Simplified Operations
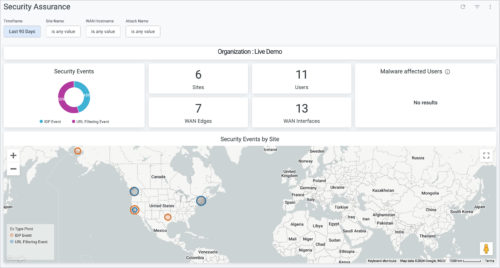
Custom forwarding tunnel information on the WLAN list page
For each tunneled WLAN (where Custom Forwarding is set to a tunnel), you can view the tunnel profile information in the Forwarding column on the WLAN list page (Site > WLANs). You do not have to open each WLAN page to see the tunnel profile mapped to that WLAN.
Marvis
API support for troubleshooting sites, devices, and clients
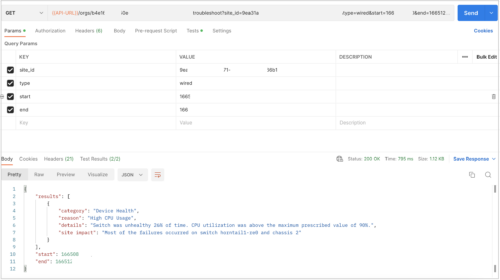
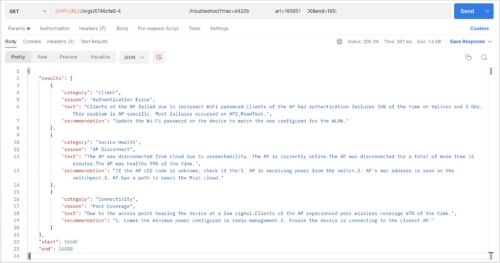
We have introduced Marvis APIs that provide you a way to query Marvis to troubleshoot sites and devices. The devices include wired and wireless clients, access points (APs), switches, and WAN Edge devices. The API query fetches a text-based response containing the problem category, reason, description, and recommendation (if applicable).
You can troubleshoot the devices by using the device MAC addresses, and the sites by using the site IDs and network types (optional). The network types include wireless (default), wired, and WAN.
To use this feature, you must have the following:
- Marvis subscription at the organization-level (see Subscriptions for Marvis).
- Organization-level access (to all sites).
The following image shows APIs for troubleshooting a site (wired network):
The following image shows APIs for troubleshooting devices or clients:
See the API documentation here: https://api.mist.com/api/v1/docs/Org#troubleshoot
Note: To access the above URL, you need to log in to the Global 01 environment. You can access the API documentation from the help (?) menu on the Mist portal (the organization UI).
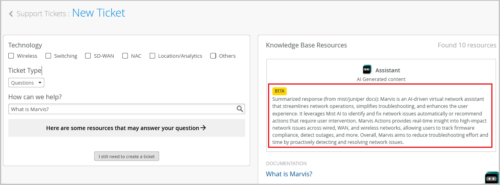
Instant, summarized response to your support questions
The Support Ticket page displays an instant, summarized response, in addition to the relevant documentation links, to your support questions. You can review this AI-generated response to see if it answers your question before opening any documentation pages. You can access the Support Ticket page from the help (?) menu.
Access Assurance
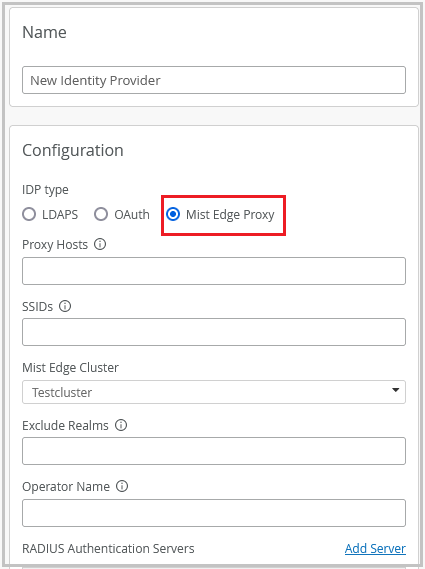
Mist Edge Proxy IDP
Juniper Mist Access Assurance provides an option to configure Mist Edge proxy-based identity providers (IDPs). A typical use case for this IDP is to use Mist Edge as a proxy into eduroam federation to authenticate:
- External visitors
- Home roaming users (the users who are traveling to a different institution and would like to be authenticated to eduroam SSID by using their home institution credentials).
