We at Mist are constantly working on making the Mist experience the best possible experience. So every week you will see new and updated Cloud Features. Here are the updates for July 20, 2017.
Honeypot AP detection and Rogue AP updates (Beta access only)
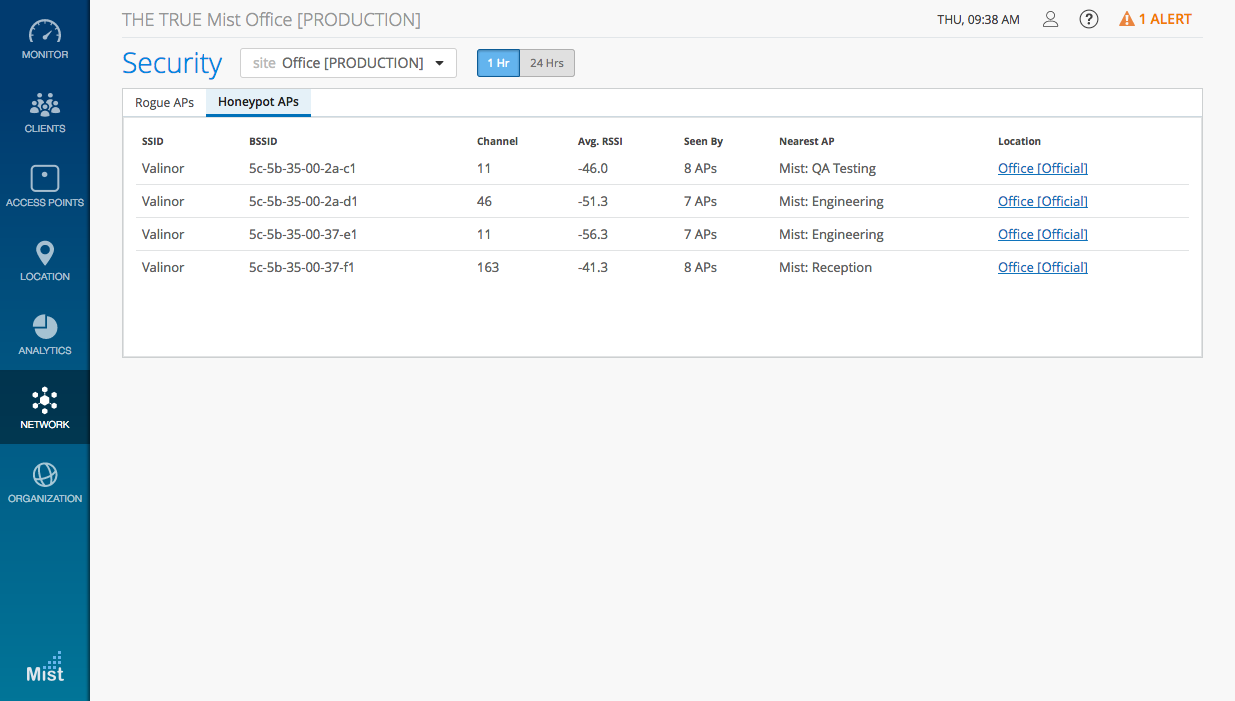
Honeypot APs are unauthorized APs advertising your SSID. They pose a security risk and may open up your network to vulnerabilities and external attacks. Mist extends its cloud security capability for organizations by introducing Honeypot AP detection to prevent such threats to your network. Detection of Honeypot APs is enabled by default under Site Settings.
