EX switches offer an extensive port security suite, including ways to track IP to DHCP mapping, block spoofed ARP responses, and ensure that malicious actors can’t impersonate someone on the wired network.
This configuration is greatly simplified on the Mist portal. Enable these checkboxes with caution. Please read below for more details:
TRUSTED VS. UNTRUSTED PORTS:
When building up new port profiles within Mist you can select whether you want the port to be considered a “Trusted Port” or “Untrusted Port”.

By default, a trunk port is considered “trusted” while an access port is considered “untrusted.” This impacts how DHCP Snooping, ARP Inspection, and IP Source Guard operate. If you are going to enable the port security feature set, use caution placing statically configured devices or devices that would usually operate on a trunk port (access points, infrastructure services) on an untrusted port.
DHCP SNOOPING:
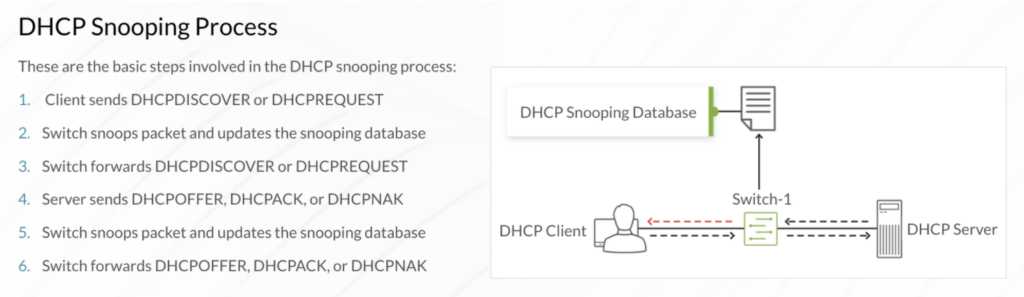
By default, the DHCP Snooping process will inspect all DHCP traffic on “untrusted” ports and use the information to build the snooping database.
DHCP DISCOVER / DHCP REQUEST will flow as expected on untrusted ports. However, DHCPOFFERs will be blocked on untrusted ports as they are assumed to be originating from rogue DHCP servers. If a customer has a DHCP server connected to an access port that is left to be untrusted by default, DHCP will not function.
The DHCP snooping database can be validated at the CLI using this command:
- show dhcp-security binding
ARP INSPECTION:
ARP Inspection further leverages the DHCP snooping database to block man-in-the-middle attacks.
ARP Inspection does this by:
- Intercepting ARP packets on untrusted ports and validating them against the DHCP snooping database.
- Checking if the source MAC address of the ARP packet matches a valid entry in the DHCP snooping database
- If no IP-MAC entry in the database corresponds to the information in the ARP packet, DAI drops the ARP packet
- If the IP address in the packet is invalid, DAI drops the ARP packet
Notice the reliance on the DHCP Snooping database entry. If a wired device has a static IP address and is connected to a port profile that is configured to be “untrusted” with ARP inspection configured it will not be able to communicate as it will not have an entry in the DHCP Snooping database.
You can validate this at the CLI using these commands:
- show dhcp-security binding
- show dhcp-security arp inspection statistics
- show log messages | match DAI
IP SOURCE GUARD:
When IP Source Guard is enabled all IP packets on untrusted ports are inspected and checked against the DHCP snooping database. The traffic will be discarded if the traffic does not match the binding (either the MAC or the IP address). This introduces the same considerations as ARP Inspection: If a wired device has a static IP address and is connected to a port profile that is configured to be “untrusted” it will not be able to communicate as it will not have an entry in the DHCP Snooping database.
Note that when combining IP source guard with 802.1X there are some restrictions. Three 802.1X user authentication modes exist, single supplicant, single-secure supplicant, or multiple supplicant. The single supplicant mode works with IP source guard, but single-secure and multiple supplicant modes do not.
Here are commands you can use to troubleshoot IP Source Guard:
- show dhcp-security binding
- show dhcp-security binding ip-source-guard