Overview
Mist Access Assurance allows you to integrate our authentication service natively into Microsoft Entra ID (formerly known as Azure Active Directory) using OAuth. How can you leverage Entra ID as Identity Provider in combination with Mist Access Assurance?
- User authentication via EAP-TTLS
- Authenticate User by doing delegated authentication checking username and password via OAuth
- Obtain user group memberships to leverage them in Auth Policies
- Obtain user account state information (active / suspended)
- User authorization via EAP-TLS or EAP-TTLS
- Obtain user account state information (active / suspended)
- Obtain user group memberships to leverage them in Auth Policies
- Management user authentication for Admin Auth (using PAP)
- Authenticate a User by performing delegated authentication checking username and password via OAuth/ROPC method
- Obtain user group memberships to leverage them in Auth Policies
- Obtain user account state information (active / suspended)
Entra ID Portal
Login to your Azure tenant at portal.azure.com
Navigate to Azure Active Directory > App Registrations:
Click on New Registration:
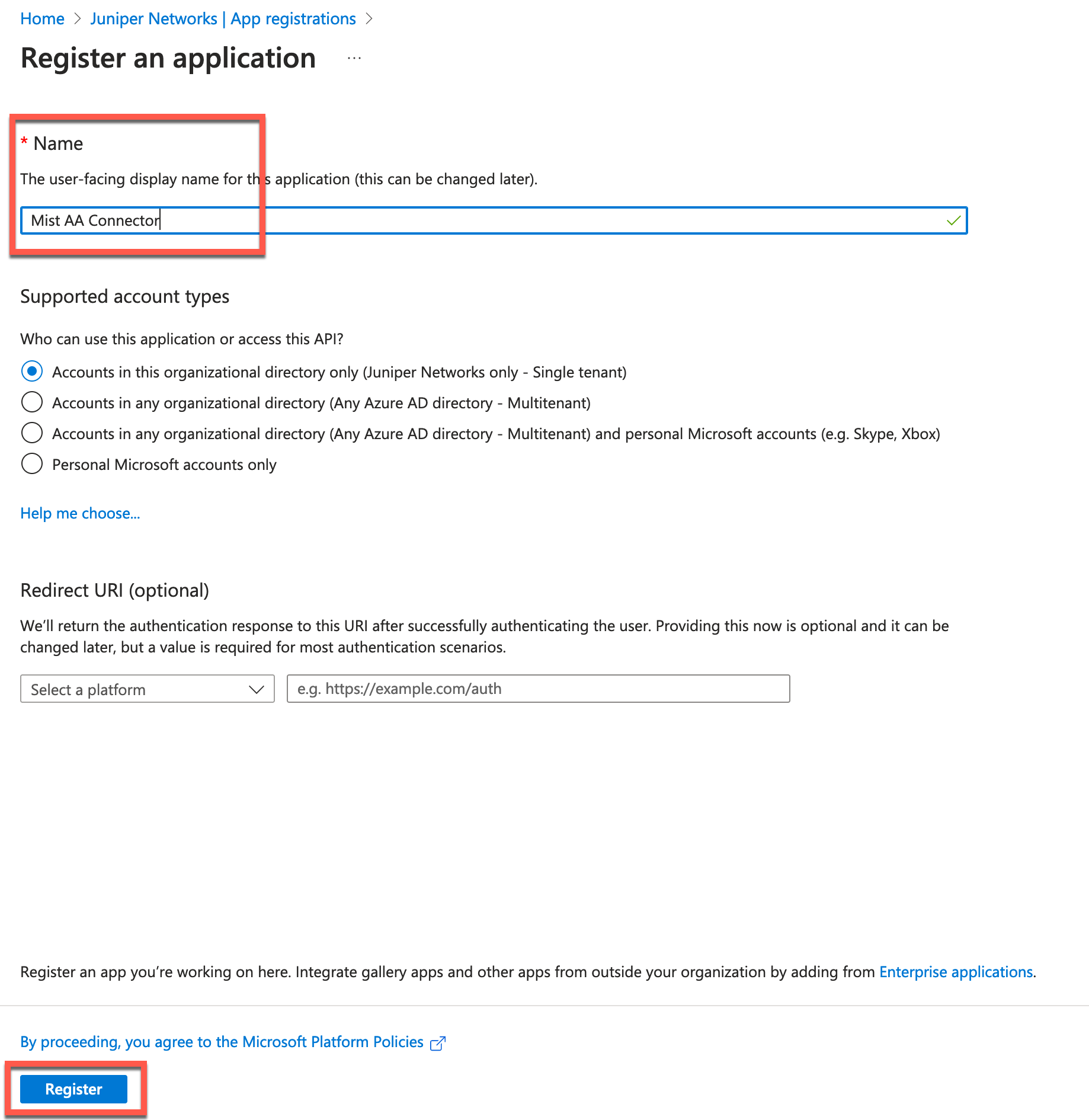
Give your application a name, then click Register:
Copy and save Application (client) ID, Directory (tenant) ID, then click on Add a certificate or secret:
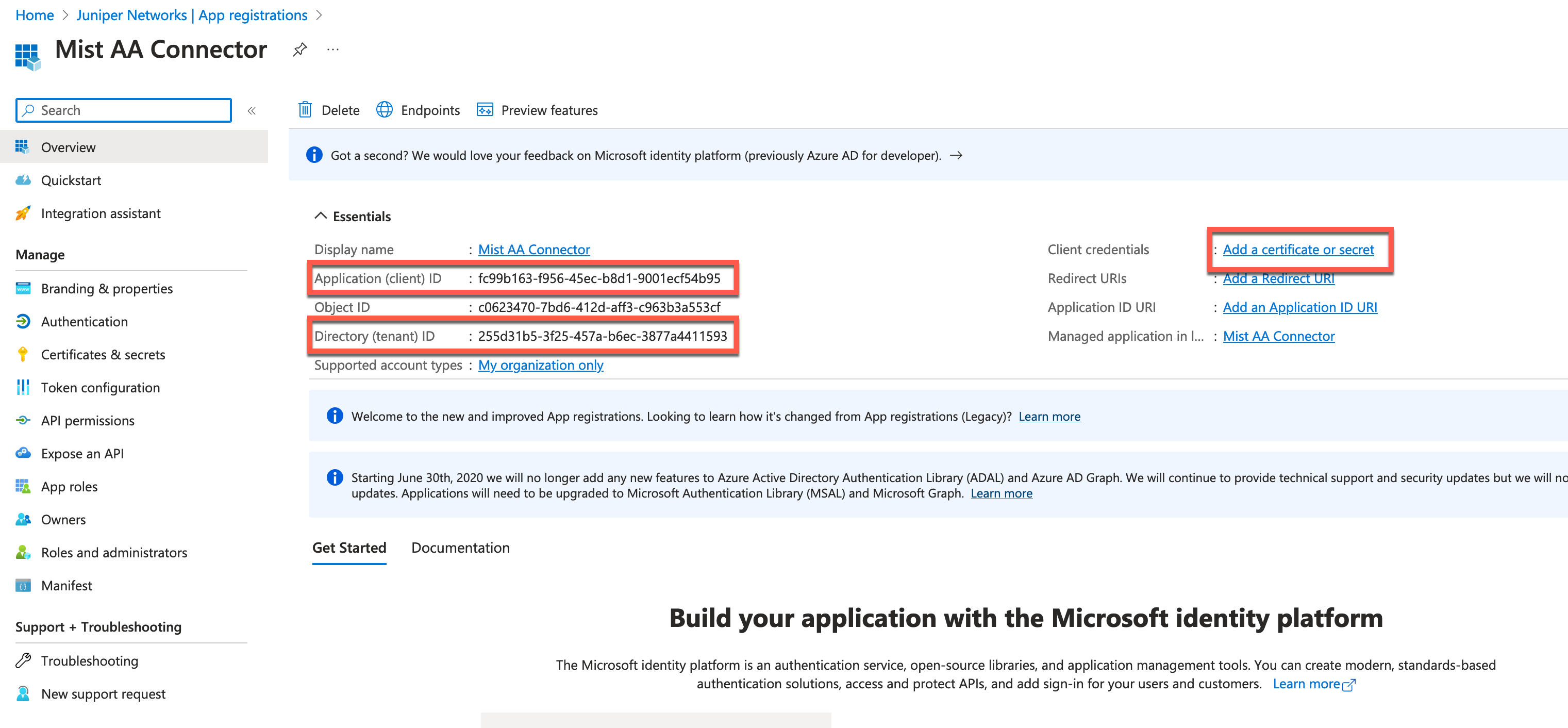
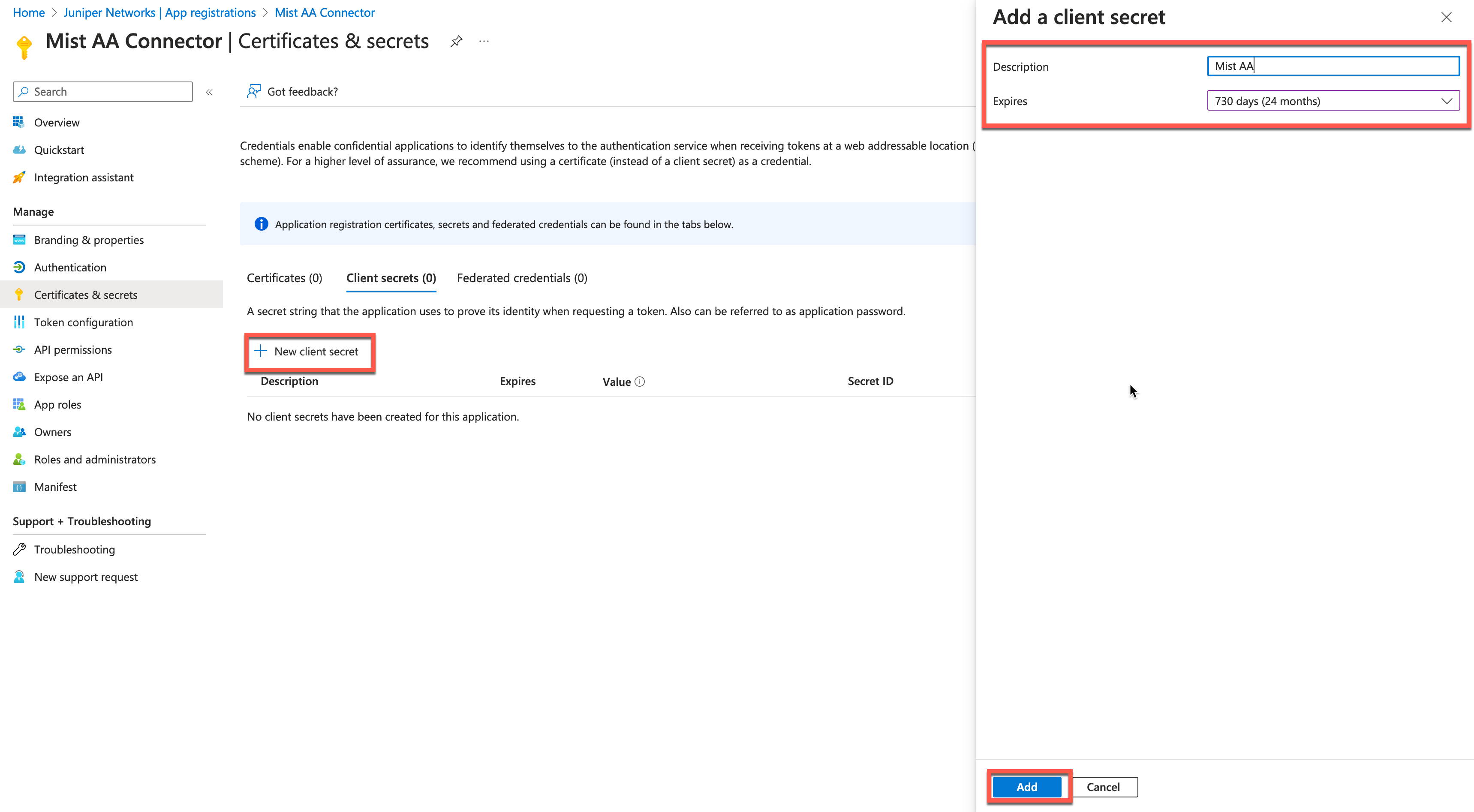
Click on New Client Secret, set the secret expiration, then click Add:
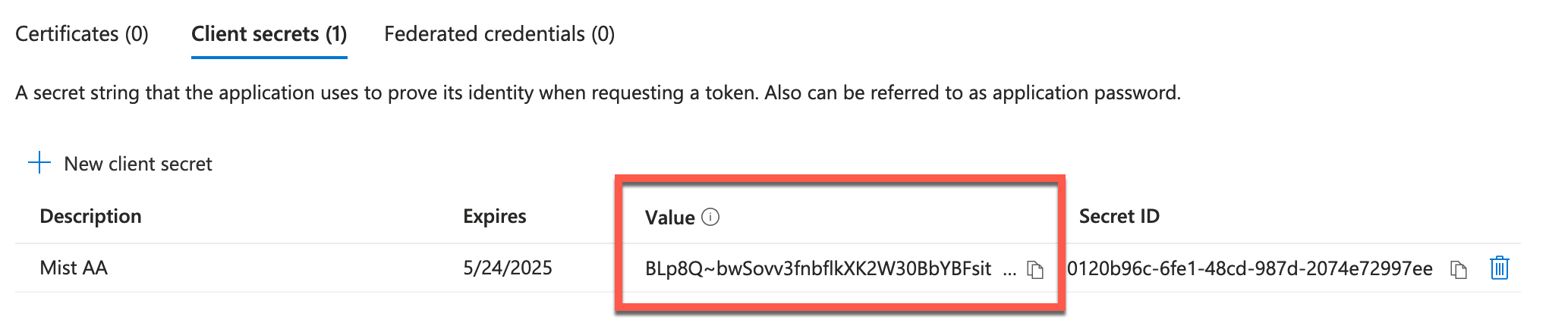
Once secret is added, copy and save the Value field (note you will only see it once right after secret is created, so make sure to save it in the safe place):