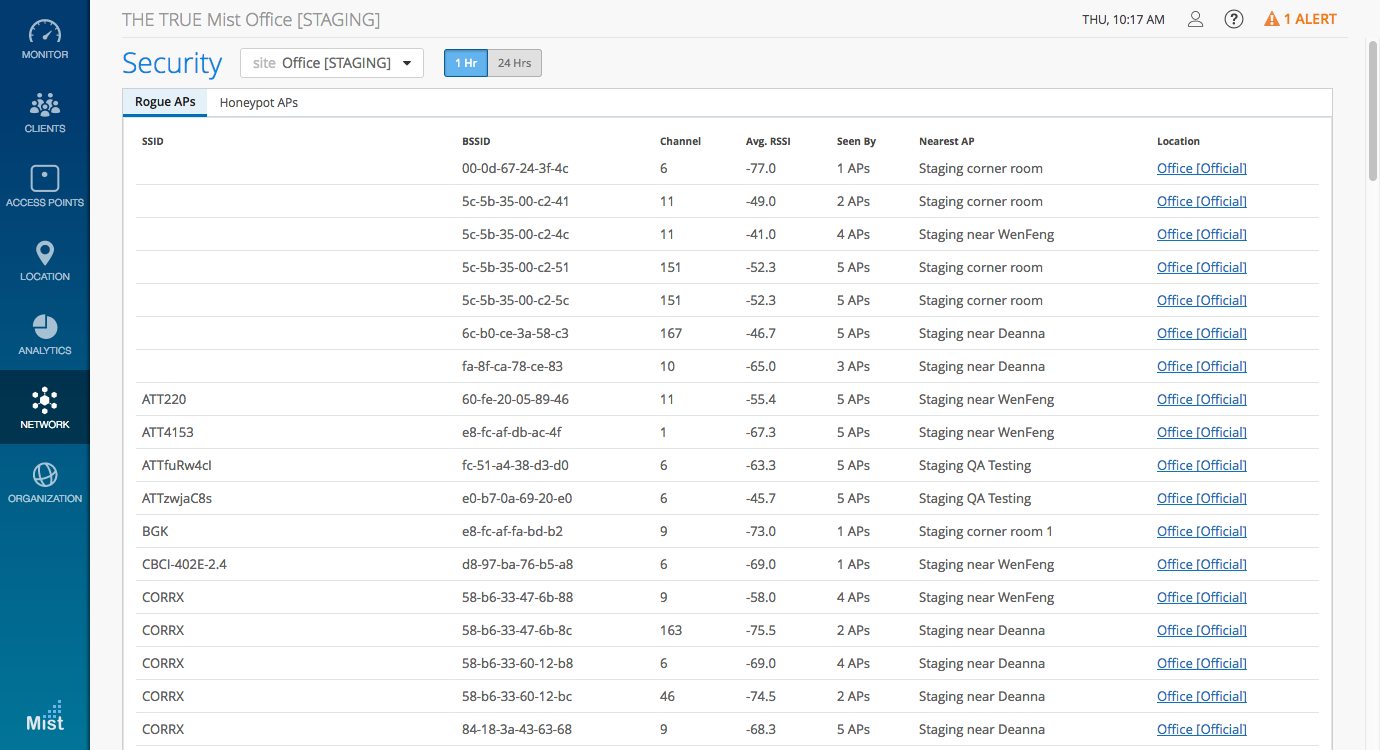
Previously, any unknown AP heard by the Mist AP would be classified as a Rogue AP. We have optimized this detection so that you can now set an RSSI threshold as a criteria for detecting actual rogues in proximity of your network, vs neighboring APs, or any APs that can be scanned in the air.
The Rogue AP detection is disabled by default (previous behavior was always on). Please go to Organization -> Site Configuration to enable it and enter an RSSI value. The default RSSI is -80dBm – you may set the RSSI Threshold for Rogue AP detection between -40dBm to -100dBm.
