Application Policies (aka Security Policies) define who can access the Applications.
Once we have created the Networks, Applications and Steering Profiles, we can combine all this in the Application Policies to define who has access to the Applications (or who has not), the selected paths for the traffic in Overlay and Underlay and some other options.
Application Policies can be defined in 2 places: At Org Level or inside a WAN Edge Template (or Hub Profile).
If we define an Application Policy at the Org Level, we can then import it (i.e. use it) in one or multiple WAN Edge Templates (or Hub Profiles) following the model “define once, use multiple times”.
When an Application Policy is directly defined inside a WAN Edge Template (or Hub Profile), it will have local scope in that Template (or Hub Profile) only and cannot be re-used elsewhere.
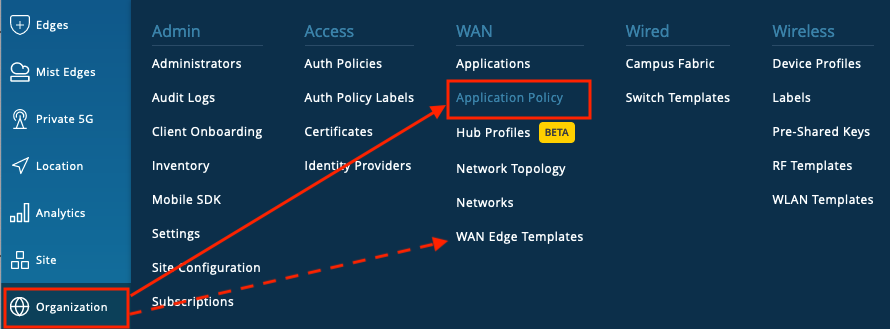
The Application Policies at Org level are defined in:
Go to Organization > Application Policy
While when the Application Policy is going to be defined in a WAN Edge Template or Hub Profile:
Go To Org > WAN Edge Template (or Hub Profile) > Select the Template (or Profile) > scroll down to Application Policies > select “Add Application Policy”.
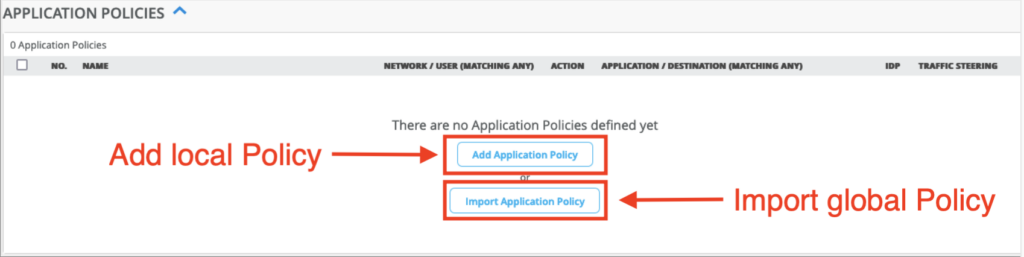
We can import a global Policy into the WAN Edge Template (or Hub Profile) by selecting the “Import Application Policy” option. The imported Policies are shown grayed out to differentiate from local Policies defined in the Template/Profile itself.
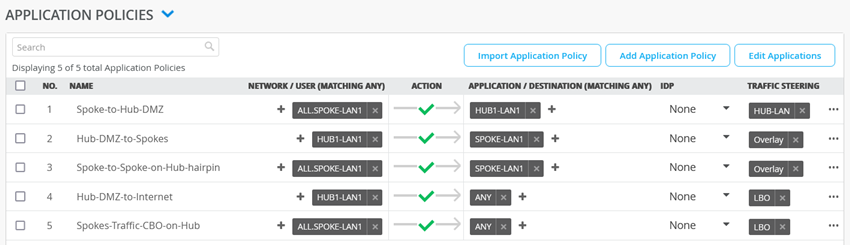
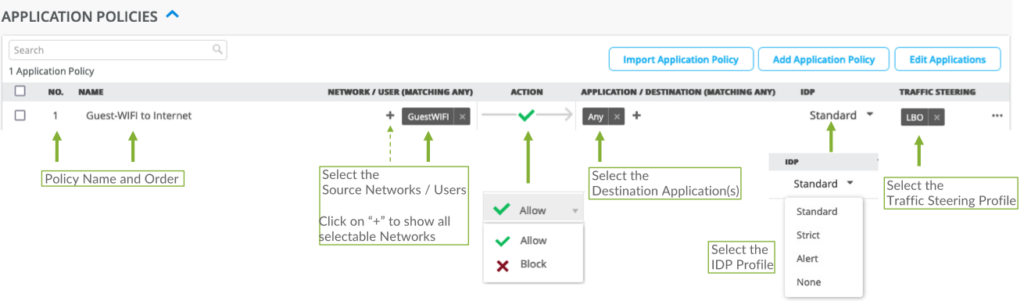
An Application Policy includes the following fields:
- The Name of the Policy
- Order number (NO.). The order matters as the Policies will be evaluated in that order.
The user can order and re-order the Policies inside the WAN Edge Template/Hub Profile so that they are used in the correct order. - Network/USER, select the source network/users that want to access the Applications.
- Action : Allow or Block, permitting or denying access.•Application / Destination: The list of
- Applications/destinations that the networks/users will have access to.
- Traffic Steering (Profile): Select the Traffic Steering Profile defining the path(s) this traffic should follow.
Unless we select a Traffic Steering Profile in the Policy, Mist will not deploy the Policy to the WAN Edge or Hub device. - IDP: Optionally we can select one of the IDP Profiles (Standard, Strict, Alert or by default None).
The Order Number and Traffic Steering are not available when the Policy is defined at the Org level as this is defined individually in each WAN Edge Template/Hub Profile where the Policy is used.
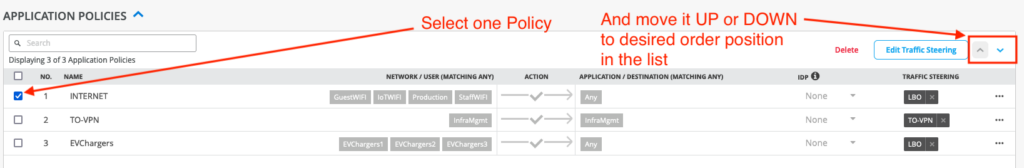
Ordering Policies: We can re-order the Policies used in a WAN Edge Template or Hub Profile at any time by selecting one Policy and using the UP/DOWN buttons until it is in the correct order. The UP/DOWN buttons are shown only when a Policy is selected.
Deleting a Policy: Similarly, we can select a Policy and the Delete button will appear. Press the Delete button to delete the selected Policy.
Using same IP Addresses/Prefixes in Networks and Applications
The Network/Users are the source networks/users of the traffic while the Applications are the destinations in the Policy. While we can use IP Addresses/Prefixes in both Networks and Applications, they are defined for different purposes, either as source or as destination in the Policy. This means that when the same IP Addresses/Prefixes (e.g. 192.168.200.0/24 for a Spoke LAN interface) will be used both as source in one Policy and as destination in another Policy to permit traffic originated from both ends (i.e. one Policy from Spoke LAN towards Hubs for example and another Policy from Hub to Spoke LAN), the same IP Address/Prefix will be defined in a Network and in an Application and we will need to create 2 Policies.