In this setup, one or more Mist Edges function as gateways into eduroam with a static public IP address.
To configure a Mist Edge Proxy IDP, navigate to the identity provider configuration page (Organization > Identity Providers > Add IDP), select Mist Edge Proxy as the IDP Type, and specify the required information.
For more information, see Mist Edge Proxy IdP – eduroam.
Wired Assurance
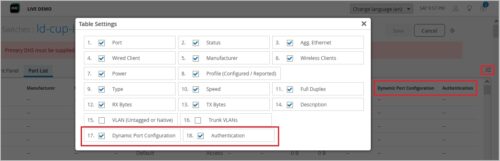
Port List displays authentication method and dynamic port configuration status
We have added the following columns to the Port List tab on the switch details page (Switches > Switch Name):
- Dynamic Port Configuration: Shows the dynamic port configuration status to help you determine if a switch port is enabled with a dynamic port profile. Dynamic port profiles enable you to configure rules for dynamically assigning port profiles to an interface.
- Authentication: Shows the authentication method configured on the switch port for access control. This column could display values such as Dot1x, Dot1x/MAB, and MAB.
You can also view the dynamic port configuration status and the authentication information on the port window that appears when you hover over a port on the Front Panel tab.
If you do not see these columns on the port list, click the hamburger menu on the right and then select the check boxes representing these columns to display them.
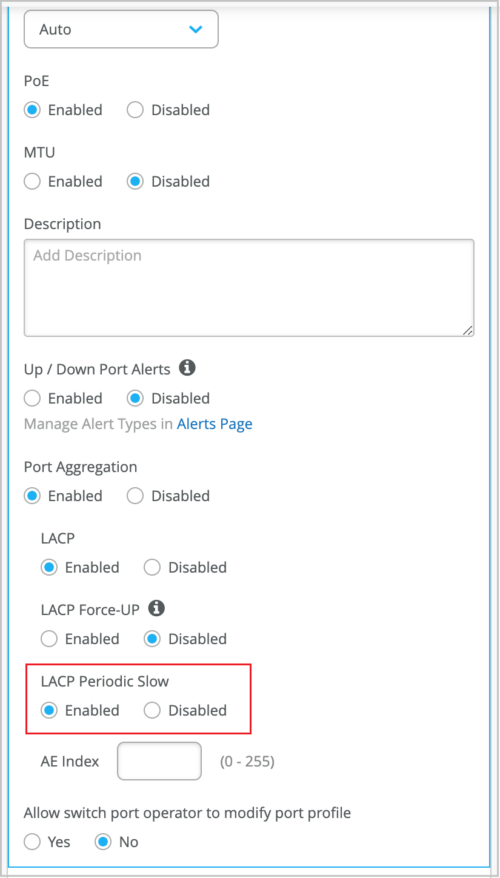
Support for configuring slow interval for LACP packet transmission
For aggregated Ethernet (AE) interfaces, you can set the slow interval (LACP Periodic Slow) for periodic transmission of LACP packets. If you configure the LACP Periodic Slow option on an AE interface, the LACP packets are transmitted every 30 seconds. By default, the interval is set to fast in which the packets are transmitted every second. You can enable the slow interval from the Port Config tab in the Select Switches Configuration section of the switch template (at the organization level or site level) or from the Port Configuration section on the device-level switch configuration page (Switches > Switch Name). The option to configure the LACP Periodic Slow interval is available only if you enable LACP on the port.