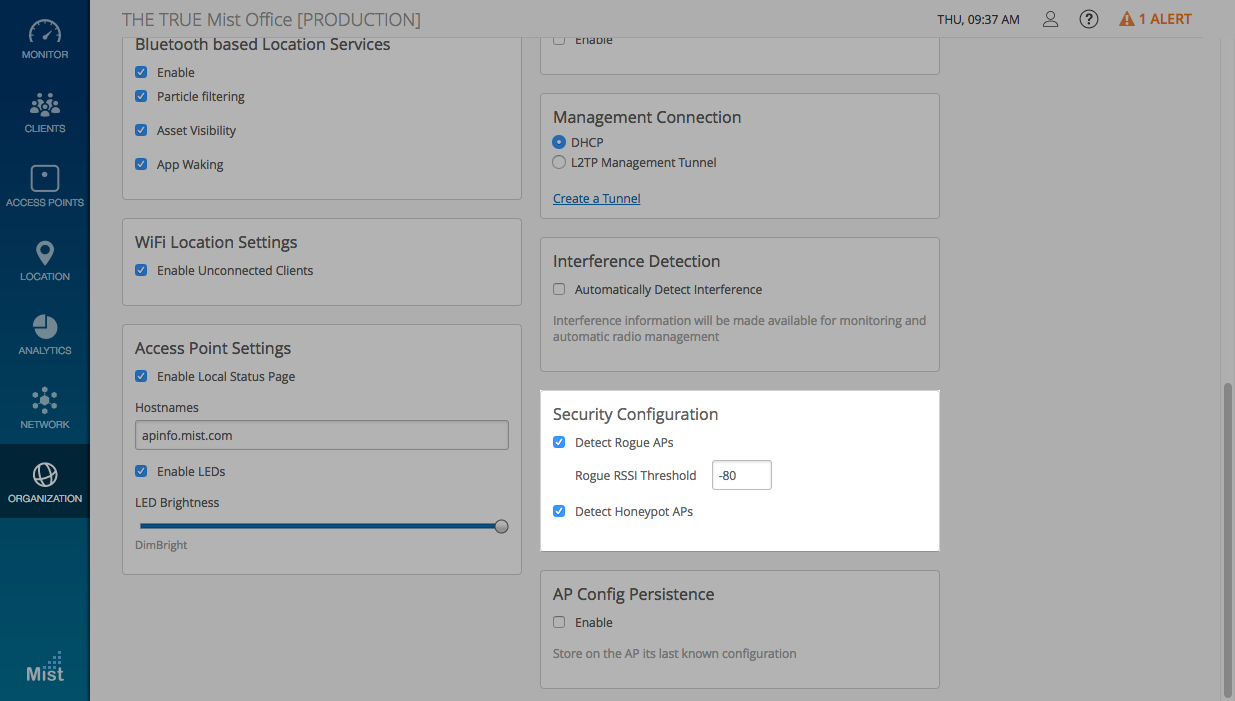
To view the list of Honeypot APs and Rogues APs, go to Network -> Security and select the tab you wish to view.
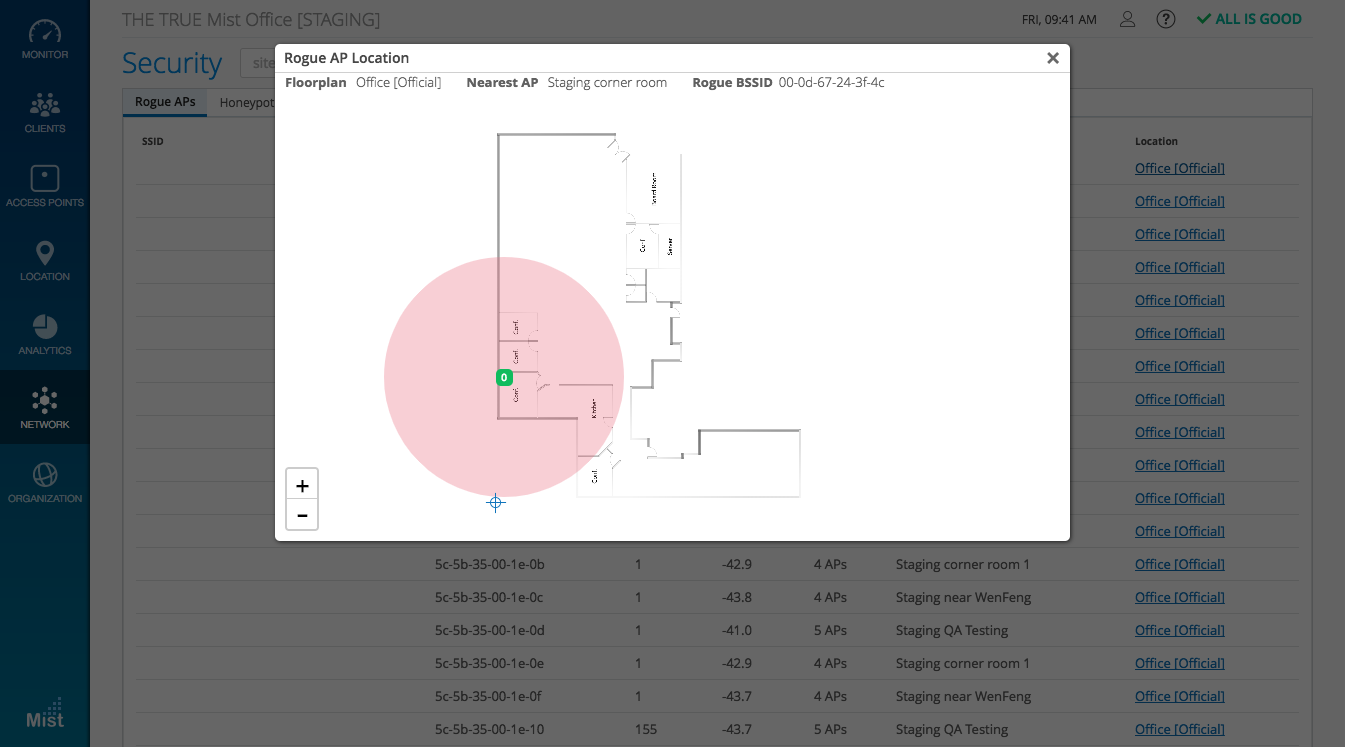
Selecting the Location link brings up your site map. Here, you can see the approximate location of the Rogue and Honeypot APs based on their Avg. RSSI values as seen by a specific AP on your site. Here, the map shows us there is a Rogue AP within the red circle surrounding the “Staging corner room” AP.
