Juniper Mist on US GovCloud addresses specific regulatory and compliance requirements of US government agencies at the federal, state, and local level; contractors; educational institutions; and other US customers that run sensitive workloads in the cloud. Currently, this environment is “In-process” on the FedRAMP marketplace for Impact level “Moderate”.
This page lists the Juniper Mist updates released on US GovCloud on February 5, 2024.
Wired Assurance
Pod configuration in site-level campus fabric topologies
We have improved the scalability of site-level campus fabric topologies with the support of pods. You can configure pods from the Nodes tab of the campus fabric page. Pods allow you to group your access and distribution devices in a campus fabric topology. A pod could represent a building. For example, you can create a pod for each of the buildings in your site and create connections between the access and the distribution devices in that pod. You do not have to connect the same set of access devices to the distribution devices across multiple buildings.
Pod configuration is available for the following topology types:
-
Campus Fabric Core-Distribution
-
Campus Fabric IP Clos
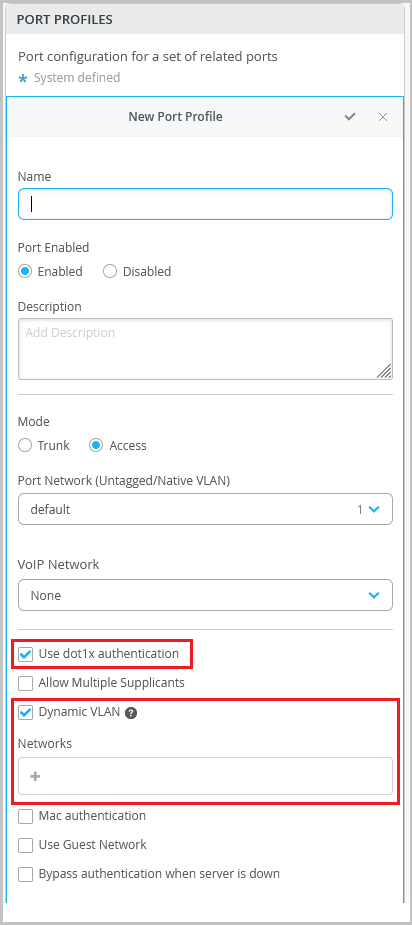
Dynamic VLAN assignment on ports with 802.1X authentication
Switch ports configured with 802.1X authentication support dynamic VLAN assignment.
During authentication, the RADIUS server may return a VLAN attribute (Tunnel-Private-Group-ID or Egress-VLAN-Name) in the RADIUS access-accept message. This attribute is then mapped to the VLANs configured on the switch port to perform dynamic VLAN assignment. To enable a port to perform dynamic VLAN assignment, you can configure these VLANs (which will be returned by the radius server) using the port profile. This is an optional configuration. For an IP Clos topology, you must fill the dynamic VLAN field so that the corresponding VLAN definitions are pushed to the switch.
To configure the dynamically returned VLAN:
-
Navigate to the Port Profile configuration section on the switch template or switch details page (Organization > Switch Templates > Template Name or Switches > Switch Name).
-
Select the Dynamic VLAN check box.
-
From the Networks drop-down list, select the VLANs that you want to include in the VLAN pool.
-
After saving the port profile, assign it to the switch port on which you want to configure the dynamic VLAN assignment feature.
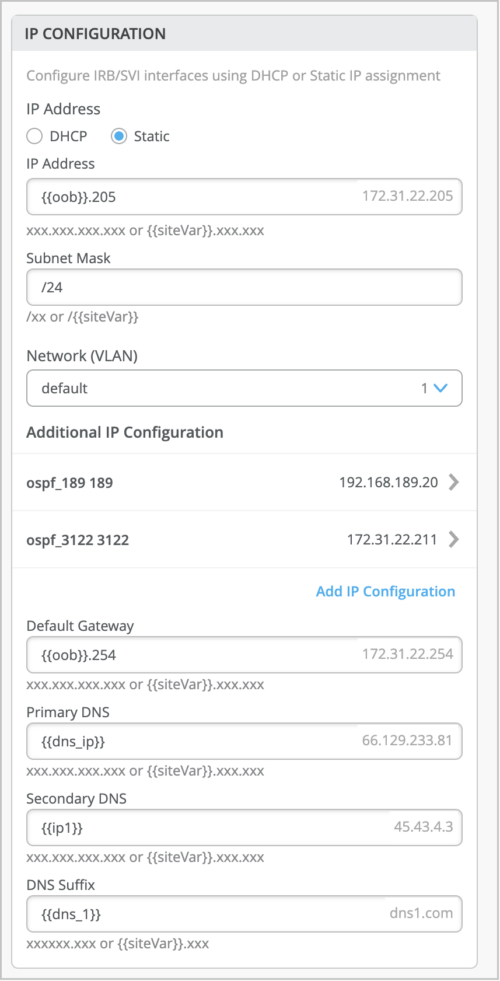
Support for configuring IP settings and static route as site variables
Mist supports configuration of static route and IP settings as site variables at the device level, site level, and organization level. Site variables help you address use cases that require you to configure a set of unique fields for different sites. Site variables provide a way to use tags to represent real values so that the value can vary according to the context where you use the variable. This means the same variable can configure different values in different sites.
Under IP Configuration, you can configure IP Address, Subnet Mask, Default Gateway, Primary DNS, Secondary DNS, and DNS Suffix as site variables.
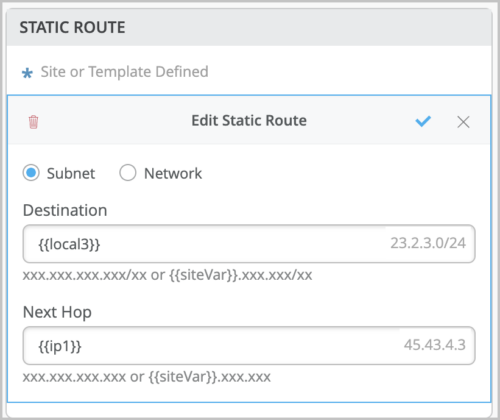
Similarly, in the static route configuration section, you can configure the Destination and Next Hop fields with site variables.
Site variables are now available for the following fields at the device level (switch details), site level (switch template), and organization level (switch template):
- DNS servers and DNS suffix
- NTP
- Radius servers
- Static route
- Networks (VLAN ID, subnet, or subnet mask)
- IP Configuration (including Additional IP configuration): Default Gateway, Primary DNS, Secondary DNS, and DNS Suffix.
- IP Configuration (OOB)
IP Clos deployments with dedicated border nodes can now function with one core switch
For IP Clos campus fabric deployments that use dedicated switches (border nodes) to run the service block functionality, we have reduced the minimum number of core switches required from two to one switch.
This change does not apply to the deployments where the core switches are configured to carry out the service block functionality as well.
In a campus fabric topology, border nodes connect to external devices such as firewalls, routers, or critical devices. External services or devices (for example, DHCP and RADIUS servers) connect to the campus fabric through border nodes.