Now, navigate to Authentication tab and allow public client flows, this is required if you want to support EAP-TTLS / credential based authentication:

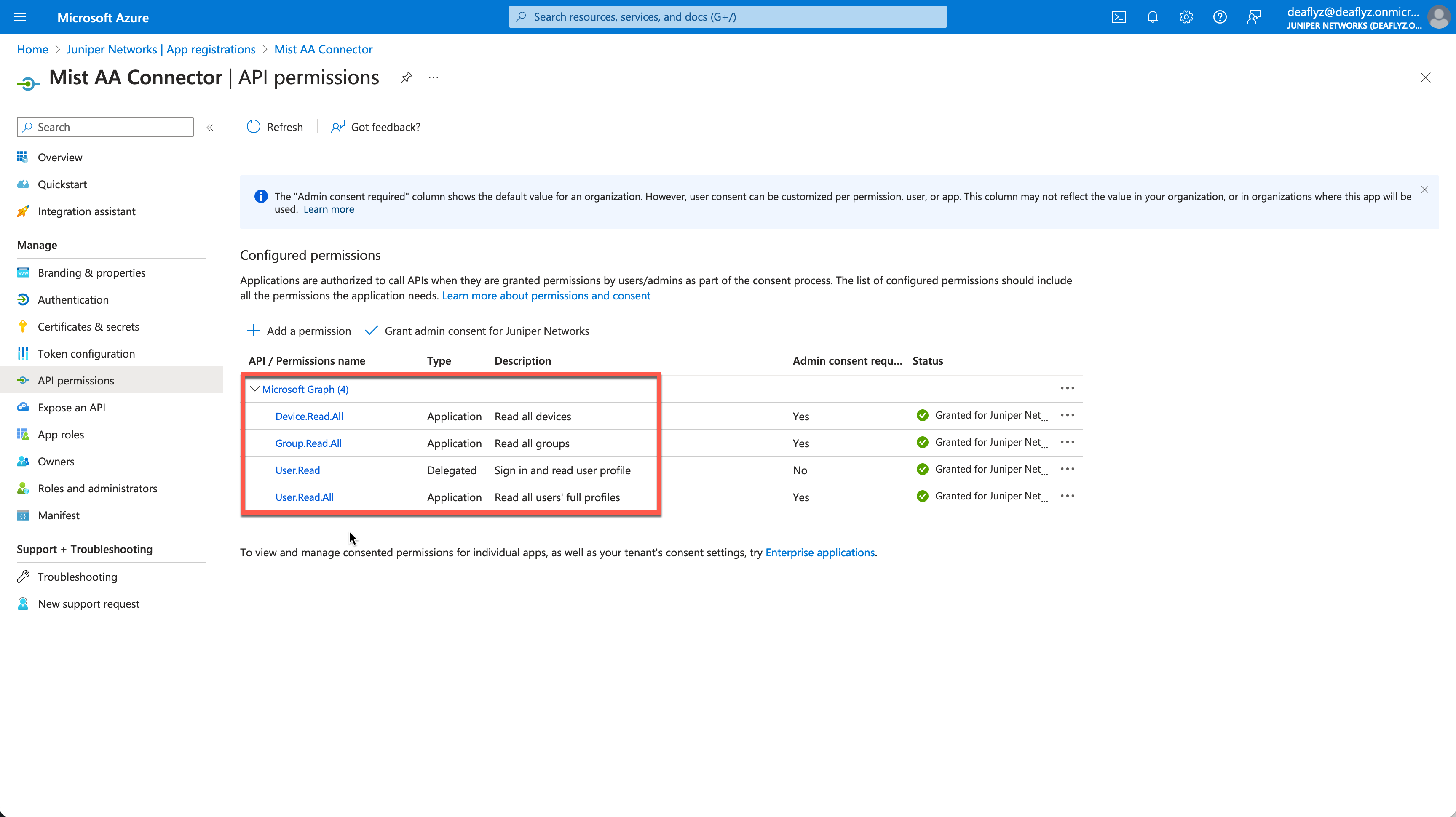
Lastly, navigate to API Permissions tab and grant the following permissions, and do not forget to grant admin consent:
Microsoft Graph:
User.Read – Delegated
User.Read.All – Application
Group.Read.All – Application
Device.Read.All – Application
Mist Dashboard
Navigate to Organization > Access > Identity Providers and click Add IDP:
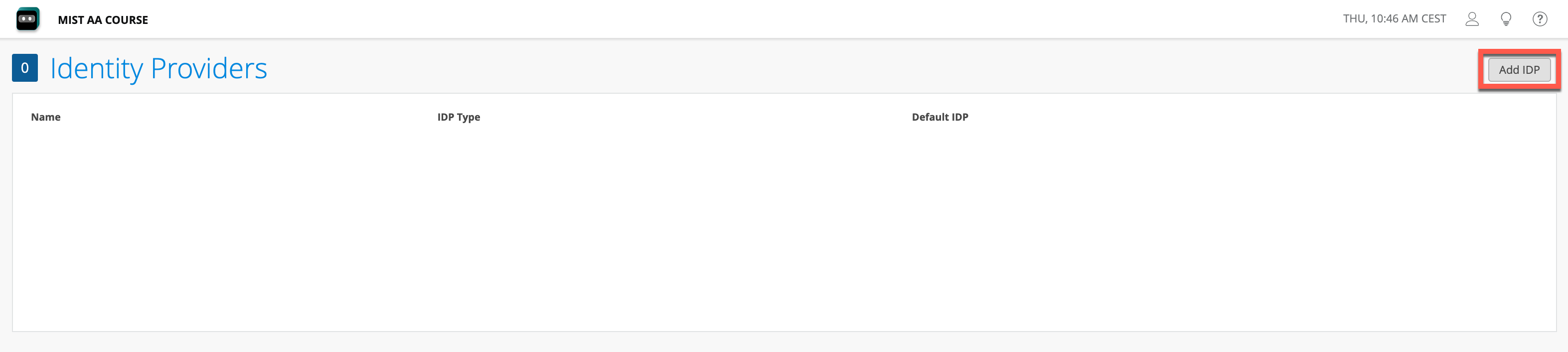
Configure Azure AD integration as follows:
IDP Type: OAuth
OAuth Type: Azure
OAuth Tenant ID: paste value from Directory (tenant) ID you copied from Azure app
Domain Names: configure your Azure domain name(s)
OAuth Client Credential (CC) Client Id: paste Application (client) ID you copied from Azure app earlier
OAuth Client Credential (CC) Client Secret: paste Value of the secret your created earlier
OAuth ROPC Client Id: paste Application (client) ID from Azure
Note: in case it is required to get machine group memberships, please enable “Default IDP” checkbox.