Guest authorization for External Portal
Guest authorization has been an essential feature in our Mist captive portal login to restrict network access to a list of predefined individuals. Starting this week, we are extending the guest authorization feature for external portal use as well. Once you are finished creating a guest WLAN forwarded to an external portal, the Edit Guest Authorization link will appear where you can specify the MAC addresses of pre-authorized guests.
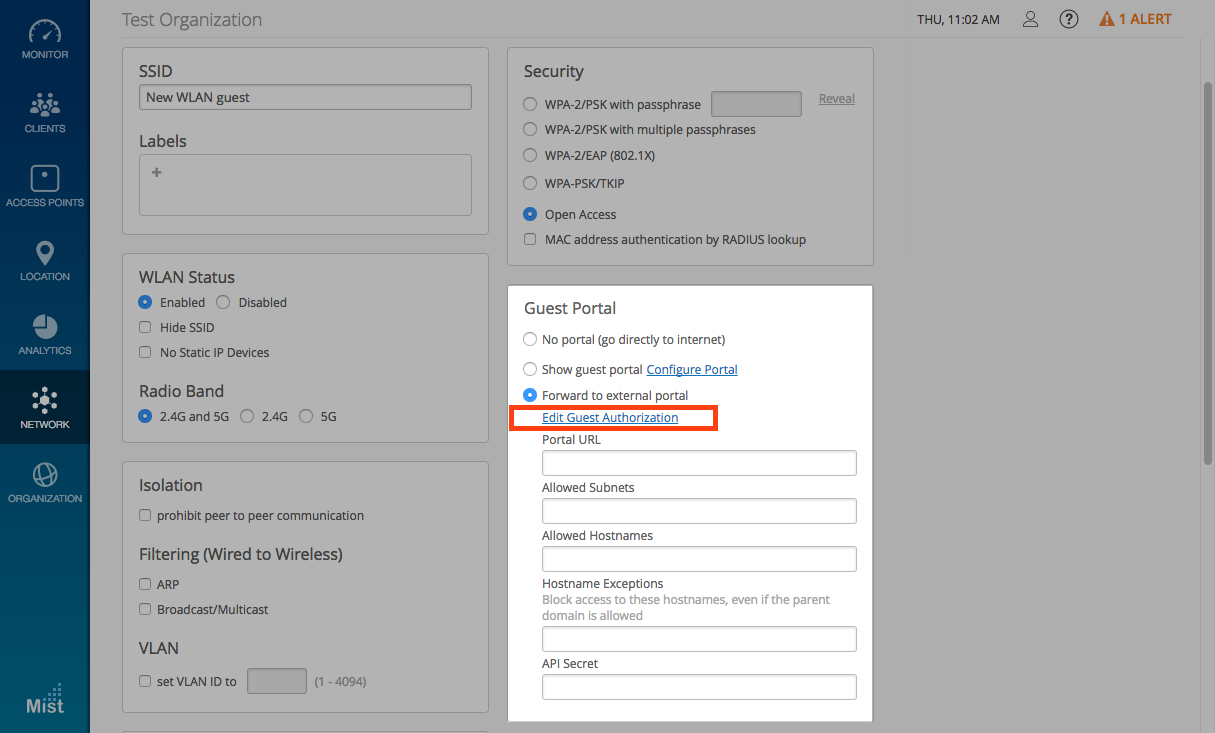
For more information on how to set up a Guest portal, please visit the link below:
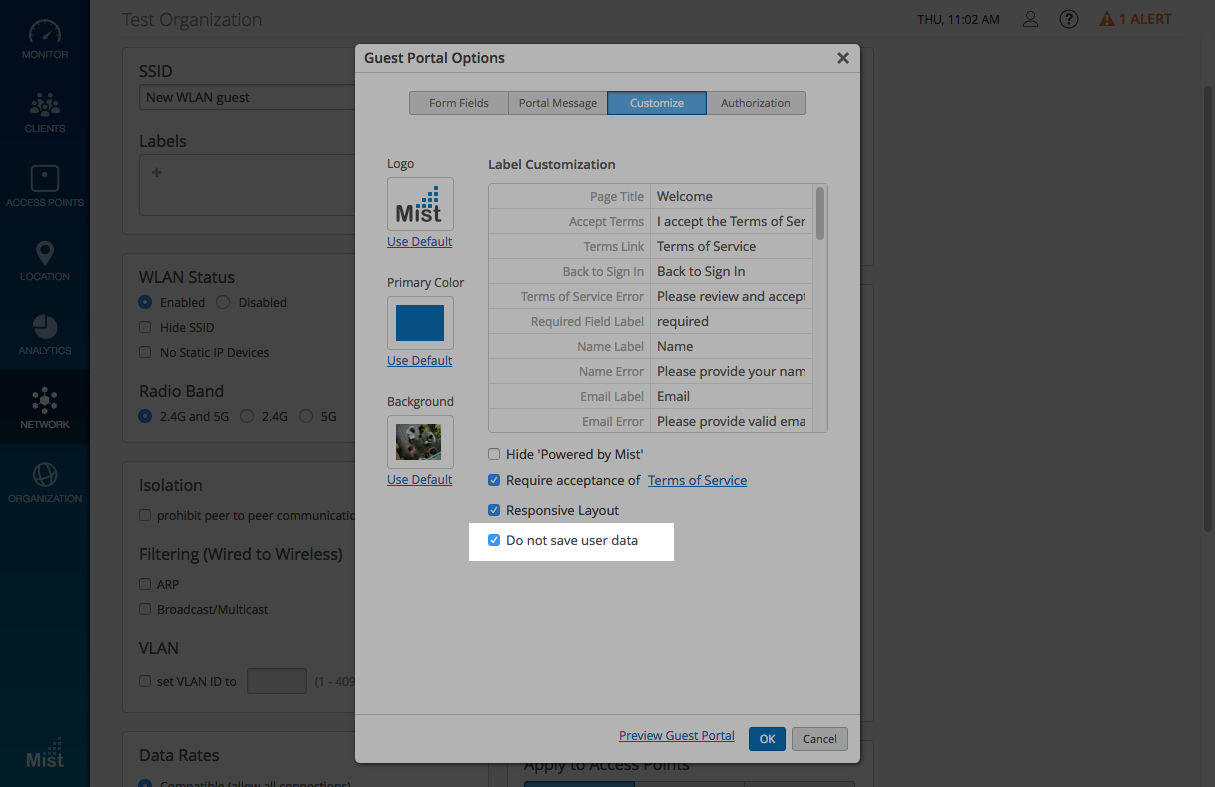
Social Login – don’t store customer data
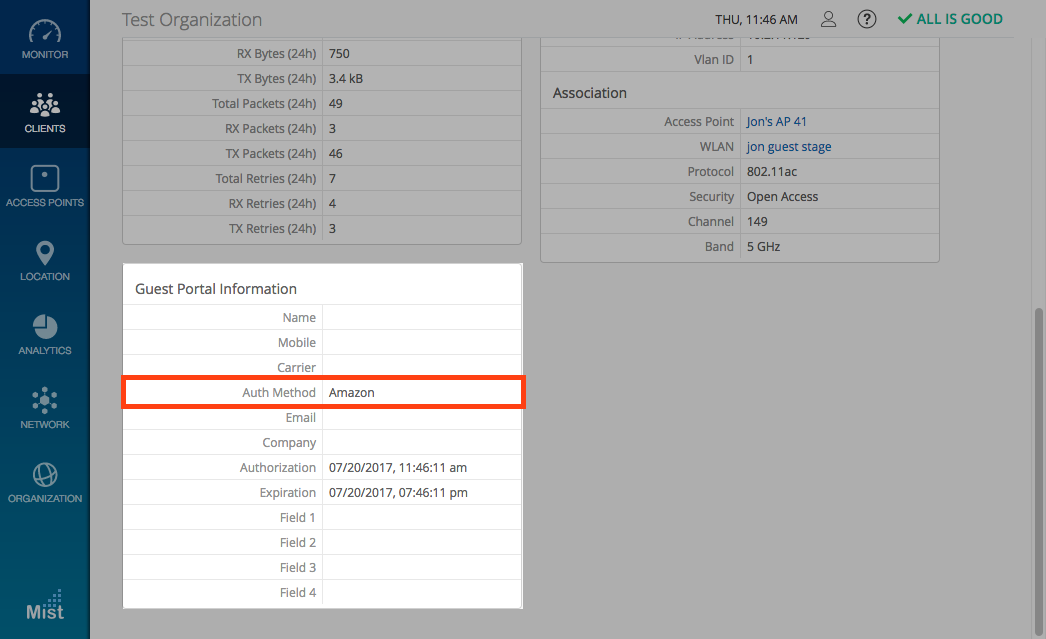
Mist respects the privacy concerns any customers may have regarding their personal details when signing into a guest network using social login. We have added a Do not save user data option when configuring a guest portal. Enabling this feature prevents any of the entered customer information from being stored or displayed on our system. Under the Client Details view, the only visible field will be Authentication Method, ensuring the anonymity of all personal information.
Enable the Do not save user data feature under the Customize tab when creating a guest portal WLAN.
Under Clients -> WiFi Clients, only the Authentication Method will be displayed. No data is stored or displayed in the rest of the fields.
If you would like access to beta features, please contact support@mist.com and we can help grant you access.