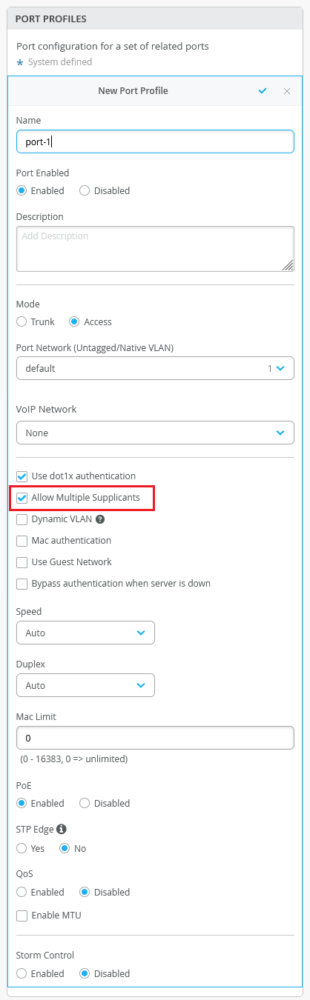
Support for dot1x authentication in multiple supplicant mode
You can configure a switch port with dot1x authentication in multiple supplicant mode. In this mode, multiple end-devices can connect to the port. And each end-device is authenticated individually. To configure multiple supplicant mode, select the Allow Multiple Supplicant check box on the port profile in the switch template (at the organization level or site level) or in the device-level switch configuration page (Switches > Switch Name). This option is available only if you select the ‘Use dot1x authentication’ option. For this configuration to take effect, you must assign the port profile to a switch port.
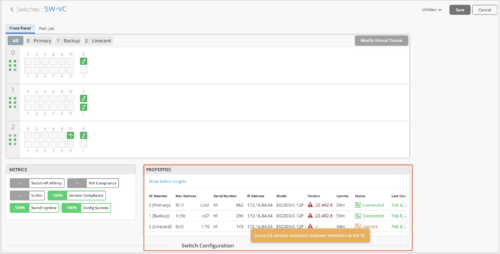
Software version mismatch warning for Virtual Chassis member switches
The switch details page (Switches > Switch Name) for a Virtual Chassis shows a warning message for each member switch running a software version that is different from the software version on the other members in the Virtual Chassis. In case of a version mismatch, the Version column in the Properties section of the switch details page displays a warning icon. To view the warning message, hover over the warning icon. The status of the members with a software version mismatch is shown as inactive.
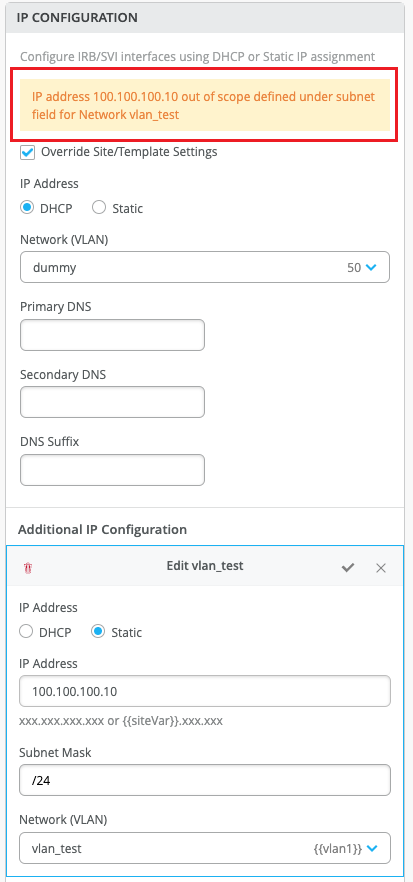
Warning when additional IP address falls outside the network range associated
If the IP address specified in the Additional IP Configuration section under IP Configuration on a switch details page (Switches > Switch Name) does not fall within the scope of the subnet configured in the associated network (VLAN), the IP Configuration window displays a warning message to indicate the mismatch.
WAN Assurance
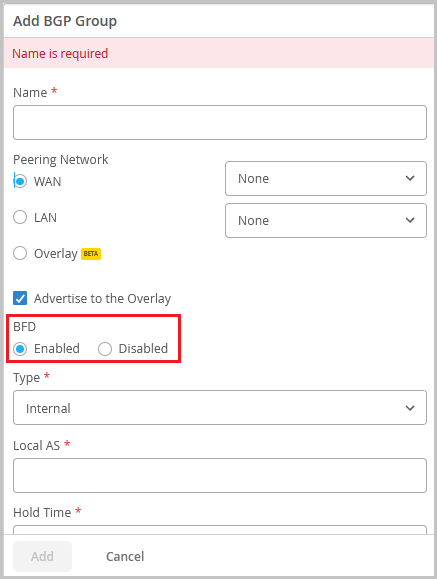
BFD configuration support for BGP sessions
You can enable or disable Bidirectional Forwarding Detection (BFD) for the BGP sessions on WAN Edge devices.