Notes on “EAP-TTLS” and “Admin Auth” Authentication with Azure
EAP-TTLS as well as Admin Auth authentication leverages ROPC (Resource Owner Password Credential) OAuth flow with Azure AD, which means using legacy authentication using Username + Password without MFA. Few considerations regarding using this method:
- Client devices need to be configured with the right WiFi profile, either from GPO or MDM – simply providing username/password at the login prompt will not work for some operating systems.
- Users need to use full UPN (username@domain) username format, not just username.
- Clients need to trust server certificate, please refer to the following doc for more details.
- Users need to log in at least once to azure before ROPC authentication will work (this note is important if using test user accounts).
- Azure needs to hold the password for the user, i.e. either full cloud accounts are supported, or local AD users where Password Syncronization is enabled with Azure AD Connect. Federated Authentication users are not supported.
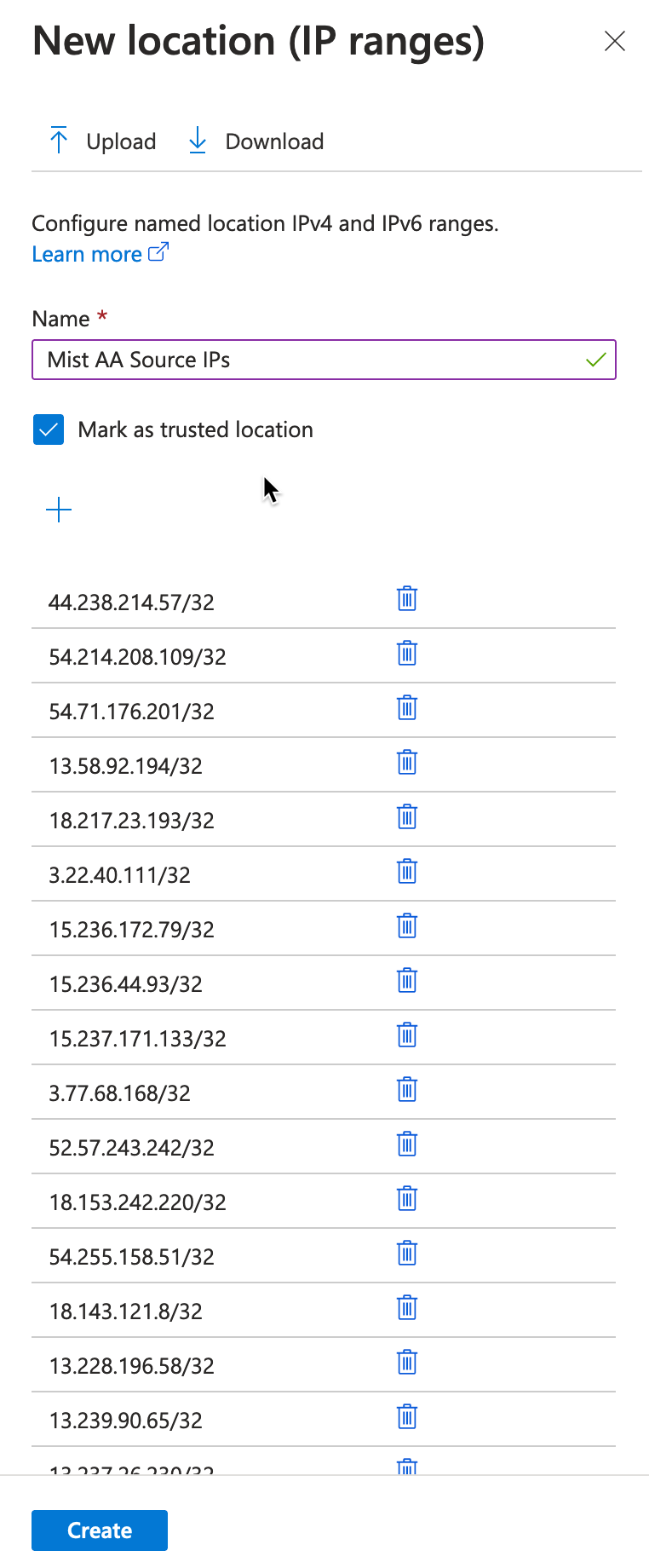
- MFA needs to be disabled for users using this specific application, as MFA is not a real option for 802.1X (breaks roaming, and client timeouts). One way to achieve MFA bypass for EAP-TTLS is to mark Mist Access Assurance Source IPs as trusted locations. For example:
