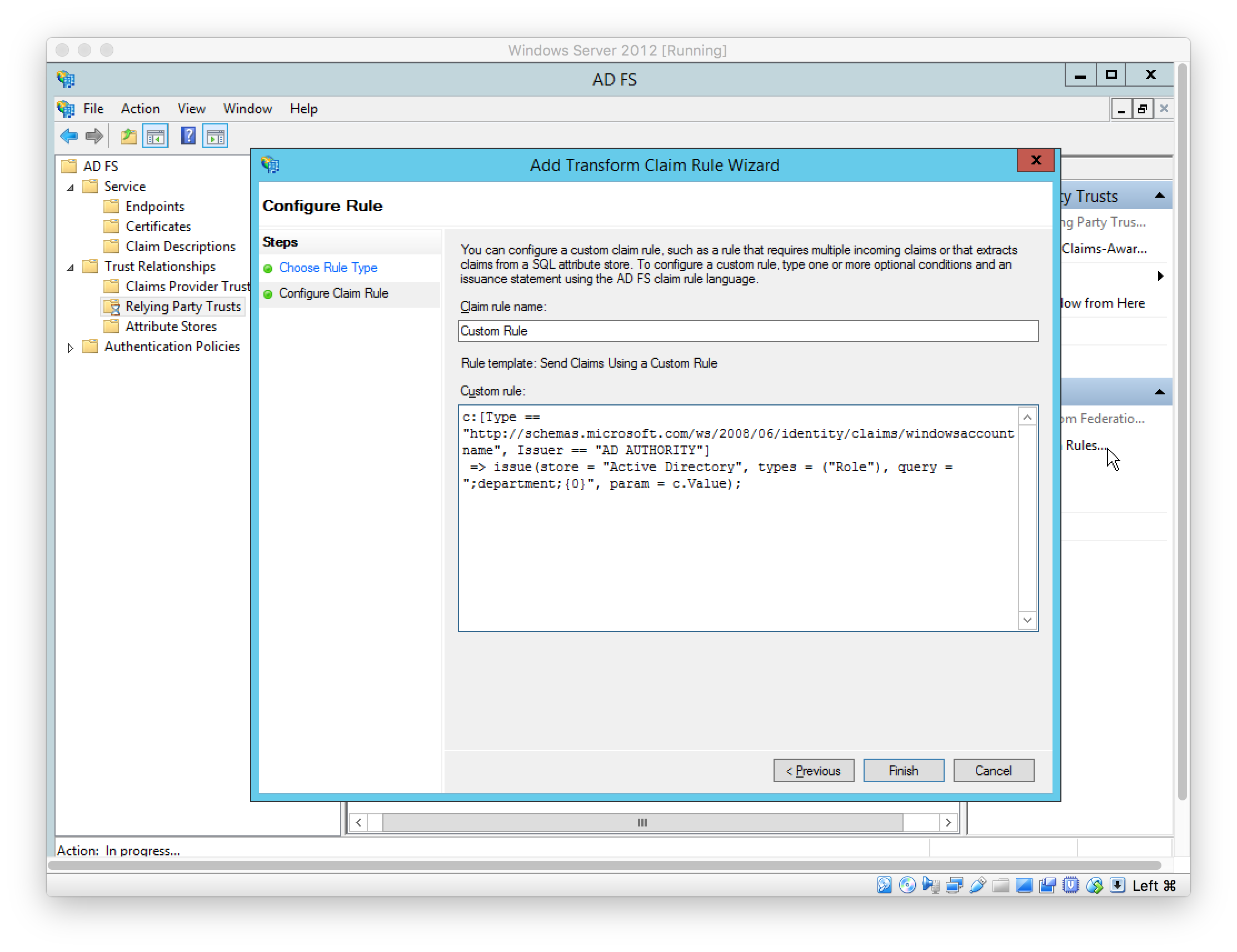
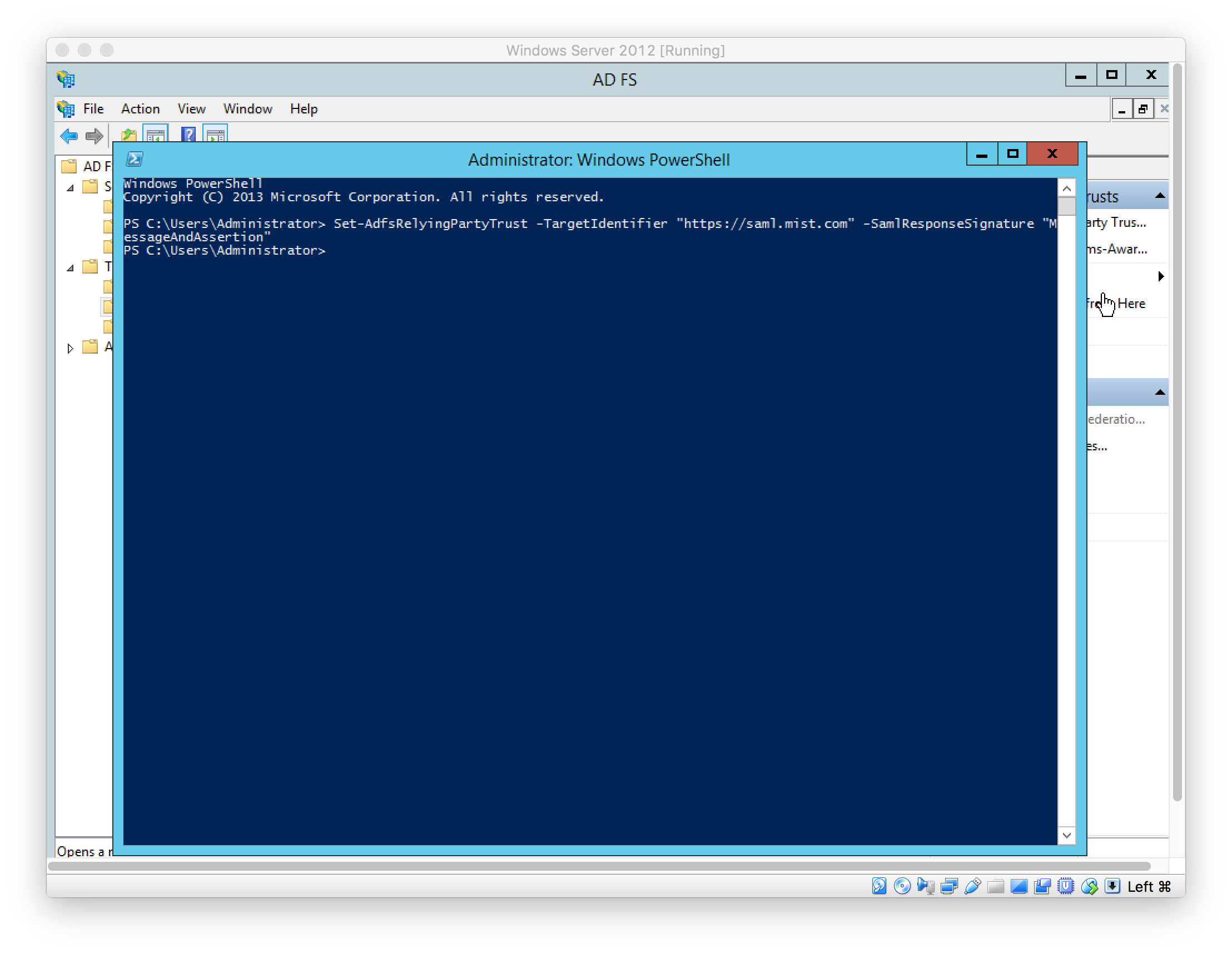
In Windows PowerShell, configure the ADFS Relying Party Trust to sign the message and assertion using the following command:
Set-AdfsRelyingPartyTrust -TargetIdentifier “https://saml.mist.com” -SamlResponseSignature “MessageAndAssertion”
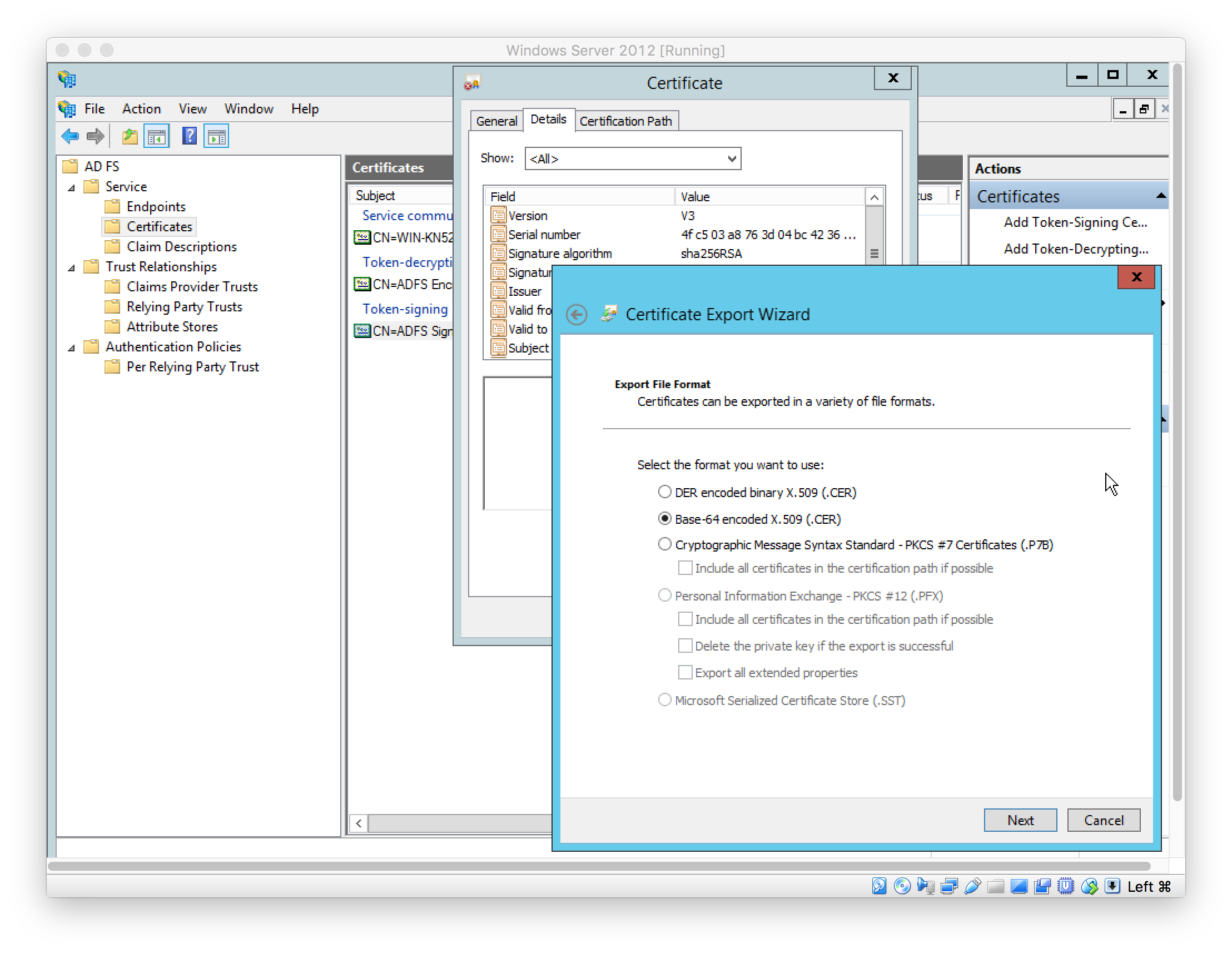
Download Token-signing certificate under “AD FS > Service > Certificates”
In Mist, set the IDP details; Certificate is the exported Token-signing certificate (see above)
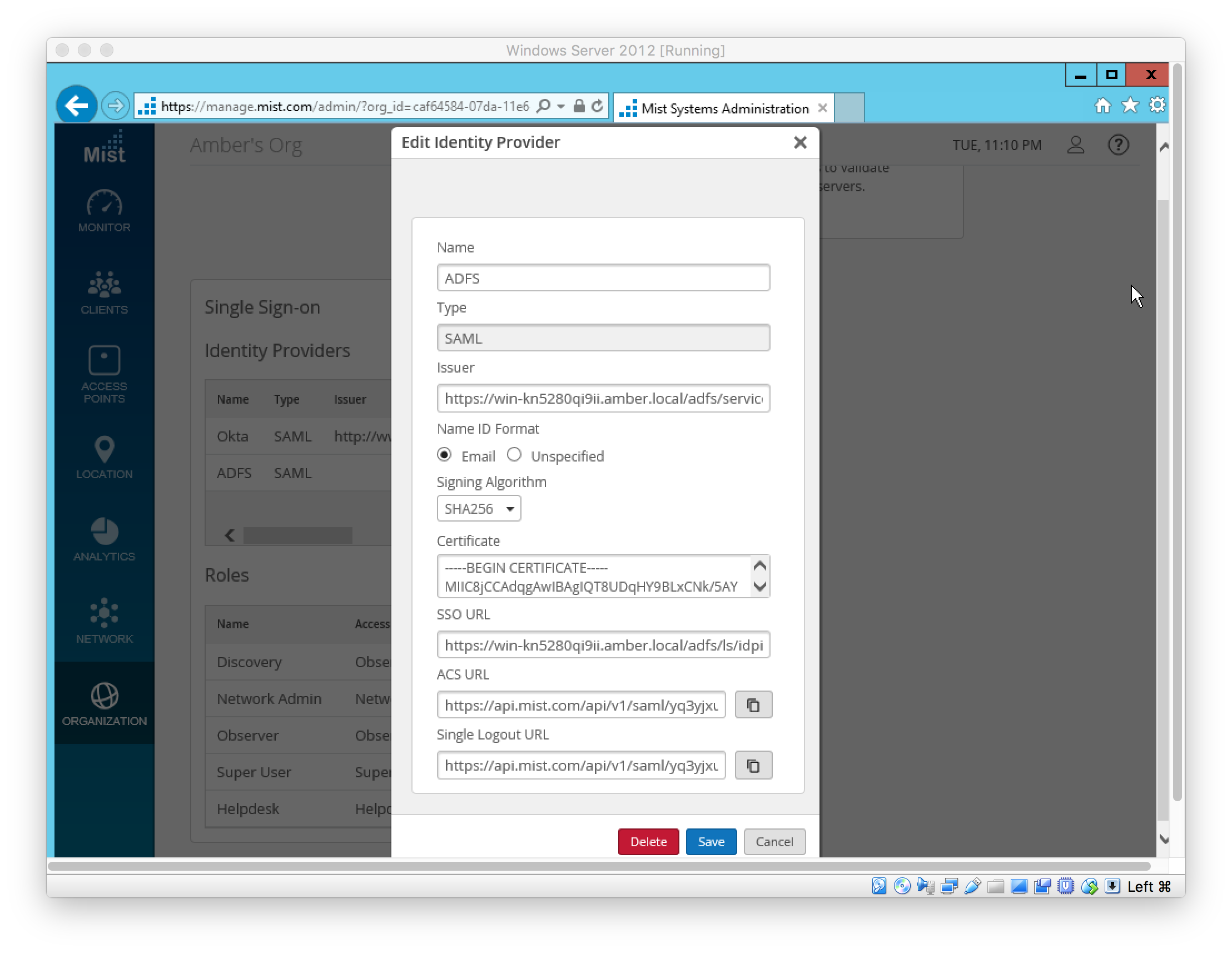
In Active Directory Administrative Center, create users
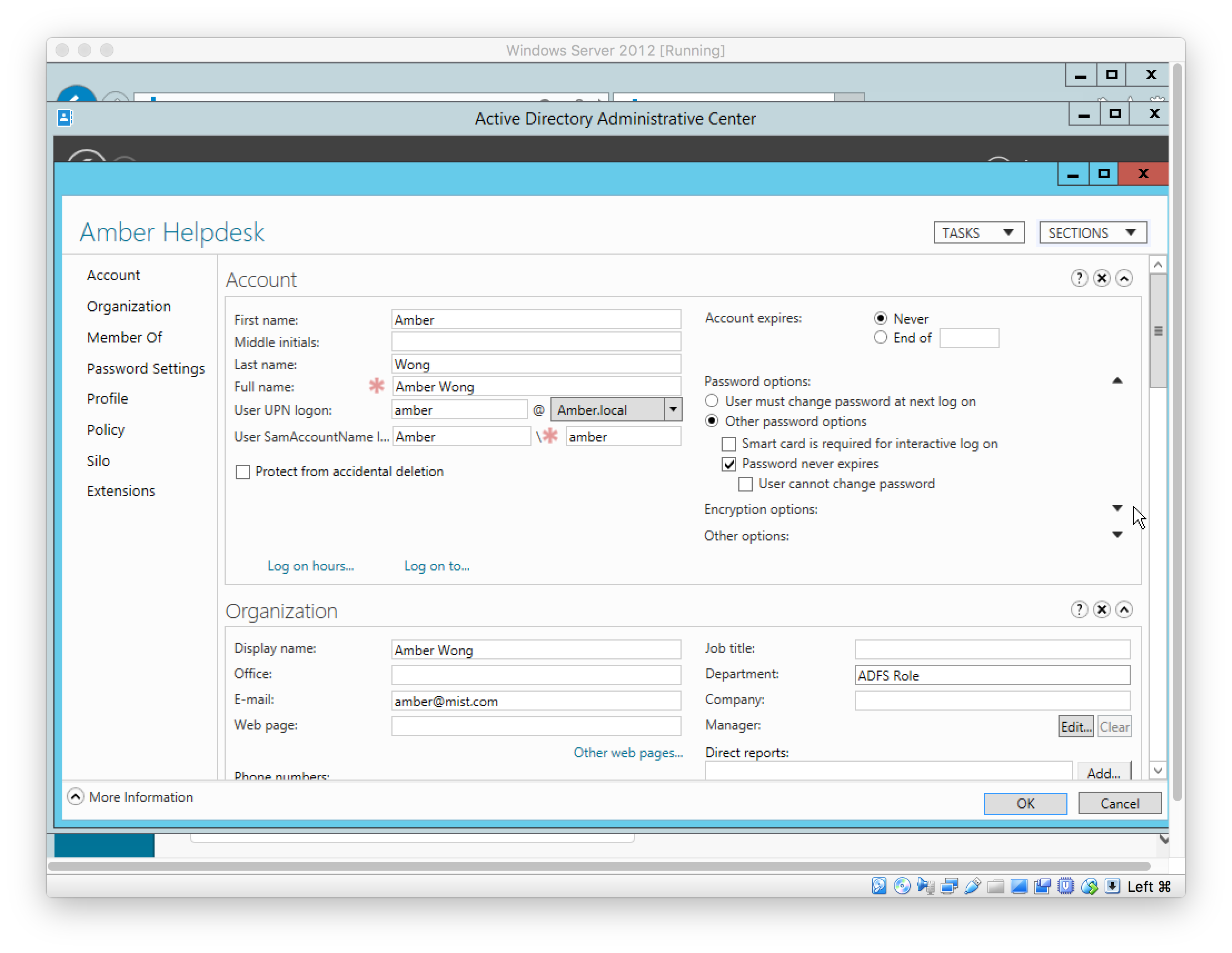
In Mist, create SSO Role to be used by SSO Admin(s). The AD User’s role must match the SSO Role’s “Name”.
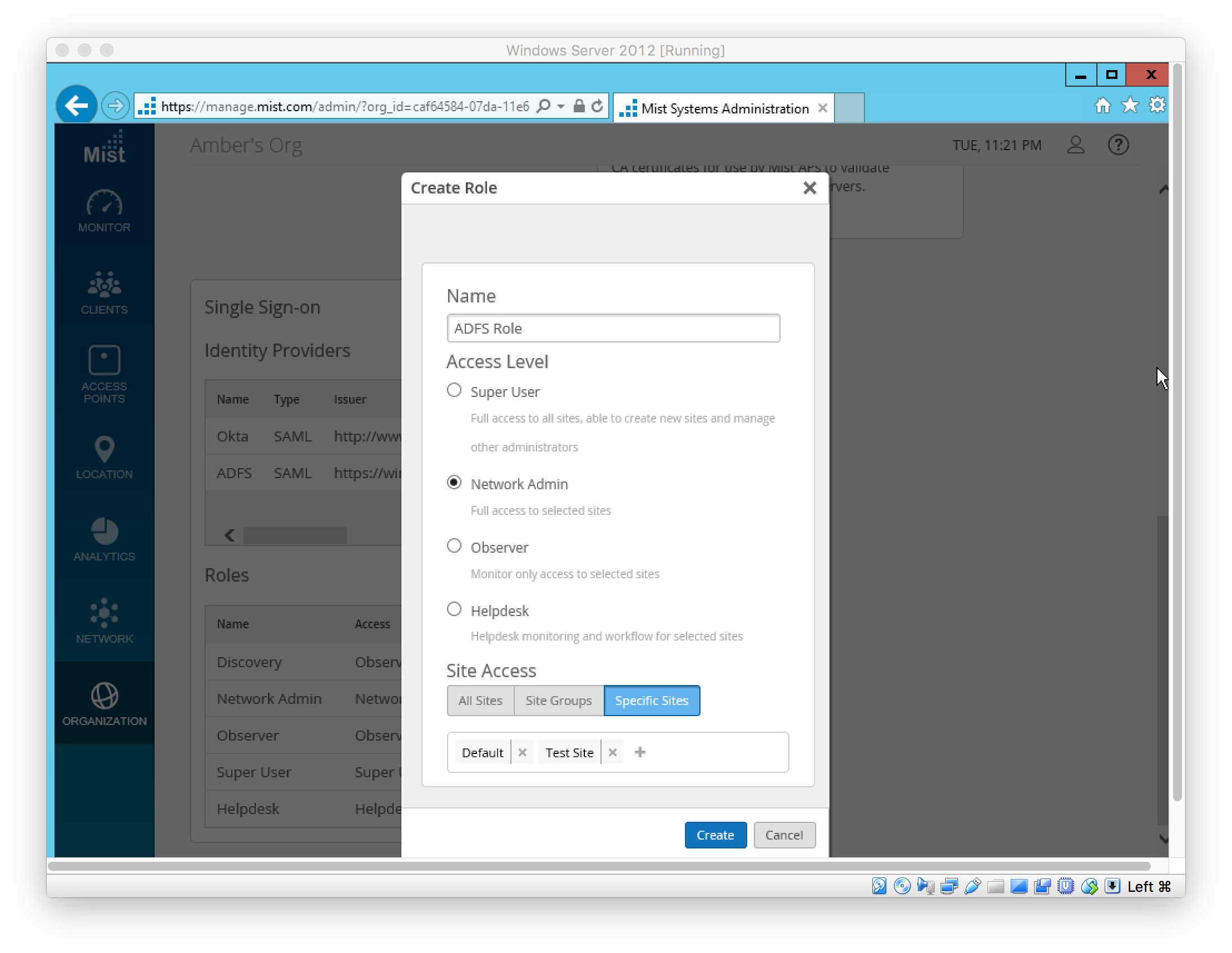
SSO Admin(s) can sign in using the SSO URL
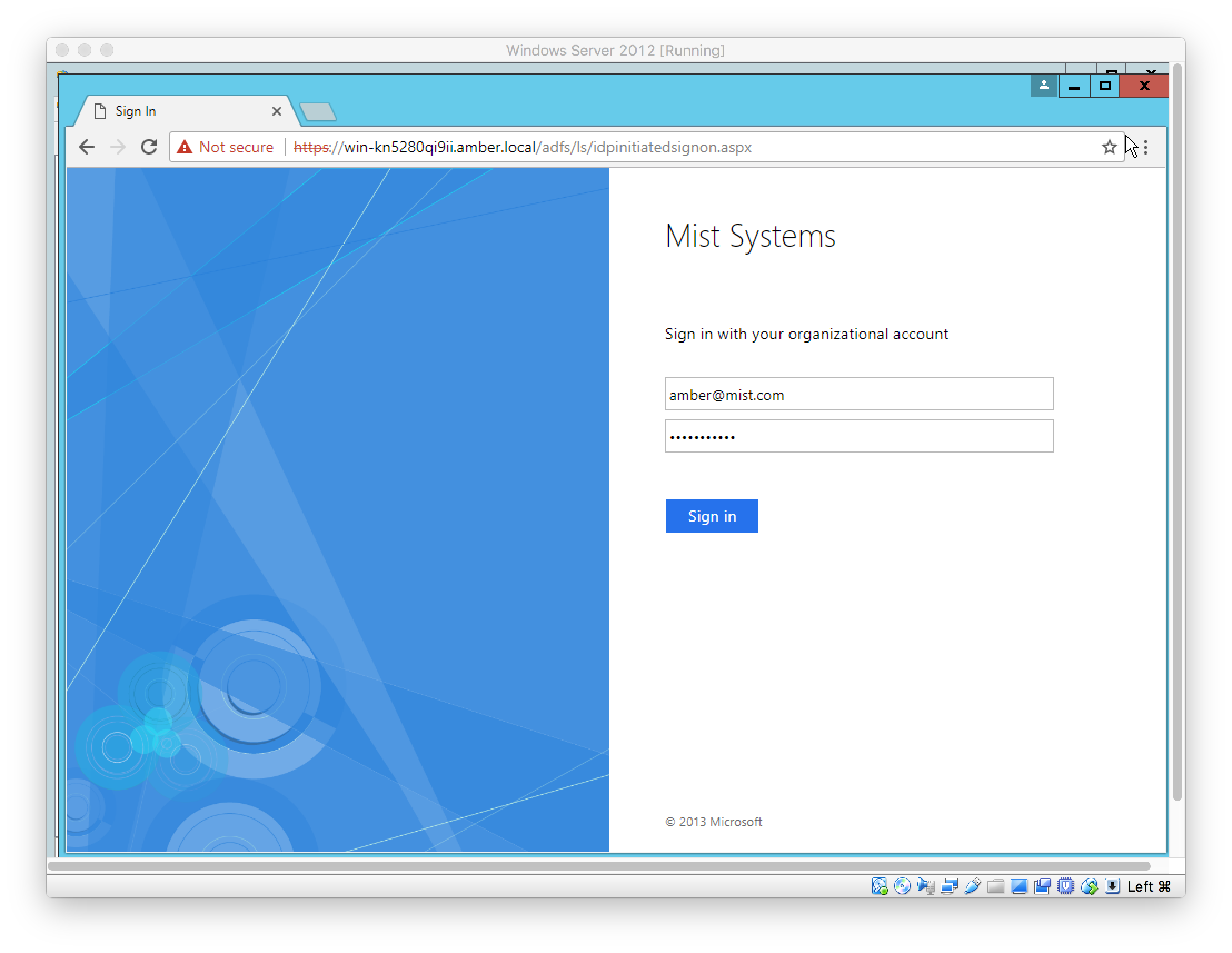
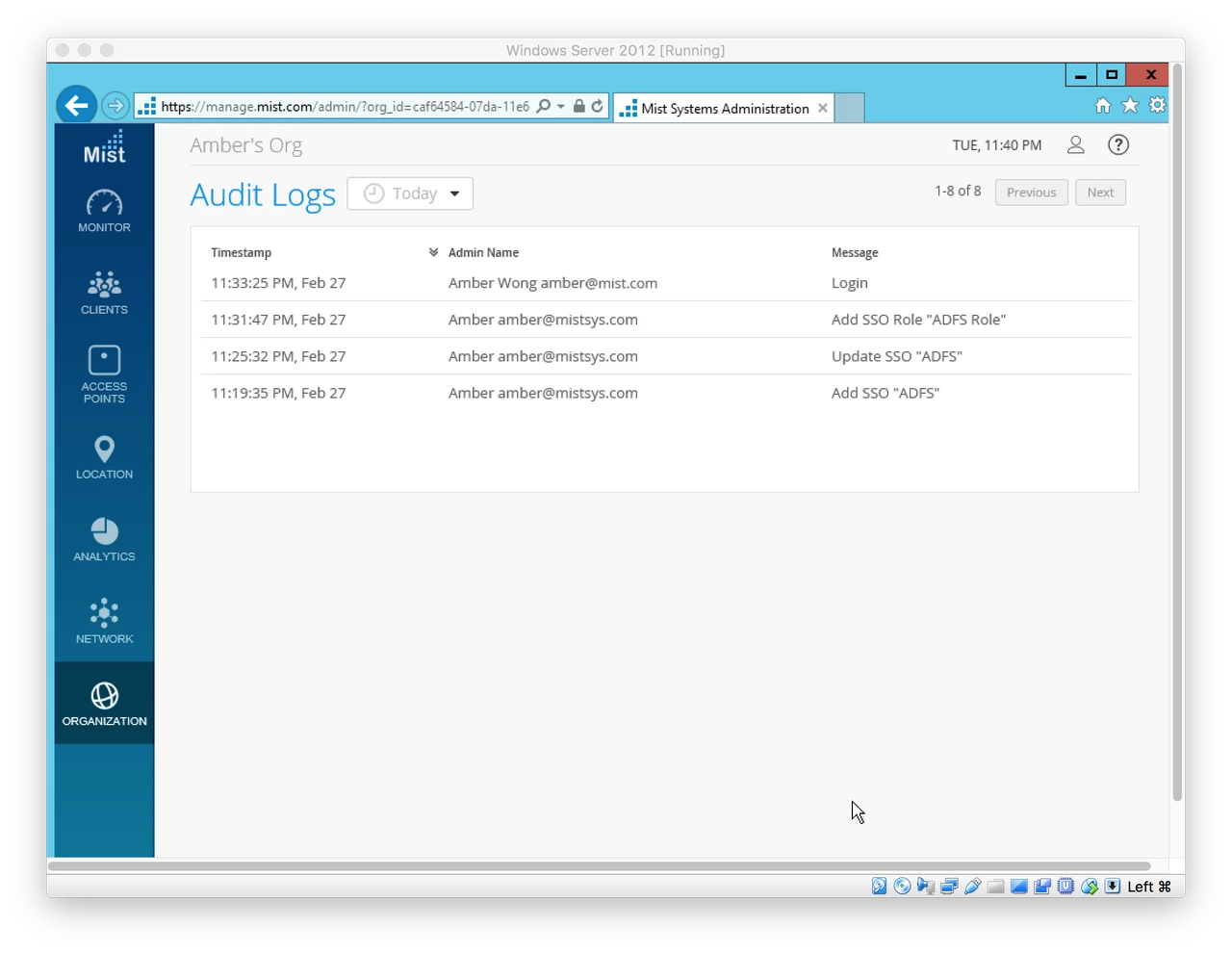
See SSO Admin logins are tracked under “Organization > Audit Logs”