The BFD protocol is a simple hello mechanism that detects failures in a network. Hello packets are sent at a specified, regular interval. A neighbor failure is detected when the routing device stops receiving a reply after a specified interval. The failure detection timers for BFD have shorter time limits than default failure detection mechanisms for BGP, so they provide faster detection.
You can enable or disable BFD from the Add BGP Group section on the WAN Edge template (Organization > WAN Edge Templates) or from the WAN Edge configuration page (WAN Edges > WAN Edges > WAN Edge Name).
Support for disabling BGP neighbors
If you want to disable BGP neighbors on your WAN Edges for any reason, you can do so from the WAN Edge template (Organization > WAN Edge Templates) or from the WAN Edge configuration page (WAN Edges > WAN Edges > WAN Edge Name). To administratively disable a BGP neighbor, select the Disabled check box in the Edit Neighbor section on the Add or Edit BGP Group page.
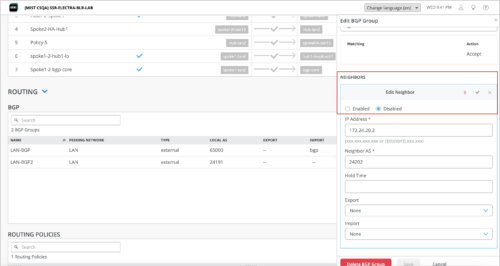
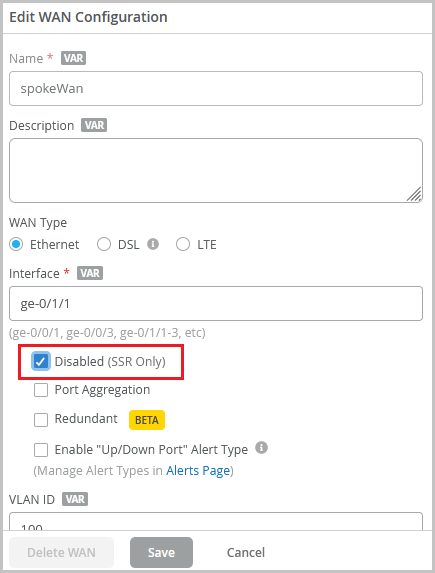
Support for disabling WAN Edge ports (SSR)
If you want to disable a LAN port or WAN port on an SSR Series device for any reason, you can do so from the WAN Edge template (Organization > WAN Edge Templates) or from the WAN Edge configuration page (WAN Edges > WAN Edges > WAN Edge Name). To administratively disable an SSR device port, select the Disabled check box under the specified interface on the LAN or WAN configuration page.
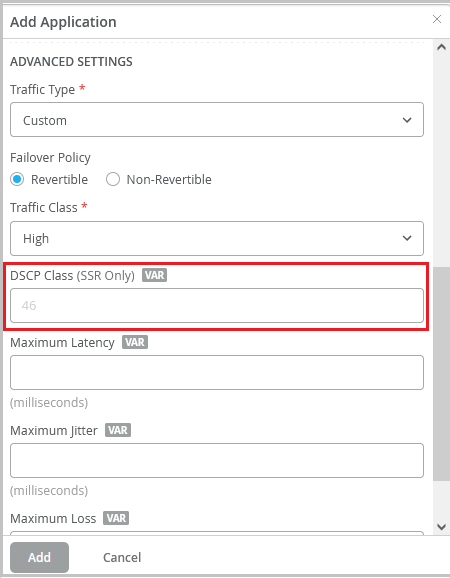
Support for configuring custom DSCP values (SSR)
We have simplified the configuration of Differentiated Services Code Point (DSCP) values for SSR Series devices. You can now specify custom DSCP Class values (ranging from 0 to 63) per traffic type for each application. Previously you had to choose from a set of pre-built values (statically mapped to each traffic type) from the DSCP Class drop-down list.
DSCP helps you classify and manage network traffic to provide quality of service (QoS) in modern Layer 3 IP networks. It uses the 6-bit Differentiated Services (DS) field in the IP header to classify packets.
You can configure DSCP Class values from the Add Application page. When you select a traffic class (Best Effort, High, Medium, or Low), the applicable default DSCP Class value is displayed as a help text. You can choose to override it.
Support for SRX1600
Juniper Mist supports onboarding, management, and troubleshooting of the SRX1600 Firewall for the secure router use case. The SRX1600 is ideal for small-medium enterprise edge, campus edge, data center edge, and secure VPN router deployments for distributed enterprise use cases.
To onboard an SRX1600, use the Adopt WAN Edges workflow on the Inventory page (Organization > Inventory > WAN Edges). This device does not support the Claim WAN Edges workflow.
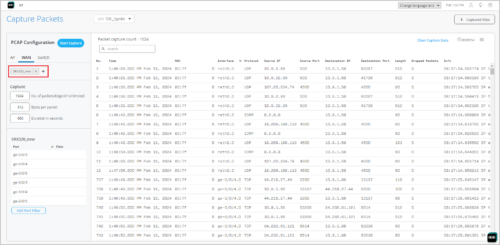
PCAP support for SRX
Mist provides packet capture (PCAP) support for troubleshooting SRX Series devices. On the Capture Packets page (Site > WAN Edge Packet Captures), you can select SRX devices from the WAN tab to initiate packet capture. The PCAP feature is already available for SSR Series devices. Packet capture is a tool that helps you to analyze network traffic and troubleshoot network problems. It captures real-time data packets traveling over the network for monitoring and logging.
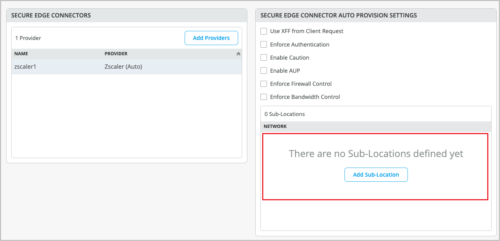
Security: Support for Zscaler sub-locations
Mist supports configuration and provisioning of Zscaler sub-locations. A Zscaler sub-location is a child entity of the location object. Locations identify the various networks from which your organization sends its internet traffic. Sub-locations can be used for specific uses cases. For example, an organization can define a Zscaler sub-location for its corporate network, and another sub-location for its guest network, even if their traffic goes through the same GRE or IPSec tunnel. The organization can then use these sub-locations to:
- Implement different policies based on IP addresses.
- Enforce authentication for the internal corporate network, while disabling it for the guest network.
- Enforce bandwidth control for sub-locations while ensuring that unused bandwidth remains available to the parent location.
For each sub-location, you can specify gateway options and an internal network.
You can configure Zscaler sub-locations from the WAN Edge template (Organization > WAN Edge Templates) or from the WAN Edge configuration page (WAN Edges > WAN Edges > WAN Edge Name). The Add Sub-Location option will be available only when you select Zscaler as the Secure Edge Connector.
Mist Edge
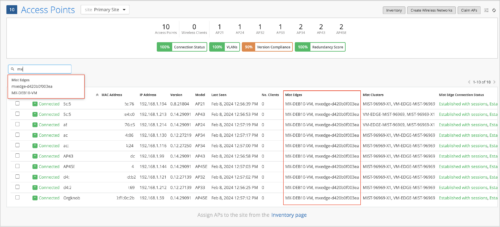
Search for APs by Mist Edge name
You can search for an access point (AP) by Mist Edge name, even if the AP has two or more tunnels to the Mist Edge. You can also sort the AP list by Mist Edge name. Previously, the AP page did not support search by Mist Edge names when there were multiple tunnels associated.
Network Observability and Business Intelligence
Security Assurance Dashboard
We have introduced Security Assurance Dashboard, a new WAN security dashboard powered by Premium Analytics. This dashboard provides crucial security insights derived from the ‘URL Filtering’ and ‘Intrusion Detection and Prevention System (IDS/IPS)’ events generated by the Juniper Session Smart Routers or SRX Firewalls with Advanced Security Pack. You can access this dashboard from the WAN section on the Premium Analytics page (Analytics > Premium Analytics).