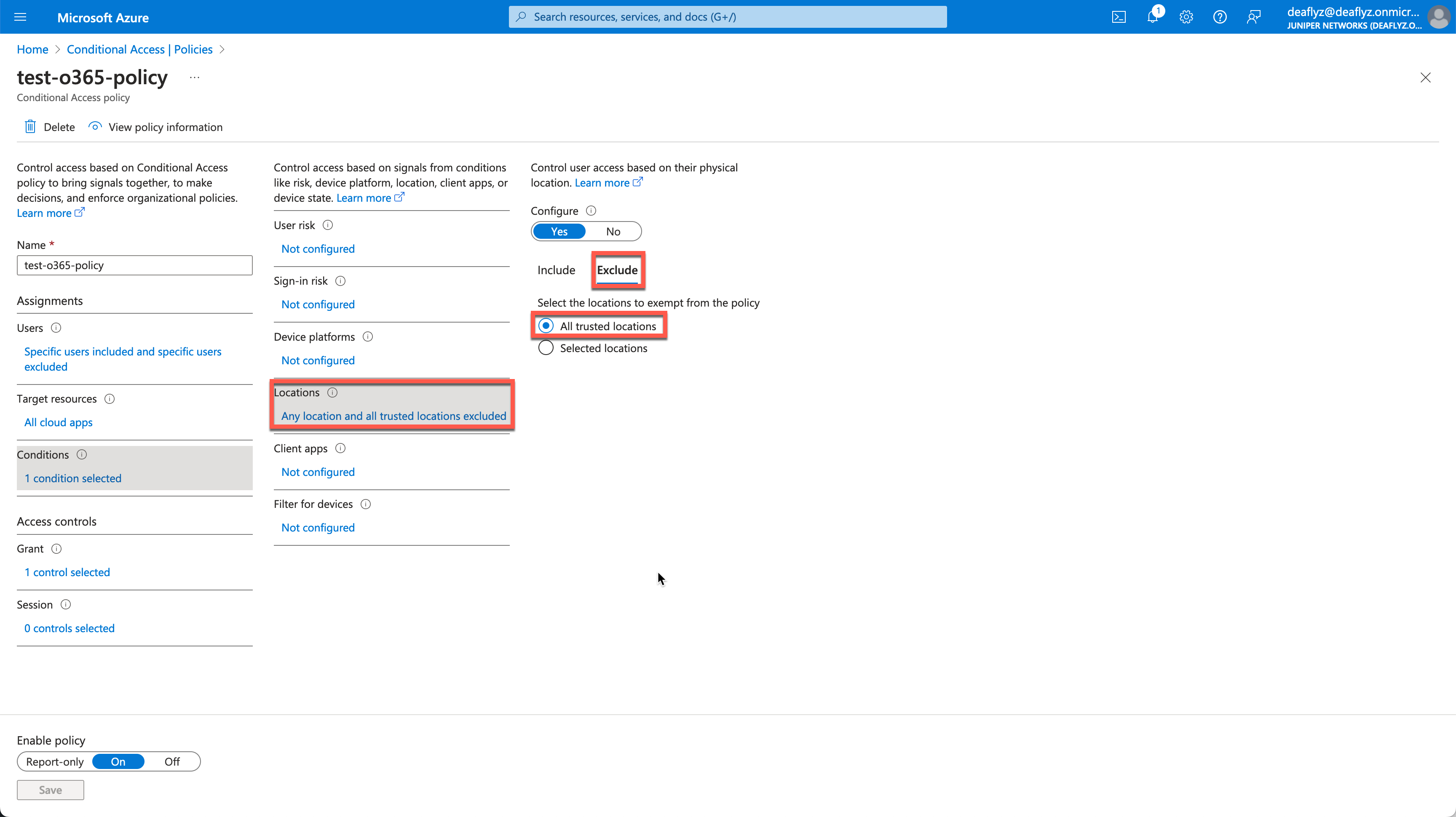
Then reference trusted IP sources as exclusion criteria for your MFA enforcement Conditional Access rule:
Validation
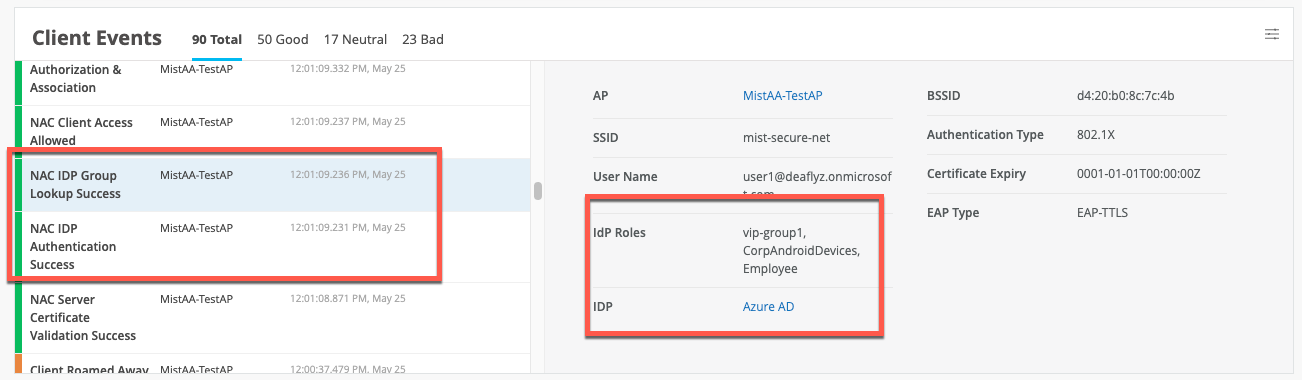
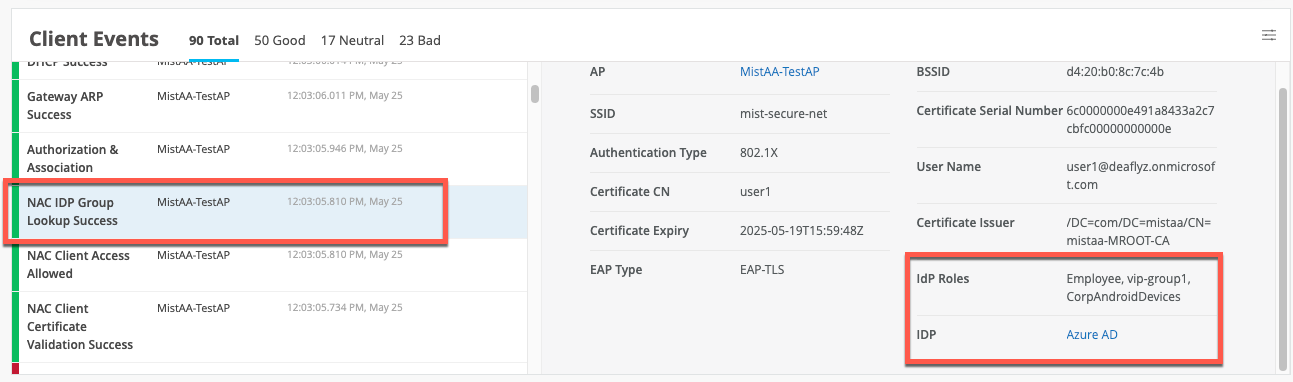
When clients are authenticated using EAP-TLS with Azure AD lookup, you should see an additional event called IDP Group Lookup Success:
In EAP-TTLS scenario, you should see NAC IDP Authentication Success (indicating Azure validated user credentials), followed by NAC IDP Group Lookup Success event that fetches user group memberships: